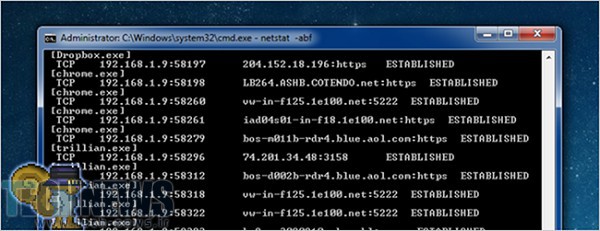
What Type Of Software Runs Secretly Behind Windows?
Have You Ever Noticed That Your Internet Speed Is Slowing Down? Or The Volume Of Your Internet While You Are Sure That Someone Is Not Connected To Your Internet Is Decreasing Day By Day And Strangely? …