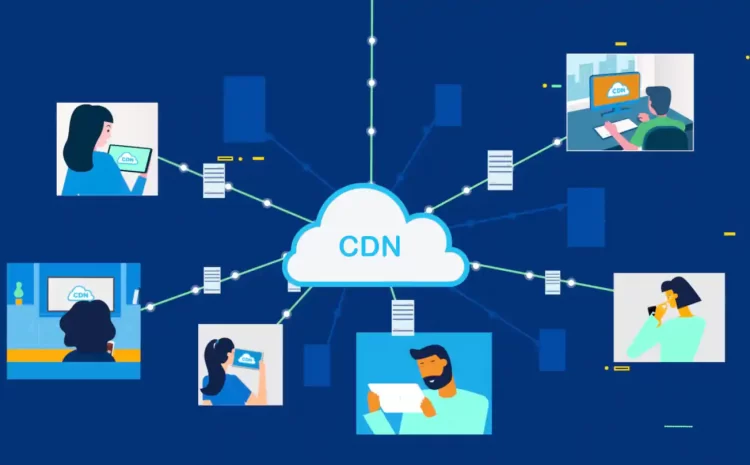
What is a Content Distribution Network or CDN?
A content distribution network (CDN) is a network of proxy servers located in different geographical areas, with their data centers. These networks aim to deliver services remotely to users, providing high accessibility and performance. Today,…