30 Questions to Ask Before Hiring a Network Security Expert
Cyber Security Is One Of The Most Important Areas Of Information Technology That Always Creates A Good Job Market For Experts Familiar With Information Security Topics. The More Demand There Is, The More Competition There Is.
Therefore, to get a job in cybersecurity, people must have a wide range of practical skills. While having the skills needed to get a career in cybersecurity is essential, one of the main parts of the story is the success of the job interview.
To be more precise, if you have the highest qualifications in this field but do not appear in a successful job interview, you will fail. Accordingly, in this article, we have compiled a list of the top cyber security job position answers and questions.
These questions give job seekers a clear view of the sample questions they may encounter in job interviews.
In addition, it helps human resource managers ask purposeful questions that are relevant to the job title of an information security expert. Let’s go to the questions and answers without margins.
1. What is cryptography?
- Encryption refers to the methods, tools, and solutions used to secure information and communications and is primarily intended to protect data from unauthorized access by third parties to sensitive data.
2. What is the difference between asymmetric and asymmetric encryption?
جدول In the table below, you can see the difference between these two patterns.
3. What is the difference between IDS and IPS?
- IDS Intrusion Detection System is an intrusion detection system and only detects intrusions, so the network administrator must carefully review the alerts and prevent intrusions. The IPS Intrusion Prevention System is an intrusion prevention system that takes steps to prevent intrusion.
4. Explain Confidentiality, Integrity, and Availability.
Confidentiality, integrity, and accessibility are the three main pillars of the security world on which information security policies are designed. Today, most organizations’ security models and doctrines are designed based on these principles.
- Confidentiality: Only licensed employees should read or view the information, and unauthorized persons should not access the data. If a person can gain access to systems by infiltrating the corporate network, the notification must be encrypted not to read its contents.
- Integrity: Indicates that an authorized person or persons have not edited the data. Integrity ensures that data is not corrupted or edited by unauthorized personnel. In addition, if an employee is trying to correct the data and the process is not successful, the data should restore to avoid unwanted breakdowns.
- Accessibility: Data should be available whenever the user needs it. Hardware maintenance, regular upgrades, backup and recovery of information, and network bottlenecks may violate the principle of accessibility.
5. What is a firewall, and why is it used?
- A firewall is a network-based security system that sits on the edge of networks or systems to monitor and control network traffic. Firewalls are used primarily to protect the system/network against viruses, worms, malware, etc. Firewalls can use to filter content or prevent access to unauthorized sites.
6. What is the difference between Vulnerability Assessment and Penetration Testing?
Vulnerability is finding a flaw in the target system or network. Here, the organization knows that the system/network has problems or weaknesses and wants to find and fix these problems.
Intrusion testing finds vulnerabilities (Vulnerabilities) in the target system or network. In this case, the organization wants to know if the security measures and solutions it has implemented to deal with cyber threats are correctly set up and if there is a way to hack the system/network out of its security experts?
7. What is a three-step achievement?
3 ‐ Way Handshake is a method used in TCP / IP-based networks to establish a connection between the host and the client. This communication mechanism is called three-step output because it is done in three steps as follows:
- The client sends an SYN message to the server and checks that the server is active or has open ports.
- The server sends an SYN-ACK message to the client if there are open ports.
- The client confirms this with another message, informing the server with an ACK confirmation message.
8. What response codes might receive from a web application?
Typically, you may receive the following answers when you plan to connect to a website or web application:
- 1xx: Information Reactions.
- 2xx: Successful operation.
- 3xx: Redirect.
- 4xx: Client-side error.
- 5xx: Server-side error.
Now let’s look at more specialized network-related security questions:
9. What is traceroute, and why is it used?
- Traceroute is a tool that shows the status of the path that a packet passes. More precisely, it lists all the points (primarily routers) that the package gives. Traceroute is used to check the stop or disconnect location to identify the point of failure. The above tool is used when it does not reach the destination.
10. What is the difference between HIDS and NIDS?
Host IDS HIDS and Network IDS Network NIDS are intrusion detection systems and have the same functionality. The only difference is that HIDS is configured on a specific host/device and controls the traffic of a particular machine and suspicious activities on the system. In contrast, NIDS operates on a network and controls the traffic of all network devices.
11. What are the steps for setting up network firewalls?
In general, security and networking experts perform the following steps:
- Username / Password: Change the default password of the firewall device.
- Remote management: Disable remote control; If you are on-site and do not need to configure it remotely.
- Port Forwarding: Preparing the correct port for applications to run smoothly and, for example, setting up ports correctly for the webserver or FTP server applications.
- DHCP Server: Installing a firewall on a network interferes with an existing DHCP server unless the DHCP firewall is disabled.
- Policies: You must have strong security policies and ensure that the firewall is configured correctly to execute those policies.
13. Explain SSL encryption
Secure Sockets Layer (SSL) is a standard security technology that creates encrypted connections between the web server and the browser. The above approach protects the confidential data and information exchanged in online transactions. The steps for building an SSL connection are as follows:
- A browser tries to connect to an SSL-protected web server.
- The web server sends a copy of its SSL certificate to the browser.
- The browser checks to see if the SSL certificate is trustworthy. The browser sends a message to the webserver to establish an encrypted connection if it is trusted.
- The web server sends a confirmation to start an SSL encrypted connection.
- An SSL encrypted connection is established between the browser and the webserver.
14. What should be done to secure the server?
Secure servers use the Secure Sockets Layer (SSL) protocol to encrypt and decrypt data and protect data against unauthorized eavesdropping. There are several ways to secure servers as follows:
- Step 1: Set a secure password for the root users and the administrator.
- Step 2: Define new users in the system. These users are responsible for managing the system.
- Step 3: Remove remote access from the default root/administrator accounts.
- Step 4: Configure firewall rules for remote access.
15. Explain data leakage
Data leakage is the intentional or unintentional transfer of data from within an organization to an unauthorized external destination. Disclosure of confidential information is not allowed in all countries, and the individual or organization faces many legal problems. Data leakage can be divided into the following three categories based on the occurrence model:
- Accidental Violation: An organization inadvertently sends data to an unauthorized person due to an error or mistake.
- Intentional breach: An organization intentionally provides data to another organization and receives money.
- System hacking: Hackers detect intruder vulnerabilities, infiltrate the system, and extract information.
Data leakage can prevent by using tools, software, and strategies known as DLPs called Data Leakage Prevention.
16. Name some common cyber attacks
- The most critical cyber-attacks that can negatively affect the performance of a system or network are Malware, Phishing, Password Attacks, DDoS, Man in the Middle ), Drive-By downloads, Malvertising, and Rogue Software.
17. What is a Brute Force attack, and how can you prevent it?
An all-inclusive search attack refers to repeated attempts and possible combinations to discover passwords or credentials. In most cases, pervasive search attacks occur when the software or web forms allow users to log in with authentication. There are several ways to prevent pervasive search attacks, some of which are as follows:
- Password size: You can set the minimum length for the password. The longer the password, the harder it is to find.
- Password complexity: Implementing pervasive search attacks becomes more difficult if you use different passwords. Using numeric passwords with memorable characters and uppercase and lowercase letters makes passwords more complex, making them difficult to crack.
- Limit login attempts: Specify a limit for unsuccessful login. Because the attack is an automated process, limited login attempts can make the attack unsuccessful. For example, you can set the login failure limits to 3. Therefore, when three consecutive login failures occur, restrict the user from logging in or sending an email.
18. What is a port scan?
Port scanning is a technique used to identify open ports and services in the host. Hackers use port scans to find information that is useful for exploiting vulnerabilities. However, network administrators also use the port scanning mechanism to verify network security policies. Standard port scanning techniques include the following:
- Ping Scan
- TCP Half-Open
- TCP Connect
- DP
- Stealth Scanning
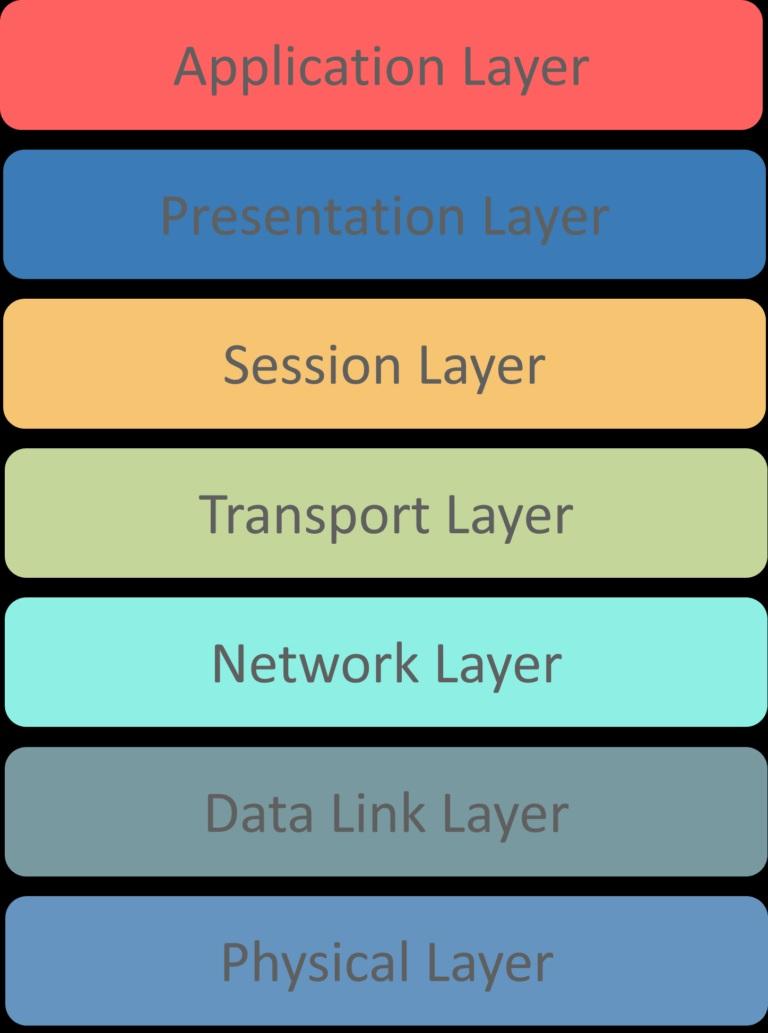
19. Name the different layers of the OSI model
OSI is a reference model that defines how applications and services on a network communicate. The model is formulated as a general guide so that vendors and developers active in hardware and software under the web have a clear view of the communication mechanisms. Figure 1 shows the layers of the OSI model. The function of each of these layers is as follows:
- The Physical layer: is responsible for transmitting digital data from sender to receiver through communication media.
- Datalink layer: Controls data transfer to/from the physical layer. It is also responsible for encrypting and decrypting data bits.
- Network layer: Responsible for transmitting packets and providing routing paths for network communications.
- The Transmission layer: is Responsible for network communication. In addition, it receives data from the top layer, transmits it to the network layer, and then ensures that the data is successfully delivered to the recipient.
- Session layer: Controls the communication between sender and receiver. Responsible for starting, ending, managing the session, and creating, maintaining, and synchronizing the interaction between sender and receiver.
- The Presentation layer: format the data and give it a proper structure, Instead of sending data in the form of datagrams or raw packets.
- Application layer: Provides the interface between applications and the network, focuses on process-to-process communications, and creates a communication interface.
figure 1
20. How much do you know about risk, vulnerability, and threats in the network?
A brief explanation of each of the above concepts is as follows:
- Threat: Refers to a person who can harm a system or organization.
- Vulnerability: A weakness in a system that a potential hacker can exploit.
- Risk means that there is a possibility of vulnerability in the infrastructure so that a hacker may detect it and use it to infiltrate the infrastructure.
21. How can identity theft be prevented?
In general, several steps can take to prevent identity theft. These actions are as follows:
- Use a unique and robust password.
- Avoid sharing confidential information online, especially on social networks.
- Buy from well-known and trusted websites.
- Use the latest version of browsers.
- Beware of unwanted installation of malware and advanced spyware.
- Use specialized security solutions to protect your financial data.
- Constantly update your system and software.
22. What are the differences between black, white, and gray hat hackers?
- Black hat hackers are known for their extensive hacking knowledge into computer networks. These hackers exploit their skills to steal information or use a hacked system. They can write malware to be used to access these systems.
- White hat hackers use their knowledge for exemplary purposes, and for this reason, they are also called ethical hackers. Companies mostly hire them as security experts to find and fix vulnerabilities and security holes in systems.
- Gray hat hackers are the boundary between white and black hat hackers. They look for network vulnerabilities without notice or permission and report them to the owner. Unlike black hat hackers, they do not exploit the vulnerabilities found.
23. How often should we do Patch Management?
- The Patch management should do it as soon as it is published. For Windows, it should be applied to all machines for up to a month after the patch is released. This rule also applies to network devices and should be installed as soon as the patches are released.
24. How to reset password-protected BIOS configuration?
- Because the BIOS is booted before the operating system, it uses its mechanisms to store the settings. A simple way to reset is to remove the CMOS battery so that the power of the settings storage memory is cut off, and everything is reset to factory defaults.
25. Explain the MITM attack and how to prevent it
- Man-In-The-Middle (MITM) is an attack vector in which a hacker puts himself between a source and destination communication channel and steals information. Suppose the two sides, A and B, are in contact, and the hacker enters into this connection. He forges their identity from side B to side A and sides A to side B to eavesdrop on the information. It can then send data from either party to another and steal information simultaneously. While the two parties think they are in direct contact, the hacker establishes their relationship. To combat this attack vector, you must use VPNs, strong WEP / WPA encryption to secure communications, intrusion detection systems, and public key-based authentication.
26. Explain the DDOS attack and how to prevent it
One of the constant questions is about job interviews. Distributed Denial of Service (DDoS) Denial of Service is a cyber attack that prevents servers from serving users. DDOS attacks can be classified into two groups:
- Flooding Attacks: The hacker sends a tremendous amount of traffic to the server to not manage this volume of requests. Therefore, it stops providing services. This type of attack is usually performed using automated programs that continuously send packets to the server.
- Crash Attacks: Hackers use a bug in the server to disable the system.
The following strategies can use to counter DDoS attacks:
- Use content delivery networks equipped with Anti-DDOS tools.
- Set precise rules for firewalls and routers.
- Use intrusion detection and prevention tools and ensure they are installed in the right places on the network.
- Use the load balancing mechanism.
27. Explain the XSS attack and how to prevent it
XSS Cross-Site Scripting is a cyber attack that enables hackers to inject malicious client-side scripts into web pages. XSS can hijack meetings, steal cookies, change DOMs, execute remote code, corrupt servers, etc. The following solutions should use to deal with the above attacks:
- Validation of user inputs.
- Implement policies to avoid receiving any input from the user.
- Encrypt specific characters.
- Use of Anti-XSS services/tools.
- Apply HTML XSS filter.
28. What is ARP, and how does it work?
- The ARP Address Resolution Protocol is a protocol for mapping an IP address to a physical address to identify a local area network. When an incoming packet to a host machine on a local area network reaches a gateway, the gateway requests the ARP protocol to find the address of a physical host (IP address) that matches the address. In this case, the ARP cache is searched, and if the address is found, it is presented to be converted to the appropriate device depending on the proper length and format. If no entry is found for the IP address, ARP sends a request message in a specific form to all machines on the LAN to see if a device has the associated IP address.
29. What is port blocking in LAN?
- Port blocking restricts users’ access to services on a local network. It is done not to have access to resources by a specific node.
30. What is Button?
- A botnet consists of the two words Ro (bot) and (Net) work meaning robot and network, which in common terms refers to a vast network of robots. The person who manages this network is the leading bot (botMaster), which most sources use to describe botmaster. By this description, we must say that botnet refers to several devices connected to the Internet on which malware is installed and performs malicious tasks without the device owner’s knowledge. Sending spam, running a DDOS attack, or extracting passwords are part of these actions.