11 Effective Strategies to Secure Your Microservices Architecture
Secure Microservices has provided powerful capabilities in flexible software development. However, They Have Also Created A Wave Of Security Complications.
The sheer number of instances, containers, network requests, and real-time data in a microservices architecture makes adopting an efficient security strategy difficult.
Microservices and containers are easy to work with in a sandbox environment, but security issues emerge when applications enter the real world.
For this reason, we suggest you pay attention to the 11 security principles mentioned in this article before preparing containerized microservices.
Data and its security
Data security is critical. In a microservices system, data is stored in places that are frequently moved and accessed by different system parts. Therefore, when transferring or storing data, you must take the necessary precautions to protect it. Depending on your management platform, such as Google Cloud, there are different ways to protect your data.
TLS and Secure Sockets Layer (SSL) are industry standards for network security. Google has developed these open standards to maximize the efficiency of its cloud platform. It uses encryption methods, such as the TLS protocol, BoringSSL, and a Certificate Authority (CA).
Managing sensitive information such as passwords, tokens, and access keys is critical in microservices. Container management systems provide efficient features to development teams, including strict credentials monitoring. In addition, Google uses an issuing authority to authenticate communications between services.
These features use the principle of least privilege and provide unique access keys that are only active for a short period. As a result, the security information stays up-to-date, and if any part of the system is compromised, you can keep the system’s state dynamic. Despite microservices’ potential benefits, severe security problems arise if the above paradigm is used unprincipledly.
Common security challenges around microservices
The distributed nature of microservices creates certain complexities and security issues that development teams must address. Among the critical security challenges around microservices, the following should be mentioned:
- Expanding the dimensions of a hacker attack: The proliferation of communication interfaces in a microservice-based application makes services vulnerable to hacker attacks. Each API and communication channel creates a potential attack vector that developers must identify and fix.
- Lack of detailed log analysis: A microservices-based application has distributed stateless services developed through heterogeneous technologies. Hence, the reports do not have the same format or are not produced similarly. Also, these services may be scattered in different geographical locations and interact with each other.
To solve the problem of the lack of detailed report analysis, a centralized system for collecting pieces should be created so that security analysts can quickly analyze events that occur on different platforms and are related to each other. - Poor testing: Microservices developers can create, deploy, and manage services independently of each other. This means that they can finalize services without testing them, which can cause services infected with security vulnerabilities to be released.
One of the most significant advantages of microservice-based applications is the freedom to release different versions of the same service and the agility in doing things. However, removing without testing creates many security problems. - The complexity of the fault tolerance mechanism: The fault tolerance mechanism in a microservice-based application has a more complex approach than an integrated application. When the number of services connected through the network increases, the complexity increases, and the probability of errors increases.
If a microservice can’t deal with failures properly, it may cause the performance of a part of the application or even the entire application to fail and make it unstable.
Why do microservices require a different mindset?
Microservices broadly address security challenges based on traditional or integrated programming paradigms, but they have their challenges. The essential nature of microservices is based on decomposing an application into separate components.
In an integrated application, all features work internally and communicate. Considering that a microservice program’s members can interact with internal and external environments, monitoring and maintaining the security of this program model is not easy.
Challenges of maintaining security in a microservices architecture
In an integrated architecture, a single point of failure can disrupt an application’s performance. In the microservices architecture, application components operate separately from each other, so a security breach does not quickly affect the entire application.
However, you should still expect to face complex security challenges. A big challenge is that a service meets different types of attack vectors. When an application comprises dozens of other microservices, providing fine-grained control over various aspects of the application is challenging.
- The first challenge is that a microservice-based application can use ten containers; you have to monitor ten different components instead of a single component. This monitoring challenge is multiplied if the containers associated with the application change continuously.
- The second challenge is the unfamiliar environment in which the program will be deployed.
- Unlike the defined and unified security umbrella, a firewall provides for a single application; hyper-centric microservices applications have no clear boundary.
- The third challenge is authentication and access control. Given that it is difficult to assess the environment in which the software is deployed, it will be difficult to impose restrictions on the users who can access microservice applications. Also, users may not need access to every application component, so assigning permissions should be done carefully.
Eleven fundamental principles of securing microservices
There is no one-size-fits-all solution to protecting microservices applications, but you can improve their security by adopting specific strategies and properly configuring microservices.
Most companies welcome the opportunity to migrate to microservices because of their many benefits, such as faster deployment and increased independence in service development.
However, migrating from a monolithic architecture to a microservice architecture significantly changes the issue of monitoring and managing the application architecture.
1. Attention to security during the design
When you intend to secure applications based on a microservices architecture, you should not only consider applying security technologies. To be successful in this field, the development and operation teams must interact with each other and information security experts based on the principles of DoApps.
Only in this way can accurate information about properly implementing security processes and reducing security risks be obtained. This approach, known as DevSecOps, emphasizes that software development and operations teams should engage with security experts from the beginning of the design rather than consulting them after the production phase begins.
2. Protect data
Always use the best defense strategies to keep information safe. Use the HTTPS protocol to secure data in transit and encrypt data at rest. HTTPS protects the privacy and integrity of data sent over the Internet by encrypting the connection.
Additionally, you can use the Strict Transport Security HTTP response header to tell browsers only to access endpoints via the HTTPS protocol. To reduce the chance of unauthorized access, it is recommended that you encrypt the data before taking any action and do not decrypt it until you need it.
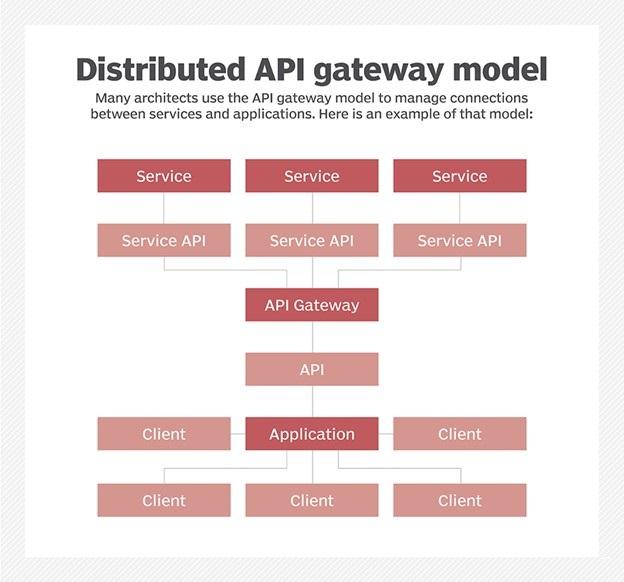
3. Use API gateway
In a well-designed microservices application, service users do not interact directly with microservices. Instead, they connect to an API gateway, a single entry point for traffic exchange, through which they communicate with various microservices.
API Gateway uses a token-based authentication mechanism to manage credentials to access services and how services interact with data. Since users do not have direct access to the services, they cannot abuse them. To improve security, placing the API Gateway behind a firewall is recommended to create a double layer of protection.
Also, ensure that all microservices used in a program have been developed based on security principles. Figure 1 shows how to define microservices and place them behind firewalls and API gateways.
figure 1
4. Implementation of rate limit mechanism
Rate limiting ensures an application accepts and processes most requests in a given period. The above mechanism prevents a hacker from accessing and abusing a program consisting of different services, each of which has its own credentials.
Also, rate limiting is a powerful strategy to deal with denial-of-service attacks and service inaccessibility. It would be best to implement rate limiting in the API gateway.
5. Use a defense-in-depth strategy
Defense in depth is a powerful security strategy in which an application consists of multiple layers of security controls. So, sens, live services are protected by different security layers. This potential attacker misuses one of the application’s microservices and cannot attack another microservice or other layers of the application.
The essential principle you should pay attention to is that you should not depend on a seemingly powerful security mechanism. Of all the security measures at your disposal to build security layers between microservices, use yourself and potential attackers.
For example, suppose you have previously deployed a robust network firewall. In that case, you should continue using other security mechanisms such as tokens, keep the addresses of sensitive microservices private, and implement a strong monitoring layer to detect anomalous behavior.
6. Separation
Separation is one of the leading and essential principles of microservices architecture. Each service must be developed, tested, deployed, scaled, and maintained independently of other services. This separation process must be in the database and also spread. Typically, each microservice has its own copy of the data. This isolation ensures that if one microservice is compromised, it cannot corrupt or expose another microservice’s data. Another advantage of the above method is that if a microservice crashes, it does not disrupt the performance of other microservices.
7. Securing should be done at the container level
Microservices applications often use containers for deployment. Containers host images that may be infected with security vulnerabilities. For this reason, they should be scanned regularly to ensure you have uncontaminated pictures. In addition, it is best to follow the minimum score principle to secure containers.
To do this, you must restrict resource access and manage resource usage. More precisely, access to a resource should only be granted on an as-needed basis. Additionally, you should not store confidential information in the container.
8. Keep an eye on everything
Developers and security staff must use specialized tools to constantly and automatically monitor microservices-based applications for potential threats. To this end, monitoring tools such as Prometheus and InfluxDB, which provide centralized monitoring, are available to development and security teams.
Also, automatic code scanning and continuous regulation updating are necessary. DevOps and security teams should have clearly defined policies to monitor the code and prevent unauthorized access to the application source code.
9. Implement DevSecOps
Ideally, carefully evaluate the security issue before adopting the architecture you plan to use to complete the project. If you consider the security challenges before coding, you can adequately assess the security problems and devise a suitable solution to solve them. This is where the idea of DevSecOps comes into play.
Since the microservices architecture has grown in the DevOps environment, it best supports DevSecOps. It is necessary to explain that in the DevSecOps environment, every specialist handles a security challenge while taking on the assigned responsibilities. DevSecOps culture implies that everyone in the organization is responsible for securing a product.
10. Protect the application by adopting multiple security policies
Providers like AWS take responsibility for security and firewalls in the cloud computing space. However, organizations should not rely solely on the cloud provider’s security measures. It would be best if you adopted a defense-in-depth strategy that creates multiple layers of security to prevent attacks.
The defense layer is the best way to protect the internal environment when interacting with external access. An important point that some developers overlook is that if any of your application’s components connect to a public network, they create a security hole. For example, containers usually use a public repository prone to cyberattacks.
The next layer of security is detection. Teams should plan a regular monitoring process and evaluate generated incident reports pointing to any potential application threats.
Docker Security Scanning and CoreOS Clair are the tools that can help in this field.
Access control, as another defensive barrier, can protect microservices-based applications. Although it can be complicated to implement, careful and correct assignment of management permissions ensures that only known users have access to the appropriate sections.
Automation is a good alternative if microservices security compliance requires a workforce. Fortunately, various security automation tools have been released for microservices that can monitor containers automatically.
11. Don’t forget to update
The key to application success is long-term protection, which requires hard work and constant updating. Updating programs is one of the most effective ways to deal with security threats. Threat modeling is a great way to assess an application’s current state and ensure it meets standards. It allows you to see threats and how they affect the application. The above approach gives you an accurate perspective on defending your application.
To achieve this level of application defense, you need to leverage a DevSecOps culture and defense-in-depth strategy and base your microservices application on that. By implementing these organizational changes, you will be prepared to face the threats microservices architecture faces.
last word
Many criteria should be considered when considering microservices security. These include the network architecture, the chosen container platform, and the data storage and access location.
Understanding how these criteria affect application security improves microservice management and security. Suppose specific policies address the security challenges of microservices, but don’t have. In that case, hidden and anonymous tips make it easy for hackers to break into various services and modules of the program.
Businesses cannot manually enforce policies to ensure security in an operational environment. In such a situation, they use tools like Project Calico, which has a network-oriented policy. Calico allows developers to define target resources and automate monitoring of these components. By adding or removing new items and communication, monitoring tools ensure that there will be no unknown security issues.
A mature container ecosystem should include security tools that use machine learning to discover and address emerging security issues. Typically, these tools integrate well with each other and provide a comprehensive view of the security of microservice applications.
They also prevent a wide range of cyber attacks by automatically analyzing large-scale data and identifying suspicious patterns. Development teams have access to machine learning-based security tools, such as Twistlock and Aqua Security, which can identify hidden vulnerabilities in microservice applications.
FAQ
What is mutual TLS (mTLS) and why is it important for microservices?
mTLS ensures both client and server authenticate each other using certificates, securing service‑to‑service communication.
How should secrets (like API keys) be handled in microservices?
Store secrets in a dedicated vault (e.g., HashiCorp Vault or AWS Key Vault), not in code or environment variables.
Why use an API gateway in microservices architecture?
An API gateway centralizes access control, rate limiting, validation, and routing, reducing the system’s attack surface.