Data-Driven Approach, The Way To Identify Cyber Threats To Organizations
As Organizations Around The World Were Forced To Telecommute Following The Outbreak Of The Coronavirus, Business Continuity Strategies Became More Important.
Data-Driven Approach: Most organizations have successfully provided the necessary infrastructure for telecommuting and maintaining production lines’ productivity. Most employees use personal devices during telecommuting and connect to an organization’s systems through vulnerable networks.
Therefore, cybersecurity risks in organizational environments are increasing. In addition, the technologies used to prepare the proper infrastructure for telecommuting have created new vulnerabilities and access points for attackers.
Organizations need a long-term strategic plan to balance business goals and cybersecurity risks to pursue their business success as they did before and allow organizations to defend their communications infrastructure while maintaining performance.
A data-driven information security plan has many benefits for businesses. Organizations can use data analysis and visualization solutions to make wise decisions and minimize security risks.
Data-Driven Approach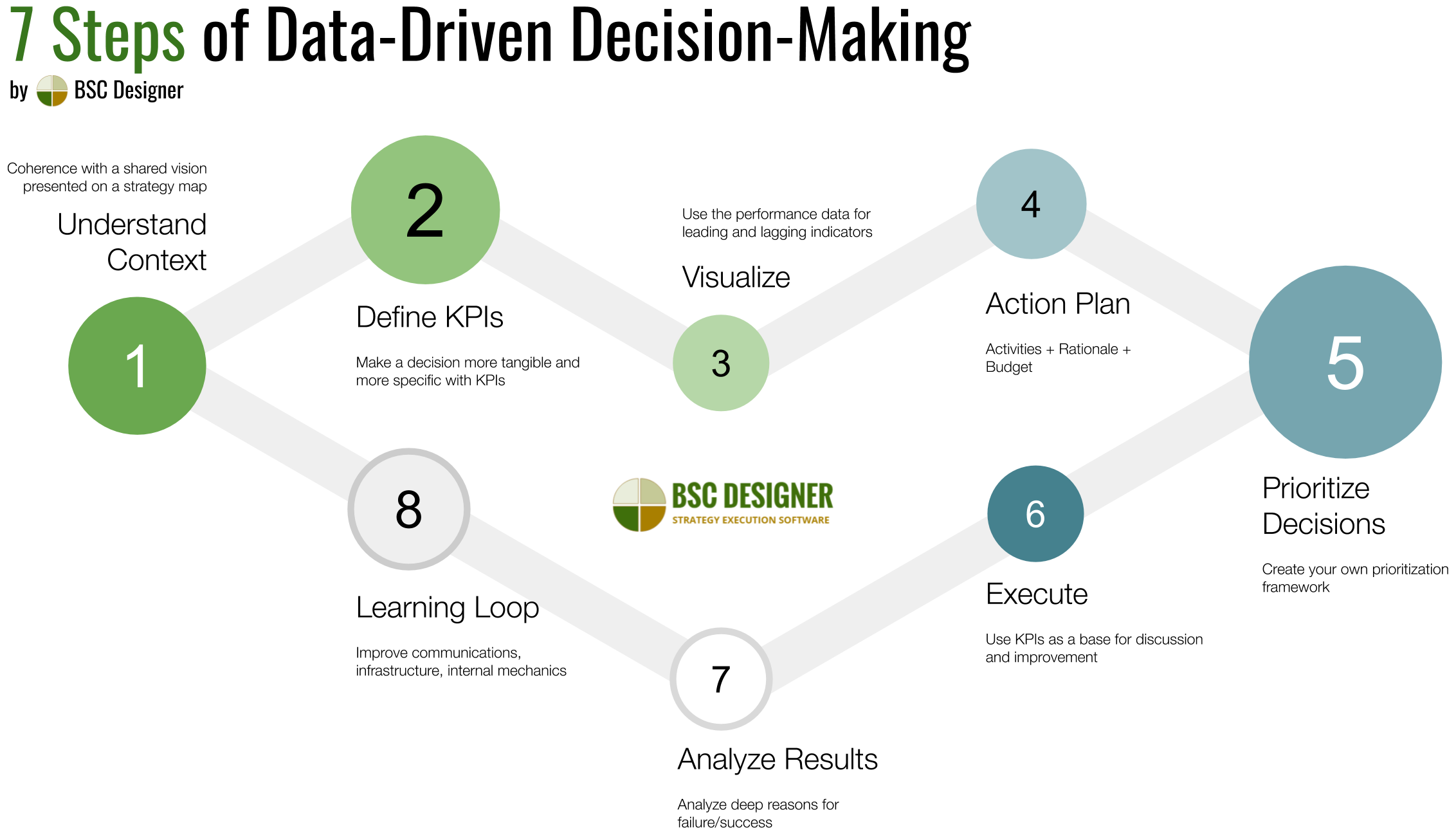
In addition, security managers can use the above solution to interact more constructively with the CEO and managers of other departments.
Accurate assessment of cybersecurity risks
When organizations face the challenge of implementing precise business strategic plans, maintaining the performance of various sectors, and managing uncertainty, they must simultaneously assess the risks posed by increased cybersecurity threats and address the following security policies.
In January 2021, the Verizon Institute published a report showing that last year, some companies made serious mistakes in properly configuring Internet-connected storage devices and cloud platforms, paving the way for hackers to enter the enterprise infrastructure.
Some companies believe that employees do not have the necessary productivity under telecommuting conditions and, therefore, move file servers or applications to a cloud environment.
Implementing super-centric solutions will increase productivity in the short term, but it poses many potential risks if the infrastructure is not configured correctly.
In part, the Verizon Institute report states that all companies need proper controls to reduce the risks of incorrect configuration, which cannot cause vulnerabilities in cloud servers.
The process of assessing cybersecurity risks requires cybersecurity professionals to first prepare a list of the information technology department’s assets and their sensitivity and vitality for the organization.
This assessment must determine the likelihood of abuse of a particular vulnerability and the potential impact of the accident due to that vulnerability.
Given the decentralized nature of the workforce, which may be due to the coronavirus outbreak, an organization’s employees may reside in different regions or even cities…
Cybersecurity managers can use business intelligence (BI) dashboards, which provide efficient solutions for analyzing business data.
The above dashboards can visualize data, assess data-driven risk, identify current trends, assess consequences, and be used as a communication tool.
Business intelligence tools designed to prepare, analyze, and create interactive images can identify a solution’s value and areas that require immediate analysis and best highlight potential risks.
Organize data and use imaging solutions to convey concepts better
In general, we describe an information security solution well when integrating statistical data systematically with the organization’s strategic plan. Such a solution can assess the risks based on a data-driven approach.
Infrastructure that prepares for telecommuting faces the dilemma of the large volumes of details and complexities associated with data collection that enters the enterprise network through wifi, personal devices, and Internet wifi.
In such situations, organizations’ security managers are faced with a large amount of heterogeneous data from which it is difficult to access useful information.
Cybersecurity experts should categorize, integrate, and manage this data to facilitate the analysis and conversion of information into comprehensible knowledge.
A detailed report on the cybersecurity situation and proposed solutions can be prepared and clearly explained to management.
Suppose the organization’s managers do not understand precisely why security solutions are essential for their business. In that case, attracting the necessary attention and consent to allocate funds to implement security solutions won’t be easy. As a result, the organization will be exposed to more security risks.
Organizations can use specialized software to analyze and visualize information from different sources, making it easier for them to aggregate and analyze heterogeneous datasets.
Histograms, bar graphs, scatter plots, and performance tools are the most efficient data visualization solutions for identifying important patterns and evaluating success.
These business intelligence tools can significantly help managers identify practical solutions. Security managers can use information designed to identify specific scenarios to help them manage the benefits of implementing an efficient solution and assess its applicability.
Are businesses exposed to cyber threats?
Security experts must first perform a permeability test. The penetration test provides an in-depth and comprehensive analysis of communication infrastructures.
In the above test, security experts try to view the infrastructure from a hacker’s perspective and directly and indirectly identify the paths that lead to system intrusion.
To do so, they may mimic attackers’ behavior in identifying and exploiting them or exploit vulnerabilities like a real hacker and end up with a detailed report to managers.
If the penetration test detects one of the following, it indicates that the organization is facing a serious security problem:
- If various potential high-risk vulnerabilities are identified in the network, they are likely caused by telecommuting employees connecting to the organization’s network through unsafe home Wi-FiWiFiorks.
- WiFiajor security patches have been installed on employees’ laptops for the past six months. When employees use personal equipment to perform business tasks, organizations have no control over the settings of these devices, and proper encryption or the latest operating system version may not be installed on laptops.
- Antiviruses are not configured to be updated automatically. Over time, antivirus programs installed on employees’ laptops become obsolete, and systems may become vulnerable to known malware attacks. Detected malware allows hackers to steal organizational information.
- The number of new accounts with high access levels may have been added to organizational groups. An attacker who accesses a vulnerable system using a configuration error can exploit only vulnerabilities accessible from within the network. Attackers may use this vulnerability to increase access levels and build high-level user accounts designed to steal corporate information.
- No multi-stage authentication mechanism is defined to access the organization’s critical systems. However, accounts on enterprise networks, especially those connected to essential applications and customer data, must use a multi-step authentication method. Attackers can use stolen information to access customer accounts or carry out phishing attacks.
- When was the last time employees were tested concerning a phishing attack? Employee performance against phishing can provide valuable information to the organization and determine whether more training is needed or whether it is time for relatively old security solutions to replace newer mechanisms.
An efficient cybersecurity dashboard can detect patterns in data and provide managers with a clear solution for risk assessment.
These dashboards allow security managers to communicate the results more accurately to the organization’s managers and tell them which areas need more investment.
Data-based decision-making saves a considerable amount of time and money
Intelligent dashboards give IT managers a clear vision for adjusting their information security plan to allow different metrics. These metrics can be a combination of statistical and operational information.
These metrics can be applied to a strategic data-driven security plan and integrated with business processes to accurately identify risks.
Once an accurate understanding of key performance indicators and key risk indicators affecting cybersecurity is achieved, the organization will evaluate the performance of the information security plan and gain practical and useful insights into vulnerabilities and threats.
Today, organizations increasingly depend on third-party companies (contractors) to enable software rental infrastructure, cloud services, and artificial intelligence solutions.
These services offer practical solutions for providing the infrastructure for telecommuting activities and allowing businesses to focus on business activities. However, they also increase organizational risk and create new risks for the organization.
For example, a chat service provider with access to data and systems beyond the required range can create dangerous conditions for the organization in the event of an error.
Cybersecurity experts must be able to describe the ultimate value of a cybersecurity solution through comprehensible data. Performance appraisal metrics such as the average installation time of security patches, the percentage of systems without antivirus software, and the number of emergency changes can all identify reasons for investing in cybersecurity solutions and different work priorities.
For example, a chat service provider with access to data and systems beyond the required range can create dangerous conditions for the organization in the event of an error.
Cybersecurity experts must be able to describe the ultimate value of a cybersecurity solution through comprehensible data.
Performance appraisal metrics such as the average installation time of security patches, the percentage of systems without antivirus software, and the number of emergency changes can all identify reasons for investing in cybersecurity solutions and different work priorities.
For example, a chat service provider with access to data and systems beyond the required range can create dangerous conditions for the organization in the event of an error.
Cybersecurity experts must be able to describe the ultimate value of a cybersecurity solution through comprehensible data.
Performance appraisal metrics such as the average installation time of security patches, the percentage of systems without antivirus software, and the number of emergency changes can all identify reasons for investing in cybersecurity solutions and different work priorities.
Digital transformation is not feasible without adhering to security policies!
An effective cybersecurity strategic plan requires rigorous processes. The evolution of digital transformation and the increase in telecommuting has led organizations to suddenly turn to tools that have long existed in the software world, some of which may be infected with vulnerabilities that have yet to be discovered.
Accordingly, it is better to evaluate the software and services based on cybersecurity experts before making them available to the organization’s employees.
Cybersecurity managers who have defined the right strategy to achieve new conditions should align the business’s overall goals concerning reducing the growing risks in cybersecurity.
A data-driven solution compatible with information security can enable organizations to use robust data analytics intelligently and data visualization in decision-making, align system and process implementations and reduce risks.
Security managers can use advanced business intelligence tools to aggregate data from various sources, identify key metrics and business objectives, and enhance collaboration between the organization and other IT partners.
Because cyber threats have become more stable and telecommuting employees have created serious vulnerabilities and risks for organizations, the need to analyze the data entering the organizational network has doubled.
Security managers can use advanced business intelligence tools to aggregate data from various sources, identify key metrics and business objectives, and enhance collaboration between the organization and other IT partners.
Because cyber threats have become more stable and telecommuting employees have created serious vulnerabilities and risks for organizations, the need to analyze the data entering the organizational network has doubled.
Security managers can use advanced business intelligence tools to aggregate data from various sources, identify key metrics and business objectives, and enhance collaboration between the organization and other IT partners.
Because cyber threats have become more stable and telecommuting employees have created serious vulnerabilities and risks for organizations, the need to analyze the data entering the organizational network has doubled.
