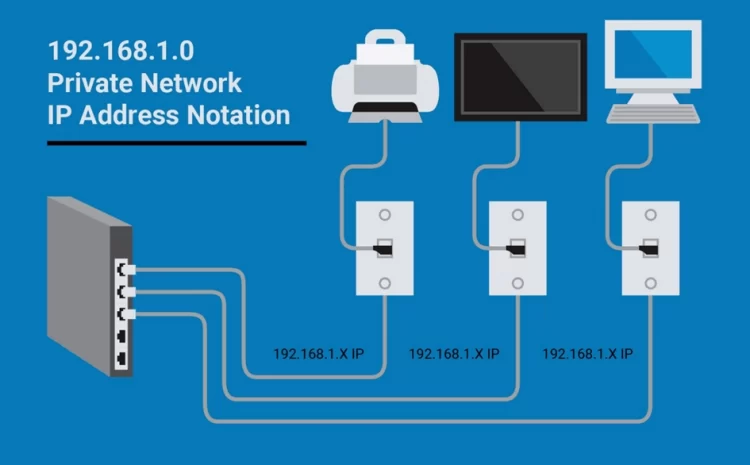
Every Thing About Network IP Classes And IP Division and Subnet Mask
The use of computer networks has become increasingly prosperous because most businesses are online, and now every organization, company, and business needs an all-around IP Classes technician to exchange all their information through him. Do…