How to Implement a Secure Network with IPsec Protocol
IPsec (Internet Protocol Security) refers to a Set of protocols Used To Secure And Encrypt Communications Between Devices On A Network.
IPsec Protocol: The above protocol manages the authentication and encryption of each packet. Based on this definition, IPsec is a set of protocols that can authenticate data and encrypt packets transmitted over a network.
What is the IPsec Protocol?
Internet Protocol Security is a network security protocol that consists of several protocols that aim to secure and encrypt data packets that are not intended to be transmitted over the IP protocol on the network and are not seen by unauthorized persons. IPSec strives to provide a high level of security for Internet Protocols.
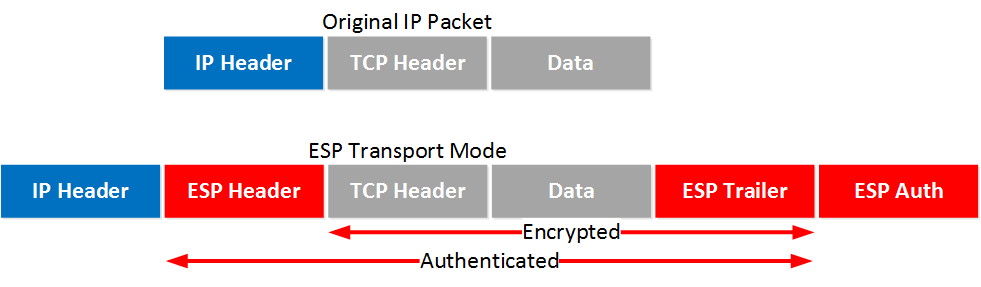
One of the most essential advantages of this protocol is that it works in Layer 3, unlike security protocols such as SSH, TLS, and SSL, which work in the top-level transfer layer. The IP protocol’s location at exactly the same layer makes it possible to protect Layer 4 protocols such as TCP and UDP and provide faster speeds when enabled.
Another advantage of IPsec over other security protocols, such as SSL, is that applications need not be designed based on the above protocol.
AH Protocol:
This protocol is used when the user needs strong authentication.
In summary, the AH protocol provides essential security services, including data integrity, authentication of the data source, and rejection of retransmitted packets.
This protocol uses HMAC technology to ensure the integrity of the transmitted data. It does this using a private key so that the packet data load and the immutable parts of the IP header look like the IP address.
After this process, the protocol adds its header. In the above protocol, the AH header is 24 bytes in size. The most important fields of the above protocol should be mentioned:
Following Header: This field specifies the following protocols. In tunnel mode, it encapsulates a complete IP diagram. This field is 4 bytes in size. When encapsulating a TCP datagram in transport mode, the value of this field is 6.
Payload length: Specifies the size of the data load.
Reserved: It is two bytes and is reserved.
Security Parameter Index: In most sources, the abbreviation SPI is used to refer to it, and it is 32 bits. This field consists of SA, which is used to open encapsulated packages.
Finally, 96 bits are used to maintain hash message authentication (HMAC), which protects the integrity of the transmitted data.
Note that the above protocol provided only the endpoints and the hidden key details, both created and checked using HMAC. It should be noted that the AH protocol does not manage network address translation. NAT is used for this purpose
If they do not use IV, Symmetric encryption algorithms are exposed to packet threats and inadvertently trigger a DoS attack. IV ensures that two different and encrypted pregnancies are used in this context.
The Next header field specifies the subsequent header.
The HMAC protocol, like the HA protocol, protects the integrity and authenticity of transmitted data. Only this head can give credit to the pregnant woman.
NAT has nothing to do with ESP, and it may still be part of IPSec and integrate with it. NAT-Traversal Addressing is a solution for encapsulating ESP packets with UDP packets.
The Next header field specifies the subsequent header. The HMAC protocol, like the HA protocol, protects the integrity and authenticity of transmitted data. Only this header can credit the pregnant woman.
NAT has nothing to do with ESP, and it may still be part of IPSec and integrate with it. NAT-Traversal Addressing is a solution for encapsulating ESP packets with UDP packets.
The Next header field specifies the subsequent header.
The HMAC protocol, like the HA protocol, protects the integrity and authenticity of transmitted data. Only this head can credit the pregnant woman. NAT has nothing to do with ESP, and it may still be part of IPSec and integrated with it. NAT-Traversal Addressing is a solution for encapsulating ESP packets with UDP packets.
Operating Modes
IPSEC can implement host-to-host mode and tunnel mode in the network as follows. In tunnel mode, all IP packets are encrypted and authenticated. They are then encapsulated in a new IP package with a new header.
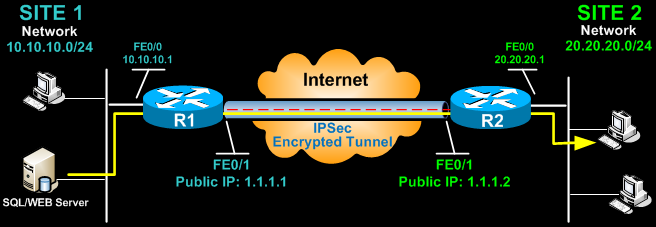
Tunnel mode is used to create a virtual private network in network-to-network communications (for example, between a router and a site link), host-to-network communications (such as remote user access), and host-to-host communications (such as private chat).
In transfer mode, only IP packets are sent encrypted. For example, the IP header may not change or be encrypted.
Then, IPsec implementations are typically performed by AH, ESP, and IKE V2. IPsec implementations on Unix-like operating systems, such as Solaris and Linux, include PF_KEY v2.
IPsec configuration
There are two locations for IPsec configuration in the Windows operating system. You can configure settings using the traditional IPsec Security Policy snap-in.
If all systems use newer systems, it is best to use Windows Defender Firewall with Advanced Security to configure IPsec policies.
WFAS is one of the most flexible solutions available. First, take a look at the IPsec policy console. We start here, as the options in this section allow us to draw the IPsec baseline as it interacts with the two endpoints.
Here are three different IPsec policies to assign to the machines we will specify in this console. Let’s take a brief look at each one, since the policy names aren’t prominent and may confuse you.
FAQ
What is IPsec used for?
IPsec encrypts and authenticates data sent between devices or networks, preventing eavesdropping and tampering.
Where is IPsec commonly applied?
In VPNs, site-to-site connections, secure remote access, and anywhere you need secure network tunnels.
What is a key step when setting up IPsec?
Choose strong encryption (e.g. AES), configure authentication properly, and apply consistent policies at both ends of the connection.