What Is a DMZ Network and What Is Its Use — Security and Network Isolation Explained
Working On The Internet And Interacting With Various Websites And Users Is Always Risky. In Other Words, Just As We Need To Take Care Of Ourselves And Our Belongings To Cross The Street, Traffic On The Internet Needs To Be Taken Care Of.
DMZ Network, Some caregivers are individuals. One of the most important things to remember is not to click on anonymous links on the Internet.
Another care is organizational, according to which an organization must protect its data from hackers. This is essential for organizations whose internal network is directly connected to the Internet.
Organizations use different methods to achieve information security. One of these methods is to use the DMZ network, but what is a DMZ network? This article will examine how the DMZ network mechanism works and enumerate its applications.
What is a DMZ network?
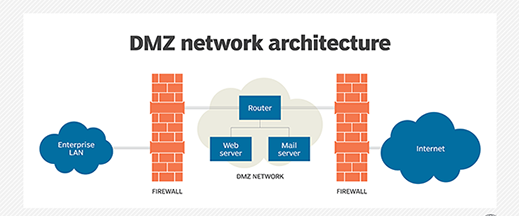
The DMZ network is, in short, a protective subnet that acts as a bridge between a secure internal network and an insecure network such as the Internet. In addition to maintaining internal network security, it may provide some internal network public services in the context of an external network.
Let’s move on with a concrete example to understand a DMZ network better. In science fiction movies about space and astronomy, you’ve probably seen astronauts get in and out of a spaceship.
To get out of the spacecraft when out of the Earth’s atmosphere, they must first enter a particular room that is separate from the spacecraft’s immediate environment, then seal the inside to adjust the atmospheric conditions and air pressure, and then open the outer outlet so that they can get out of the ship completely.
The DMZ valley network acts as the ship’s entry and exit chamber, providing a secure area connecting organizations’ internal networks to the Internet. The name of the DMZ network is derived from the term “Demilitarized Zone,” which is written as a headword.
DMZ, or civilian area, is used initially to define the border between two countries in geographical and political science, which has entered technology.
The most important use of the DMZ network is to add an extra layer of security to the core network, preventing hackers and attackers from infiltrating and accessing sensitive core network information.
In specialized terms, the DMZ network falls into the category of Perimeter networks, creating an environment to establish a connection between the approved and unapproved networks. The ultimate goal of the DMZ network is to provide the organization with access to unapproved networks, such as the Internet, by ensuring the security of the local private network.
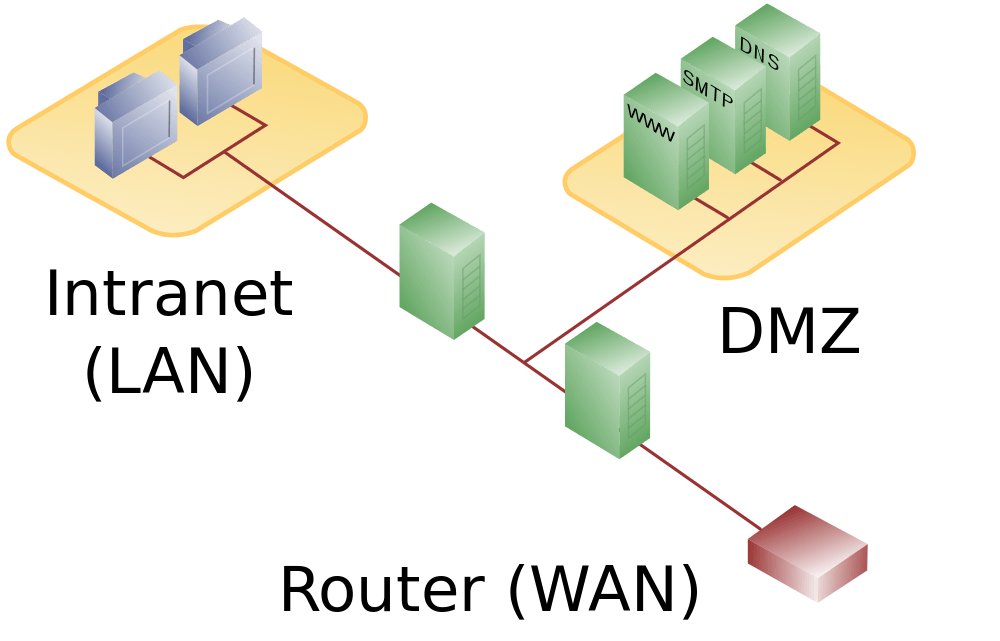
Organizations often put external services and resources, such as Domain Name System (DNS) servers, File Transfer Protocol (FTP), Email Services, Proxy, and Voice over Internet Protocol (VoIP) services, and Web servers under the DMZ network.
These servers and resources are set up in isolation. They have limited access to a local area network (LAN) that can be accessed via the Internet, but the internal LAN is inaccessible. This process ultimately results in hackers having less chance of infiltrating the internal network and accessing the organization’s data.
How does the DMZ network work?
Businesses that have a website to interact with their customers must make the web server available to them through the Internet to communicate through the website. Doing so risks the entire internal network of the organization.
Therefore, to avoid potential risks, the organization should ask hosting companies to host the organization’s website or public server with firewall protection, which will affect the website’s performance.
Therefore, hosting public servers available to users separately and in isolation on an independent network is better. This new isolated network is called the DMZ network.
The DMZ network creates a barrier between the Internet and the organization’s private network. Its isolated space has firewalls and security gates that monitor traffic between the DMZ and local networks.
BY DEFAULT, the DMZ server is equipped with another security gateway, protecting the gateway from incoming traffic from external networks such as the Internet.
In other words, the DMZ network is optimally operated between two firewalls; therefore, the DMZ network firewall ensures that another firewall checks incoming packets from the external network and then accesses the servers hosted on the DMZ network.
Thus, even if a hacker can circumvent the first firewall with complex actions, he must have access to the impenetrable DMZ services before damaging the organization’s internal network.
Even if a hacker can penetrate one of the DMZ network systems and take control of it, bypassing the first firewall, access to sensitive enterprise information is still impossible. Because an intrusion alert is sounded, the internal firewall and the local network will notify you of this intrusion.
Some organizations sometimes install proxies on the DMZ network to comply with rules such as HIPAA. This server enables them to monitor and record each user’s activity, easily centralize web content filtering, and ensure employees use the system to access it.
Advantages and disadvantages of DMZ network setup
Earlier, we discussed the DMZ network’s main advantage and how it creates an advanced security layer on the leading network. But, in addition to creating a barrier between the external and local networks, what other security features do these types of networks provide?
Other security benefits of the DMZ network include:
1—Access control ( Access Control): Businesses can provide users outside their network environment access to various Internet services. The DMZ network creates the conditions for accessing such services while also running the network segmentation process, making it difficult for unauthorized users to access the private network. On the other hand, as mentioned earlier, installing a proxy server in the DMZ network makes it possible to centralize internal traffic flow and facilitate traffic monitoring and recording.
2 – Prevent the implementation of vulnerability scanners and network detection operations: The existence of a DMZ network acts as a barrier between the Internet and the local area network, and this will prevent hackers from passing the first step to performing attacks, namely, network vulnerability detection. DMZ network servers are open to the public, but despite the built-in firewall, they do not allow hackers to scan inside the internal network. Even if a hacker enters a system in the DMZ network, he can still not perform the vulnerability scan successfully.
3. Prevent IP forgery attack: Hackers may impersonate an authenticated device by forging an IP address and infiltrating local network systems. The DMZ network can detect and stop authentication attempts, and some of its services can verify the legitimacy of IP addresses. Services on the DMZ network include DNS servers, FTP servers, email servers, and remailers.
Like everything else, the DMZ network has insignificant drawbacks compared to its benefits. Some of the disadvantages of the DMZ network can be classified into three categories:
1—Lack of internal protection: Although a diamond network prevents the penetration of external attacks, Employees and authenticated system users will also be able to access sensitive information.
2. False sense of security: As technology evolves, ways of infiltrating technology become the dark side of advanced technology. Therefore, even with the DMZ network set up, the servers are not always secure, and it is best to control all network environments in all sections periodically.
3—Users lack access to data stored on the private network server, inside the second firewall, and outside the DMZ network. Of course, to solve this problem, when you want to put the email database behind the security email firewall, you have to grant verified user access by assigning a username and password.
In practice, DMZ network setup has no particular disadvantages, but it requires deep knowledge, and not everyone is suitable for setting up a DMZ network. The incomplete and incorrect start-up of the diametric network will cause a fundamental problem. Because the exact boot process does not proceed, all system data may be lost or copied. Therefore, it is strongly recommended that you start with enough knowledge to enjoy the benefits of this network.
Proper operation of all DMZ network equipment and precise adjustment of switches are effective measures to reduce the network’s vulnerability.
Therefore, improper DMZ network setup can lead to information loss and increase the likelihood of being exposed to malicious attacks. If you try to infiltrate the system, you will not be alerted. The network administrator will think that everything is under control.
I will not examine the output. Do not forget that, in general, a diamond network can not work miracles against penetration. Still, it is one measure that can reduce the probability of infiltration and information leakage.
Design and structure of the DMZ network
DMZ network is an unlimited and open network that can be set up according to the number of firewalls and can use various designs. For example, you can start with one firewall and move to two or even several firewalls, thus significantly increasing network security.
A large part of today’s DMZ networks uses dual-wall architecture, as this type of design creates the conditions for it to be further developed and for more complex systems to be created.
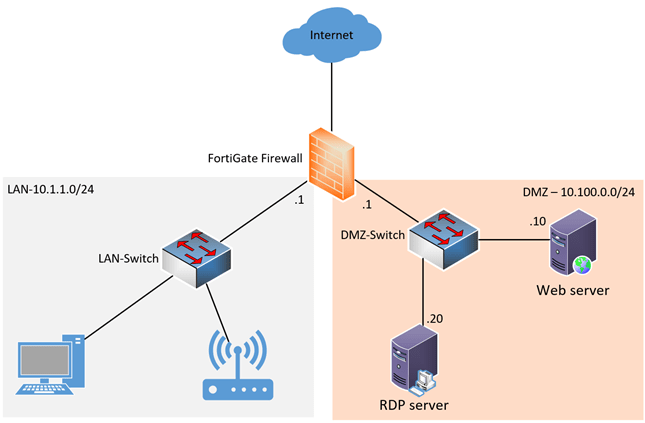
1. Single Firewall Network
A DMZ network with a firewall has three main components: a firewall, switches, and servers. In addition, a single-firewall DIAM network requires at least three network interfaces, and some structures may have more. A network interface is, in short, what connects digital equipment. These relationships may be software or hardware.
In a dual network with a firewall, the first “external network” interface connects the public Internet connection to the firewall. The second interface forms the “internal network.” The third interface connects to the diamond network. Various rules monitor and control network data traffic to access the diaspora and restrict the connection to the internal network.
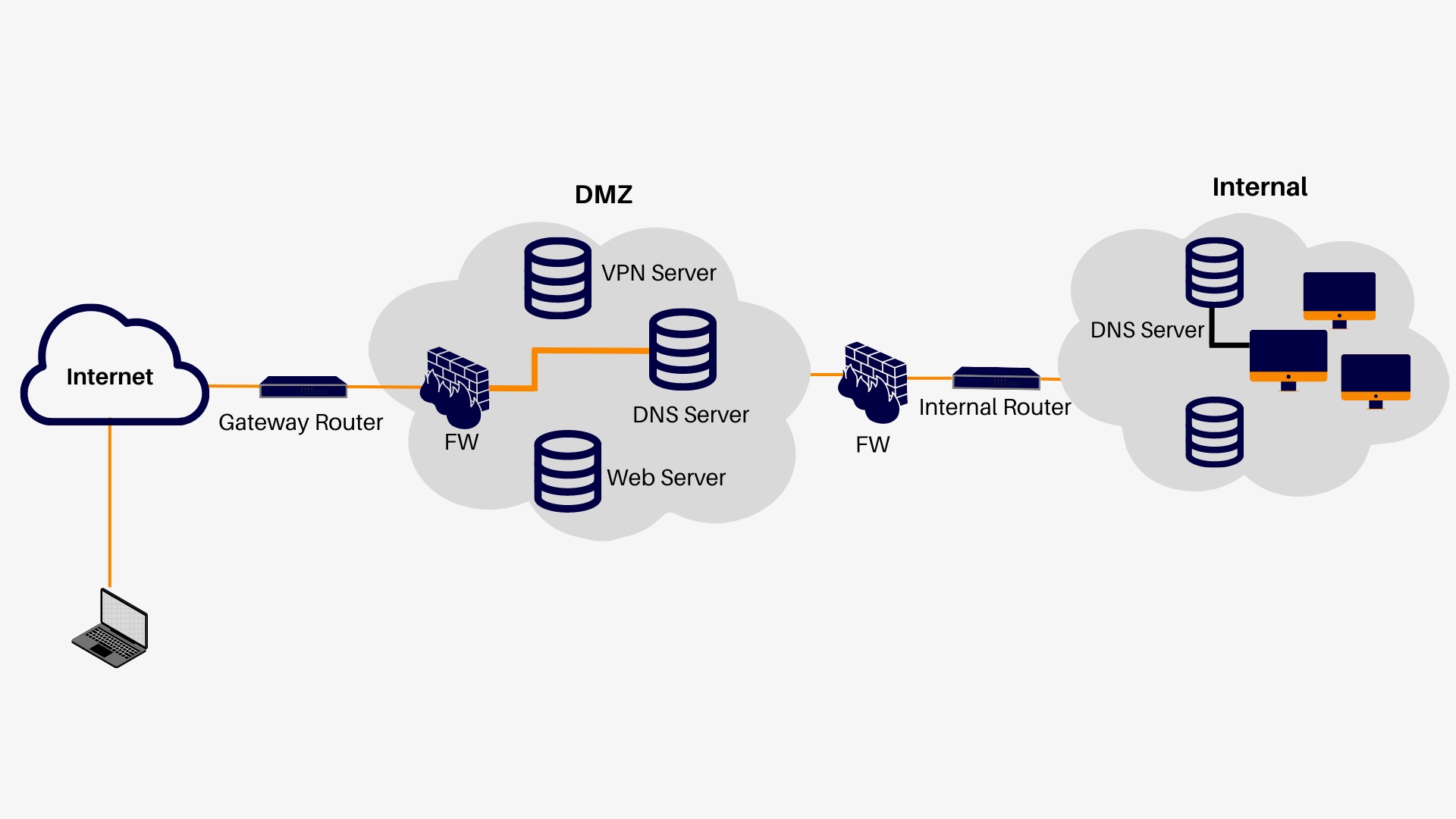
2-Dual firewall network
Establishing a diamond network between two firewalls is often a safer method.
The first firewall only allows external traffic to pass through the DMZ network, and the second firewall only allows traffic to pass through the DMZ to the internal network.
Therefore, a hacker must go through two firewalls to infiltrate the organization’s local network. According to this structure, the DMZ network with two firewalls also consists of three parts: firewalls, a dual network, and a local area network.
Organizations can also set up different security control stations to increase the safety factor in different network parts. In other words, the use of Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) within the Diamond Network will allow the blocking of any data traffic. It only provides access to the Hypertext Transfer Protocol ( HTTPS ) on the TCP layer and port 433.
In addition, these two models, which are classified based on the number of firewalls, can configure the DMZ network in terms of security and access level.
1. An anonymous DMZ network built for anonymous authentication is called an anonymous DMZ.
2- The DMZ network is built for access with authentication and known users.
For example, suppose you have a website on the Internet that is supposed to be accessible to everyone. In that case, you should be able to access it without authentication and place it on the public part of the DMZ network.
However, if your website is private and used by particular employees or customers, it can be made available as a gateway to log in with their username and password.
One significant application of an anonymous DMZ, which has doubled in popularity, is the creation of the Honeynet. A honeycomb is a network of several honeypots that trick hackers into identifying and trapping or diverting them from accessing their core resources.
Most Honeycomb computers are virtual machines mounted on a single physical device, through which intrusion detection systems and other surveillance systems collect all the hacker’s movements, techniques, and identities.
DMZ network application
Since the introduction of firewalls, the DMZ network has been one of the most comprehensive methods of protecting the information security of enterprise networks. The most critical application of the civilian area network is protecting sensitive organizational data, local area network systems, and the organization’s internal resources, which has a mechanism similar to the ditches around palaces and cities thousands of years ago.
Today, many businesses use virtual machines to separate their networks or specific applications from other systems. In addition, the growth of cloud spaces with faster services and lower costs has meant that businesses no longer need to set up internal servers.
On the other hand, most businesses use software as a service, or SaaS, which can also be referred to as “software leasing” and “cloud computing,” as a large part of their external infrastructure.
For example, a cloud service such as Microsoft Azure allows organizations to run applications on-premises (on-premises computing) and virtual private networks (VPNs) to take advantage of the hybrid approach and the DMZ network. It is located between the two.
This method is also proper when the outgoing traffic needs to be inspected or when the traffic between the on-premises data center and the virtual networks must be controlled.
In addition, the DMZ network addresses security risks in new technologies such as Internet of Things (IoT) devices and Operational Technology systems that make products smarter. Still, it has also been shown to increase the range of threats.
Operating systems (OT) equipment was not designed to counter or recover from cyber-attacks like IoT devices. As a result, operating system equipment has exposed organizations’ vital data and resources to risks.
Thus, the DMZ network divides the hazard network into hacker intrusions that can damage industrial infrastructure, which will reduce significantly.
Another application of the DMZ network could be for home networks, where computers and other devices connect to the Internet via a router and then configure a local area network. Some home routers provide DMZ hosting for the web.
This feature can be considered different from the DMZ subnet used in organizations. The modem’s DMZ host features indicate that a device on a home network outside the firewall will act as the DMZ network, while other home network devices will operate inside the firewall.
In some cases, the video game console acts as the host of the DMZ so that the firewall does not interfere with the execution of online games. On the other hand, the game console is a better choice for DMZ hosting because it does not store sensitive data compared to a PC.
Another application for the DMZ network that can be considered is its use in the Industrial Control System (ICS) as a solution to security risks. Industrial equipment, such as turbine engines or other industrial control systems, interacts fully with information technology to make the production environment intelligent and efficient. Still, the same interaction can also pose serious threats.
Although much operational or industrial technology (OT) equipment is connected to the Internet, it was not designed to manage hacker attacks and intrusions like IT devices. Thus, the DMZ network makes it more challenging to penetrate ransomware and other network threats between vulnerable IT systems and operating equipment by increasing network segmentation.
More straightforward examples of using a DMZ network include setting up email, fax, and web servers on email networks.
Email is an email service that users interact with via InteEmail, and the location of the email server on a secure network reduces the vulnerability of users’ personal information. However, to increase the security factor, it is recommended that you do not put the email database in the Diamond email and network it afterward, behind the firewall.
In general, the main application of the DMZ network is to create stop and inspection stations to control traffic within the network. These stations can be used according to the network’s needs in different scenarios and ways.
It may not be an absurd claim to say that information is one of the most valuable assets today, playing the role of currency between large corporations and on a larger scale between countries. Therefore, any effort to preserve information is an important step.
Usually, any company that stores sensitive information on its servers and interacts with users publicly via the Internet can use the DMZ network according to its needs.
The importance of this issue sometimes goes so far that some companies are legally required to set up their Diamond network. For example, medical and healthcare companies should design their systems to prevent users from leaking sensitive information.
What is a DMZ host?
DMZ hosting is slightly different from DMZ networking. As mentioned, the DMZ network is a separate and isolated space from the leading network used on a large scale.
However, the DMZ Host is a home router feature that can be enabled in modem settings. This feature lets you expose just one computer or device from your home network to the Internet.
The problem with dual router hosting is that if it becomes infected with a virus, it can infect other internal network devices since it interacts with them. Therefore, we emphasize that if you do not need to, do not use your home router’s DMZ capability in any way as usual.
Enabling DMZ hosting capabilities means that your home router opens all ports and responds to all pings and queries received from the Internet. Although your PC or server may have other firewall software, the router is the system’s front line of defense against attacks. As the router becomes a DMZ host, your system will lose an essential layer of security. The router’s firewall will not be able to block attacks.
Conclusion
The DMZ network is a buffer that acts as a protective layer. Examining the incoming and outgoing data can filter the incoming traffic to the internal network and prevent hackers from infiltrating and leaking information.
This space allows intrusion detection and systems to take the initiative in the face of attackers. Setting up a DMZ network requires expertise. Due to the high sensitivity of using a diamond network, you strongly recommend not creating a network without sufficient knowledge.
FAQ
What is a DMZ network in computer networking?
A DMZ (Demilitarized Zone) is a separate subnet that sits between an internal network and an untrusted external network to isolate public-facing services from sensitive internal resources.
Why do organizations use a DMZ network?
It allows external access to specific services (like web, email, or DNS servers) while keeping the internal network protected behind firewalls, reducing the risk of attackers reaching sensitive systems.
How does a DMZ improve network security?
By segmenting the network and placing firewalls between the internet, DMZ, and internal LAN, it restricts traffic flow and prevents direct access to critical internal systems if a public-facing service is compromised.