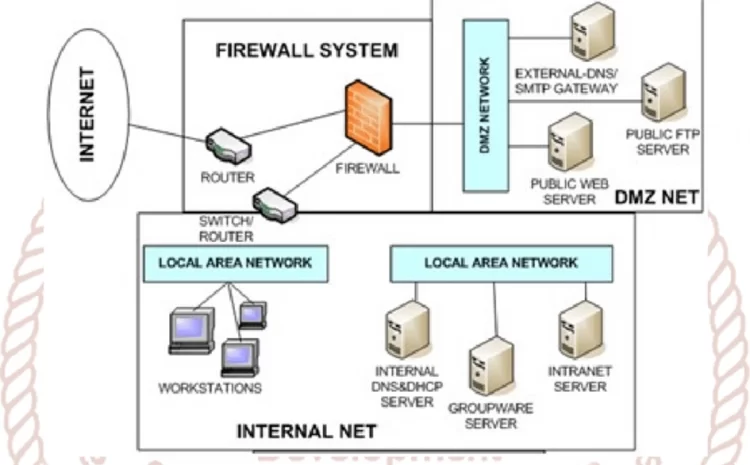
What is a DMZ (Demilitarized Zone) Network?
DMZ, which stands for Demilitarized Zone, indicates civilian networks in the network world. These networks, which are classified, play a big role in increasing the security of organizations. The DMZ network will maintain the security…