How Is Network Monitoring Done? A Clear and Practical Guide
Due To The Increasing Complexity And Extensive Nature Of Most Corporate Networks, Network Monitoring Is Increasingly Important For Many Organizations.
This is especially true when organizations move to a cloud or hybrid work environment.
In many cases, advanced network monitoring tools are also an essential part of the organization’s cybersecurity architecture, because they provide real-time, end-to-end visibility needed to identify early problems or attack indicators associated with an active cybersecurity event.
What is network monitoring?
Network monitoring is an IT process that continuously monitors and evaluates a computer network and its assets. A network monitoring system proactively identifies and corrects slow traffic or inadequate network components. In this way, it is always ensured that the integrity of the network is maintained.
Due to the increasing complexity and extensive nature of most corporate networks, network monitoring is essential for many organizations. This is especially true when organizations move to a cloud or hybrid work environment.
In many cases, advanced network monitoring tools are also an essential component of an organization’s cybersecurity architecture, because they provide real-time, end-to-end visibility needed to identify early problems or attack indicators associated with an active cybersecurity event.
Network monitoring tracks the health of a network in its hardware and software layers. Engineers use network monitoring to prevent and troubleshoot network outages and failures.
How does network monitoring work?
Networks allow transferring information between two systems, including between two computers or applications. The Open Systems Interconnection (OSI) model breaks down several functions that computer systems rely on to send and receive data.
For data to be sent to a network, it goes through each OSI component, using different protocols, starting from the physical layer and ending at the application layer. Network monitoring provides the possibility of viewing the various components of a network, and thus, engineers can identify and troubleshoot network problems at each layer.
Types of network monitoring protocols
Humans alone cannot monitor or analyze all activities within a network in real-time. Network monitoring protocols or related solutions automate this process and are critical for collecting, measuring, and reporting data and metrics that ensure optimal network performance.
There are two common examples of network monitoring protocols:
1) Simple Network Management Protocol (SNMP)
The most common protocol used for system status monitoring and network configuration. SNMP retrieves and organizes the data of all kinds of managed devices, such as network routers, switches, servers, printers, and other endpoints in a network, including a cloud network.
Each device’s management agent provides data and collects and stores it in the Management Information Base (MIB). SNMP transfers any information from the MIB to the network manager. The data is then displayed in a graphical user interface (GUI) and alerts the network administrator in case of any incident or problem that needs attention.
2) Internet Control Message Protocol (ICMP)
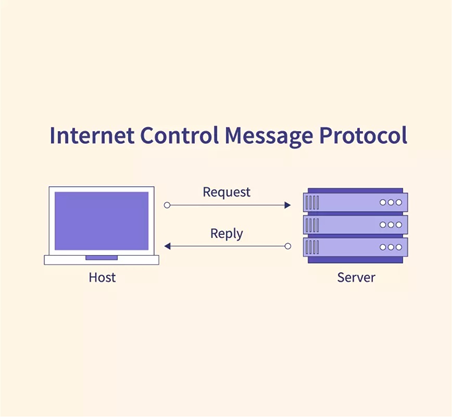
This protocol is used by network devices to send error messages, and it gives an error message if the host or router cannot be accessed.
Unlike SNMP, the ICMP protocol does not typically exchange data between devices. Instead, the ICMP error reporting protocol provides network administrators with a quick and direct understanding of the root cause of a network error.
How is network monitoring done?
You need to remove unnecessary load from the process for efficient network monitoring. For this purpose, you can pay attention to the following.
Monitoring essential network devices
Faulty devices affect network performance. This problem can be solved through early detection, which is why network device monitoring is so important. In ineffective network monitoring, the first step is identifying the devices and performance metrics related to monitoring.
Devices such as desktop computers and printers are not critical and do not require frequent monitoring; servers, routers, and switches perform essential business functions.
Optimizing the network monitoring interval
Both critical and non-essential devices require monitoring; For this reason, the second step is to set a time frame for regular monitoring. By selecting this interval, you can remove the extra load from network monitoring and reporting tools, and it will save your resource consumption.
Choosing the correct network protocol
After identifying the devices and creating monitoring intervals, choosing the appropriate network protocol is the next step. When monitoring a network and its instruments, a common good practice is to adopt a secure network management protocol that consumes the least bandwidth to minimize the impact on network performance.
SNMP is one of the accepted network protocols for managing and monitoring network elements. Most network devices and Linux servers support SNMP and CLI protocols, and Windows devices support the WMI protocol. Most network elements are associated with an SNMP agent.
This agent must only be activated and configured to communicate with the Network Management System (NMS).
Setting monitoring thresholds
Network failure can be costly. The reason for this is the weak approach to active enterprise network monitoring. The end user usually reports a network problem to the network monitoring team. The critical challenge in real-time network monitoring is to identify performance bottlenecks proactively.
This is where thresholds play a central role in a network monitoring program. Threshold limits vary from device to device and are based on the type of use in each business.
Introducing Bina network monitoring software
Bina network monitoring software is a product of Dana Pardaz company, which is considered an essential tool for the IT teams of any organization. With the facilities it provides, this software enables 24-hour monitoring of all services in your organization’s network.
By tracking any disturbances and problems in the network or its equipment, Bina sends warnings to the network authorities that have been determined in advance. Bina’s continuous and real-time reports help the IT team to have a clear and up-to-date picture of the quality level of the organization’s information technology services.
Bina network monitoring software supports over 600 devices manufactured by reliable brands such as Cisco, Mikrotik, Linux, and HP. In addition to providing practical and powerful features, this software is straightforward to use and can be used for small to large organizations.
Using this software, the monitoring workload can be distributed on several servers so that it does not affect the network performance. Bina supports standard and common protocols in this field, including WMI and SNMP versions 1 to 3.
In the following, you can familiarize yourself with some of the critical features of this software:
- Database monitoring
- Network equipment monitoring
- Server monitoring
- Monitoring email servers
- Website monitoring
- Monitoring virtual servers
- Temperature and humidity monitoring
- Bandwidth monitoring
- Monitoring network links
- Network equipment log monitoring
- Microsoft server log monitoring
FAQ
How is data collected in network monitoring?
Monitoring tools gather data through SNMP, ICMP, flow analysis, and log collection.
Why is network monitoring important?
It helps detect issues early, prevent downtime, and maintain network performance and security.
What metrics are commonly monitored?
Key metrics include bandwidth usage, latency, packet loss, CPU load, and device uptime.
