NAS Data: 7 Security Solutions You Should Use To Protect Your NAS Data
Network-attached storage (NAS) is a mechanism for storing and organizing files. This Centralized Storage Mechanism Allows Users And Client Devices To Store, Retrieve, And Organize Files And Documents.
Users on a local area network (LAN) can access shared storage through a standard Ethernet connection.
Typically, NAS devices are configured and managed through a browser-based tool. Each network-attached storage device is an independent node in the local network with its IP address.
NAS is a cost-effective solution
NAS is the primary data storage mechanism in small and large companies and organizations. In the above tool, storage space is provided to users as a single entity, which is vital for optimal information access. In addition, NAS can integrate with the cloud to make the archiving and backup process efficient.
NAS and storage area networks (SANs) provide organizations with comprehensive solutions to prevent data loss due to hardware failure. NAS is great for storing various data types, such as audio and video files, websites, text files, and documents. In addition, thanks to the different RAID architectures that can be implemented in NAS, it is possible to increase the speed of input and output operations and implement the network in a way that can withstand the failure of hard disks.
What network-attached storage is used for it?
NAS is used to improve interoperability and more effective and targeted data sharing. For example, in companies where some employees work remotely and need to access organizational resources remotely, NAS provides them with a comprehensive solution to access information.
In office environments, NAS connects to a wireless router, simplifying access to files from desktop computers or mobile devices. Organizations use a NAS environment as the infrastructure to implement a private cloud.
On a macro scale, NASs are based on a single architecture to implement a larger concept called a “Storage Area Network” (SAN). These widely used network equipment have at least two slots for installing hard disks or solid-state memories. Of course, single-cartridge products are also available in the market.
Still, due to the lack of support for recovery technology, they are not used in commercial applications and are more suitable for home users.
Enterprise products have at least four bays for hosting hard drives, offering more advanced features for storage management, compression, replication, and snapshots. More drives on a NAS allow organizations to install more disks and allow for more efficient RAID architectures, such as RAID 6.
Before the advent of NAS, companies had to configure and manage hundreds or even thousands of file servers and use solutions such as DAS for data storage, which had advantages and disadvantages.
However, thanks to the support of multi-terabyte capacities and the ability to host more disks, enterprise NASs, which are called scale-up NASs, can respond to heavy traffic workloads.
In addition, most NAS product manufacturers are partnering with cloud storage providers to allow customers to back up files and data more flexibly.
While NAS has many advantages, it is not without flaws. Network-attached storage only supports hard disks. When workloads increase, and many users send their requests to NAS, they face problems in responding to input and output operations, and response delay is one of them.
Newer systems use flash memory, which is faster and has excellent performance in data reading and writing. However, due to its high price, flash memory is not attractive to all companies. For this reason, some companies use hybrid approaches.
In this way, hard disks and flash memory are combined in NAS. They can simultaneously use the advantages of flash memory’s high speed and hard disks’ increased capacity. Regardless of the hardware architecture used to implement NAS, securing the data stored on the NAS is an essential issue for network experts.
NAS security
Securing the NAS and the data stored on it is one of the most critical issues to consider. Information encryption is one of the most efficient methods in this field. Encryption is one of the most effective ways to protect data hosted on network-attached storage.
If cybercriminals gain access to the drives or can eavesdrop on communication channels and monitor data packets, they will obtain unreadable data because a decryption key is needed to view the information correctly.
Encryption to keep data safe
Typically, network professionals use NAS encryption to prevent unauthorized persons from accessing confidential data in transit or stored on the NAS. This data may be bank card numbers, intellectual property, medical records, social security information, or personal data.
Information encryption is mandatory in some countries. For example, companies based in the European Union must use data encryption to comply with regulations such as GDPR or HIPAA.
Without encryption, data is stored and transmitted in clear text. In this case, any user with minimal technical knowledge can intercept communication channels and eavesdrop on information or, if there is physical access to the drives, can read sensitive information.
As we mentioned, a NAS device shares local network traffic with other devices and users. These systems can be desktop computers, printers, smartphones, tablets, and IoT devices. Therefore, information should not be provided to clients in plain text.
While encryption is a great way to protect data, NAS encryption can be complex and put sensitive data at risk if done incorrectly. Network administrators can save data simply and safely by following the seven simple strategies we will mention.
1. Determine what needs to be encrypted
The first thing to consider when using data encryption and decryption mechanisms is their impact on NAS and network performance. Sometimes, encryption slows down NAS performance.; As a result, responding to user requests takes time. The wait time depends on the hardware specifications of the NAS, how encryption is implemented, and whether the NASI depends on whether it uses the hardware acceleration feature.
In some cases, encryption negatively affects other NAS functions, such as data compression and replication, which are essential for optimal storage space utilization and data protection.
To solve this problem, you must first classify the data and encrypt only the sensitive data and the disclosure, which will cause legal issues. More precisely, the data to which the confidentiality principle applies are prioritized.
For example, if you have a variety of data on the NAS, classify the information based on the three criteria of “availability, confidentiality, and integrity” to efficiently identify sensitive, semi-sensitive, and regular data (Figure 1).
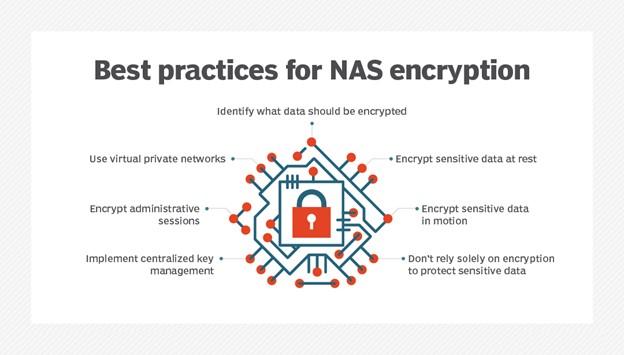
figure 1
2. Encrypt unused sensitive data
In the world of networking and storage, there are two information groups. The first group is data called “data at rest.” Data at rest stored on the NAS is the opposite of data sent to endpoints. This data may be archive files, documents, and financial reports or snapshots necessary to exist on the NAS and only used under certain circumstances.
Use NAS encryption algorithms to protect this data from unauthorized access. If the device is stolen or hackers manage to penetrate it due to a vulnerability in the NAS firmware, they will not be able to steal, view, or tamper with the data. Network and security experts recommend using cryptographic modules that conform to frameworks like NIST.
In addition, advanced encryption technologies such as 256-bit AES encryption are recommended. Note that both data groups and metadata must be encrypted.
3. Encrypt sensitive data in transit
Data in transit is exposed to various threats, such as eavesdropping and theft. Cybercriminals can gain access to confidential information transferred between a NAS device and other systems; Hence, encrypting the data exchanged between clients is essential. When employees work remotely, they need to access NAS and resources from personal plans to get things done. For this reason, it is required to encrypt any sensitive data entering or exiting the NAS.
However, NAS encryption does not guarantee that the network will be free of all threats. A careless employee can be as dangerous to an organization as a hacker. It is recommended to use industry-standard protocols such as Transport Layer Security (TLS) when encrypting data in transit and to close all unused ports on the NAS device. Also, all sensitive data should be backed up periodically.
4. Encryption of managers’ meetings
Typically, administrators from different departments of an organization have full access to NAS systems to configure and control storage equipment and related components and sometimes connect to the systems remotely.
Administrative access to NAS has its challenges. Most attacks are carried out through administrative accounts because hackers can access the NAS environment by intercepting a session’s data.
They can then change permissions, steal sensitive information, install malware on the NAS, or wipe data. Therefore, it is recommended that you encrypt administrative sessions to prevent data breaches and other attack vectors.
Some network experts do not consider whether the organization’s administrators connect to the NAS through application programming interfaces (APIs), command-line interfaces, or other client tools to be irrelevant. In all these cases, their sessions must be encrypted.
5. Use virtual private networks
A virtual private network defines an encrypted connection to the Internet, hiding the details of a session and adding a double layer of protection around the communication channel of a user’s system that intends to communicate remotely with NAS devices.
Since a virtual private network prevents the identity of online users from being revealed, hackers find it difficult to attack data or systems or even guess the contents of a session or the type of data.
It should be noted that virtual private networks have become especially important during the COVID-19 pandemic, as more people work from home and, in most cases, have to connect to corporate resources remotely.
6. Implementation of centralized key management
Most cryptographic algorithms rely on cryptographic keys to encrypt and decrypt data. As a result, key management is a critical issue to consider in your NAS encryption strategy. Cryptographic keys must be appropriately generated, distributed, stored, and erased promptly. A centralized key management system is needed to complete this process correctly.
A system that can keep the keys safe. Without such a system, hackers may intercept the keys and use them to decrypt information or impersonate users, access sensitive data through a valid user account, intercept information exchanged by users, or perform malicious activities.
In addition, the key management system must be selected based on business requirements and security policies to maintain data security.
7. Don’t rely on encryption alone to protect sensitive data
Encryption is one of the most important mechanisms to protect sensitive data, but it is not the only tool. Data protection requires several layers of security so that if a hacker succeeds in passing through one layer, they cannot easily access the data. For example, an employee may be authorized to access the personal data of the company’s customers.
When the user logs in and accesses the data, decryption is performed to access the data in plain text. Suppose a hacker succeeds in obtaining the user’s identity and authentication information. In that case, he can gain access to the network and view the available data as an organization employee, even if the data is encrypted.
Therefore, other tools, such as intrusion detection and prevention systems, must be used in addition to NAS data encryption algorithms.

