What Are The Threats Facing Cloud Infrastructure And Its Customers?
Over The Past Few Decades, We Have Witnessed Significant Developments In Industrial Processes.
Industrial processes involve chemical, physical, electrical, or mechanical methods to help produce better and more quality products. In addition, the planet’s growing population has forced industries to make on a large scale. For example, looking at the evolution of computer systems and the invention of transistors, we find that the size of computers has decreased significantly.
Transistors helped build large-scale integrated circuits (ICs). Smaller and faster computing devices have led to the emergence of various application software technologies, of which the cloud has been one of the most influential.
The cloud has an influential role in information technology and various industries. It has led to the emergence of multiple paradigms such as cloud and edge computing, which paved the way for the growth and emergence of other fields such as the Internet of Things.
However, an important point is the need to pay attention to security.
The current generation of computing requires intelligence because security experts cannot be expected to detect and deal with them in the face of the attack vectors that the superhuman infrastructure faces daily.
In addition, data processing for real-time applications requires the use of intelligent algorithms that are capable of gradual learning and rapid response.
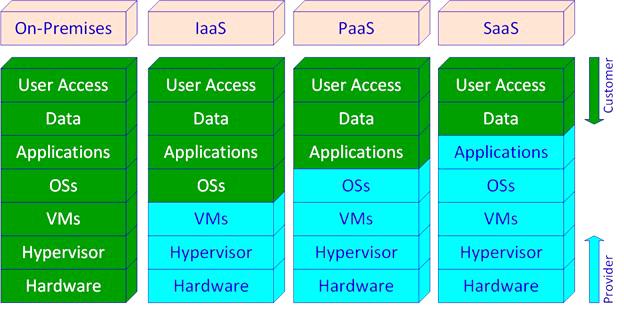
In this context, environmental intelligence as an emerging technology is entering the world of technology, and the purpose of its development is too intelligent the services that we use. There are many different cloud services today, but the essential paradigms in this area are shown in Figure 1.
The services provided in Figure 1 are as follows:
- Infrastructure as a Service (IaaS): These services provide the hardware and virtual machines needed to run our work environments. We must install operating systems, programs, and data on them and manage users’ access to resources.
- Platform as a Service (PaaS): These services provide the venue, i.e., hardware and operating system so that the user can install their applications directly on them.
- Software as a Service (SaaS): These services provide us with software to use the software online.
figure 1
Types of attacks around cloud computing
As noted, the growing use of cloud services has made consumers and service providers vulnerable to hacking. The first important point is that if we implement cloud computing or virtualization for internal or external applications, access to infrastructure through the Internet should not be direct. To be more precise, Internet traffic must first enter the Demilitarized Zone (DMZ) and then be provided to the organization’s employees and customers through the data center network. The above architecture is something like Figure 2.
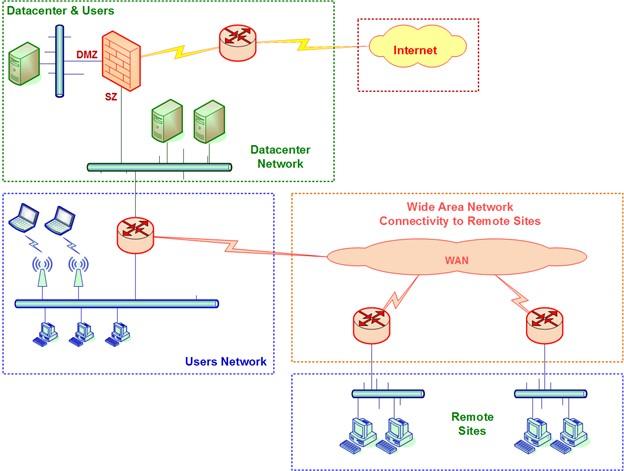
figure 2
The most critical issue that a cybersecurity expert should pay attention to is the complete breakdown of the IT environment or essential parts due to a cyber attack that causes the network and corporate services to be taken out of reach. Damages can be minor, such as hours of unemployment during office hours or disruption of access to widely used resources such as storage space.
In more severe cases, attacks cause customers to be denied access to services for hours or days, creating a tremendous economic necessity for companies active in cloud computing.
Another major threat to cloud computing is the loss of enterprise or customer data. Here we are in danger of destroying or stealing the organization’s data. There are two important goals when hackers decide to attack urban infrastructure; The first is to make the infrastructure inaccessible, and the second is to damage the data.
What is a cloud attack?
Before we look at the different vectors of attack on cloud infrastructure, we must first see what cloud cyber attack means.
Any cyberattack that targets online service provider platforms is called a cloud cyber attack. These platforms may provide different users storage space, computing power, or hosting services. Standard service platforms such as SaaS, IaaS, and PaaS models are exposed to these threats.
“Moving to the cloud has many benefits for companies, especially when most companies have adopted telecommuting as an organizational culture,” said McAfee. Cloud services have been well received by consumers due to the great flexibility and scalability, as there is the potential for significant cost savings depending on the existing infrastructure and needs.
“However, be aware that data in the cloud may be more vulnerable than data stored on dedicated corporate servers.”
Many cloud service providers promote security as a core advantage of their service, and companies focusing on providing storage solutions use basic security mechanisms to protect users’ data. However, you are mistaken if you think these security measures are all you need to protect your corporate data.
The popularity of telecommuting has posed new cyber security threats to both cloud and enterprise IT environments. The increasing use of remote work tools such as RDP (Remote Desktop Protocol) and data storage on cloud services has led hackers to use the communication channels used by organizations to connect to cloud services and the tools used by cloud service providers.
To continuously test to identify vulnerabilities hidden in them and through them to steal or manipulate data or cause hardware damage to components under the network. According to IBM, the incorrect server configuration is the cause of the hacking of cloud services in 86% of cases.
Knowledge of the correct deployment methods and the proper installation of security tools prevents the successful implementation of cyber attacks. Here are the six biggest security threats to cloud infrastructure that cloud service providers.
1. Incorrect configuration of cloud services
One of the biggest security threats to cloud infrastructure is easy to prevent. Incorrect cloud configuration occurs when a user or administrator fails to understand the cloud platform security settings. For example, an administrator may accidentally grant unlimited access to services to customers, causing unrelated programs and servers to communicate with each other.
Improper configuration is a big problem. A real example of incorrect configuration of cloud services was the Alteryx breach in 2017, when the online marketing company misrepresented the servers, exposing the data of millions of users. From 2018 to 2019, the number of records exposed by wrong cloud configuration increased by 80 percent, according to a study by the DivvyCloud Research Institute.
Incorrect configuration causes information to be disclosed and can lead to attacks such as brute-force search.
To solve this problem, you must use the Multi-Factor Authentication Mechanism (MFA) to reduce the risk of unauthorized access. If you do not use the multi-factor authentication mechanism and hackers succeed in finding a way to circumvent the settings, the chances of infiltrating the infrastructure increase. In addition, employees may encounter other attack vectors such as phishing.
Using the RDP mechanism, use the best security practices and minimum access, enable network-level authentication, and place RDP-enabled services behind the VPN. Deploying a cloud-based SIEM is another effective way to protect infrastructure. SIEM can detect suspicious communications.
2. Data loss
Cloud solution vendors try to make the two features “interoperability” and “information sharing” easy for customers. Sometimes cloud environments make it relatively easy for users to share data, so information sharing is done similarly with in-house teams and third parties.
As the workload increases, it is not unreasonable to expect employees to share sensitive organizational information with companies or third parties, Just like people on social media send the wrong messages to each other. The Synopsys 2021 Cloud Security Report states that 64% of cybersecurity experts describe data sharing and backup in the cloud as the leading cause of data leakage.
Data Loss refers to any process or event that results in the user corrupting, deleting, or unreadable information or application software. The above problem occurs when users or applications requesting the information cannot use all or part of the information. This problem is sometimes called data leakage. Static data and data transmitted over the network are equally exposed to this threat.
Data loss can occur for a variety of reasons, the most important of which are:
- Data corruption.
- Data is intentionally or unintentionally deleted or overwritten by a user or an attacker.
- Data that has been stolen due to network intrusion.
- The data storage media is physically damaged or stolen.
- The malware attack deletes one or more files.
Usually, data loss solutions can prevent by implementing backup data solutions and adding robust data access controls and security mechanisms to cloud-stored assets.
Recovering lost data is time-consuming and costly. Sometimes, these efforts are futile because a company needs to recreate or retrieve the data from backup files, which may suspend business for a significant period.
In addition, storing data over the cloud without regular backup is fraught with risks. For example, many hackers encrypt cloud storage to ask companies or cloud service providers for ransom to gain access to information.
3. Distributed service denial attack
“Distributed Denial of Service” (DDoS) attack means that hackers block users from accessing services or services hosted in cyberspace. The attack could be on a network, a server running multiple services or a specific service that provides cloud storage to other companies. DDoS attacks are implemented to get a benefit out of reach.
For example, hackers could use an Internet worm to execute a DDoS attack on a network to block communication lines or create multiple sessions and send heavy traffic to routers to make the server inaccessible.
DDoS attacks can disrupt the operation of a cloud service through traffic carried out by attacker-controlled devices (zombie equipment) and third-party servers that are inadvertently configured for replay attacks.
Another attack that surrounds cloud infrastructure is diverting traffic from the destination. This type of attack involves changing the Internet routers to redirect the direct traffic and direct it through the attacking network. Figure 3 shows how to implement this attack.
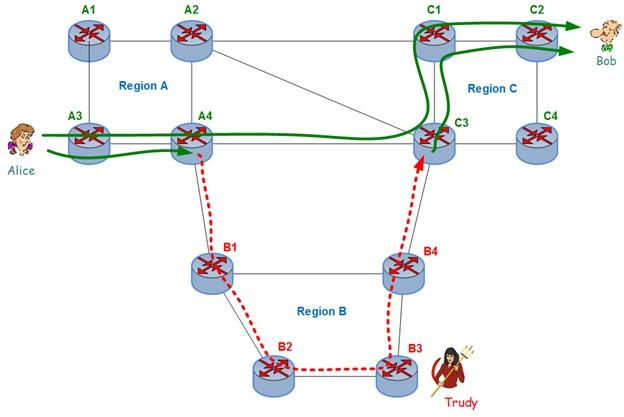
Figure 3
In Figure 3, we see that the traffic sent by Alice to Bob is monitored via the Trudy network.
Usually, when Alice sends traffic to Bob, she goes from Zone A to Zone B and gets to Bob. When an attack occurs, Trudy configures routers in Zone B to direct traffic to it. Traffic is sent from router A4 to B1. In zone B, traffic is routed to a point where traffic can record, copied, and transmitted to router C3 in zone C and the destination route.
Here, Bob and Alice are clients who send and receive information, while Trudeau is a hacker who tries to infiltrate the network, steal information, or divert the sending and receiving of data sent by Bob and Alice.
To divert the data that must be transferred from A4 to C3 so that the information is sent to B1 in region B, router B1 must tell router A4 that it has more priority than router A4 to see which is the best route to reach the destination via B1 and Not through C3. Hackers go to the Border Gate Protocol (BGP) to do this.
4. Attack the firewalls
Attacking firewalls occurs when an attacker tries to infiltrate a network. Network penetration is done in different ways. It can do by scanning the firewall for security breaches, such as ports that are left open to open a connection to the internal network. Another way is to disable the firewall services so that they can continue to operate only as routers.
Another component that cloud infrastructure administrators need to look out for and protect is the firewall management console. When the console is installed on an external device, make sure that it is not exposed to external networks such as the Internet and is protected by strong passwords.
5. Attack servers
Attacking corporate servers is the most dangerous attack that cloud service providers face because it not only compromises corporate data but also steals or deletes customer data. Servers face various episodes, the most important of which are hacking into servers, making them inaccessible, manipulating services running on them, or changing the settings of critical tools running on the server.
6. Attack on internal networks (LANs) within the organization
Data centers host various local area networks that connect internal networks. Hence, if a hacker manages to infiltrate a local network, he has a chance to enter other local networks.
Attacks on enterprise LANs can be carried out in different ways. However, there are two main ways to attack these networks. In the first case, the hacker is on the local network (employee or person whose account has been hacked).
In the second case, the attack is carried out from an external network. And in this way, the hacker may, as a customer, rent service from a cloud service provider and then look for vulnerabilities and backdoors in the software.
- Attack commonly used network equipment such as routers, switches, and storage devices. For example, attacking controls increase the data loss rate so that packets never reach their destination or there is a long delay. In general, LANs have the following attack vectors:
- Attack commonly used network protocols, such as spanning tree protocol (STP), ARP caches, etc.
- The attack aimed at analyzing, eavesdropping, and stealing information.
- Attack network routers and routing protocols.
- Attack switches that are incorrectly configured.
- Attack routing protocols to mislead routers and not send packets or parcels in the wrong directions.
- Attack on virtual equipment deployed in infrastructures such as routers or virtual switches