Why Isn’t It Easy To Implement Devsecops?
Devops Is A Set Of Methods, Processes, And Tools That Delivers Generated Values To End Customers Quickly And Consistently By Focusing On Communication, Collaboration, And Integration Between Software Development Teams And IT Operations.
However, Dups has entered various areas of the tech world, such as artificial intelligence and security. As the name of this solution is known, the two-way interface between application developers and infrastructure leaders.
Moving towards this strategy as an organizational approach is an influential approach due to the increase in the use of computational imagery and automation in important industries and infrastructures such as data centers.
The move was accelerated by the supply of Coburntis, a standard for synchronization of reservoirs. The architectural principles of Coburntis microservices, its declarative definitions, and unchangeable infrastructure are among the empowerment factors of DevOps and DevSecOps.
What is DevSecOps?
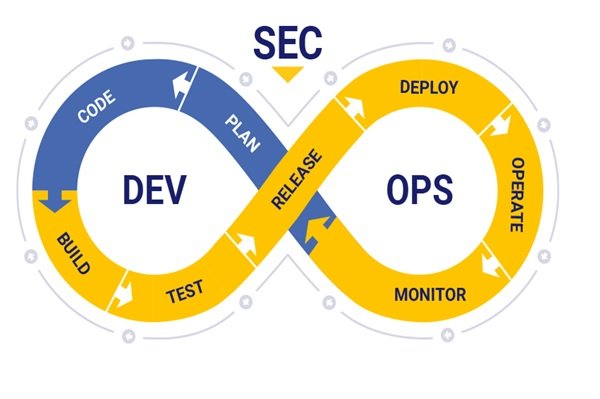
DevSecOps is the name of development, security, and operations. At DevSecops, everyone in an organization participates in security discussions to implement security decisions and measures in line with development and operations decisions and actions. In other words, DevSecOps seeks to carry out development and operations processes in the form of a two apps-based solution focused on security.
For example, in the discussion of software manufacturing, the goal is to follow the software development stage alongside the development of security. The above approach is the opposite of the situation where the focus is only on building and perfecting software and continuing to address security challenges.
What is devSecOps application?
However, the application of DevSecOps goes beyond the category of software manufacturing. As cyber threats grow increasingly spread, organizations and companies need to use a powerful framework like DevSecOps to promote infrastructure security. Companies and organizations active in the field of software manufacturers that use the DUPS framework should gradually move towards a more powerful DevSecOps framework.
Therefore, after improving the level of knowledge of individuals concerning security issues and sufficient awareness of safe development, the DevOps framework should be migrated to DevSecOps. DevSecOps looks at security as a key component in the development process.
For this reason, if you take steps according to this framework, security in the development process will be taken into consideration by all team members and shorten the process of making and supplying the product to the market, as less time is spent on identifying breaches and vulnerabilities.
How does DevSecOps work?
By following this framework, advanced automating across the software production line reduces errors, thus reducing attacks and system failures. Teams looking to incorporate security within the special framework can seamlessly and effortlessly use DevSecOps tools and processes. To clarify the content, let’s review a DevSecOps process:
The developer writes a code with a version control system (VCS). New changes and codes are recorded within the VCS. Another developer receives the previous step code from the VCS and checks the bugs and security weaknesses by analyzing the generated code. In the following, an environment is created through an infrastructure tool as an infrastructure-as-code.
A good example in this area is Chef. By creating this environment, the program will be deployed and the security configuration will be applied to the system. The above tool creates a laboratory environment allowing for program debugging.
An automated test set will be performed on the program that is installed.
This series of experiments is carried out on the elements of backhand and front end. In addition, application programming interfaces and elements are tested side by side.
If the program passes the tests successfully, it’s time to publish it in a real environment. The product that has been released is constantly monitored to check for any security flaws or defects that occur. Because software operations in the production environment are among the work of the designer team of applications, it is different from the traditional development method. When two apps are not used, operational teams face difficulties in reaching the applications service level agreement because it does not receive feedback from quality control professionals or security experts.
DevSecOps is created on a two apps basis and assures development teams that not only issues related to applications and infrastructure are aligned, but security risks will also be investigated. So members of a team can operationalize security throughout the entire software development cycle. The movement of software companies toward DevSecOps and the use of Coburntis as a common language in the life cycle of reservoirs (cloud) has many advantages.
Among these benefits should be mentioned as reducing operating costs due to a single and coherent infrastructure that increases productivity, reducing security costs, reducing operational risk, increasing developers’ productivity, and providing the implementation of digital transformation projects.
Why do DevSecOps fail?
Sometimes organizations fail to implement DevSecOps projects, which prevents failure by following the following points.
Failure to build learning culture: A report published by MacKenzie consulting firm shows that cultural issues are important issues in the field of digital transformation. Organizations focused on education and learning are gaining more success in devSecOps. Therefore, for devSecOps to succeed and improve the performance of organizations, the existence of a culture of learning and education is inevitable.
To achieve this goal, you need to devote certain financial and time resources to daily education and the term organizational culture, improving human resources skills, investing in the field of education to obtain training certificates.
Disregard for multipurpose training:
A survey conducted by the Linux Foundation in 2020 shows that open source and free software developers spend an average of 2.3 percent of their time improving code security and are running away from security issues. While maintaining security is one of the main priorities of software production, that’s why developers have a primary responsibility to reduce security vulnerabilities before the codes are finalized. While security experts should not be skilled coders, they should have a general understanding of coding methods, the ability to check the general formats of code so that they can identify vulnerabilities and incorrect configurations.
Disregard for business values transfer:
Any activity and efforts related to the implementation of DevSecOps plans must be consistent with the relevant key business objectives. DevSecOps is a big turnaround that requires different people of the organization to interact with each other. That’s why different people of the organization should be familiar with DevSecOps’ business values and understand the reasons for using it by conducting detailed assessments.
Fear of risk and failure:
As mentioned above, teams and organizations appear successful in implementing DevSecOps initiatives that have institutionalized the learning culture and are not afraid of failure. If an organization doesn’t make mistakes, doesn’t learn from its mistakes, and doesn’t try to fix flaws using trial and error methods, it won’t get the chance to be successful in implementing the DevSecOps framework. Teams should have the power to learn, identify weaknesses and correct them and improve their abilities in an environment based on transparency, security, and trust.
Distribution and separation of tools: Increasing the speed of transformation and digital innovation has accelerated the application of cloud-based solutions.
This growth has led to the formation of a diverse set of tools and applications that help organizations achieve devSecOps goals. However, the increasing production of various tools in most organizations has created a complex and unbroken environment. The dispersion of tools creates challenges in the field of productivity, monitoring, and control capability.
Nowadays, most organizations are looking for options for managing the chain of tools to prevent complexity and inefficiency. Of course, such issues are not limited to two-faced, and the security field faces various challenges due to the variety of tools. According to the researches, organizations usually face various challenges in evaluating security tools and familiarizing employees with all the tools in their organizational environment.
Misconception about DevSecOps:
One of the most common mistakes that some organizations have is that they think they have implemented DevSecOps in practice if they follow the principles of continuous integration and continuous delivery. You should note that DevSecOps is a solution that is implemented in collaboration with individuals, processes, and technologies.
Employee cooperation and principled integration of processes have an important impact on the implementation of this framework. If no attempt is made to implement a culture that conforms to the devSecOps principles, the implementation of DevSecOps projects will fail.
Last Word
Implementing DevSecOps is not a simple process. However, if done right and focused on its key capabilities, it will bring many benefits. In addition to increasing delivery speed, responsiveness to users, and competitive advantages, this framework helps to quickly, low-cost and effective elimination of vulnerabilities.