How to enable SSH on ESXi 7.0
This article will examine two methods to enable SSH on VMware ESXi 7.0. On ESXi, the SSH protocol is disabled by default, and we can enable SSH for the things we need. We should know that for the cases we need to access the core of ESXi, this is done through SSH.
-
Enable SSH through DCUI
Enter your ESXi server, click F2 and log in.
Go to the Troubleshooting options menu and enter it.
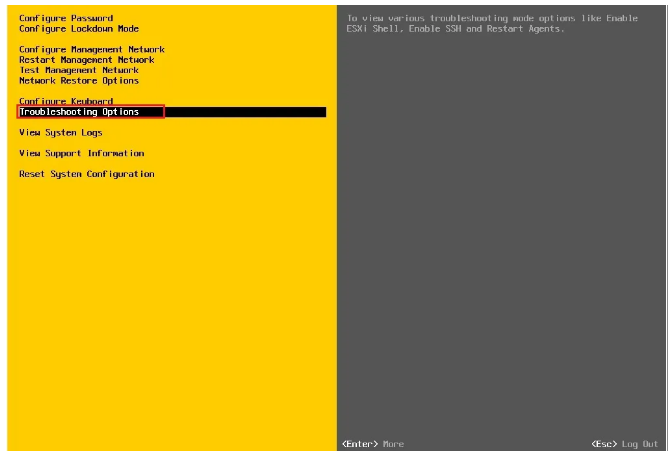
As you can see, SSH is in the Disable state, go to Enable and press Enter.
 At the end, hit ESC and return to the main menu.
At the end, hit ESC and return to the main menu.
-
Enable SSH using the Web Client
Log in to your ESXi using your account.
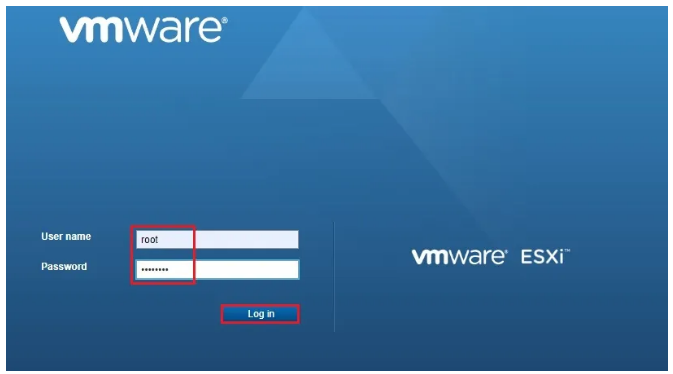
After logging in, follow the path as shown in the image.
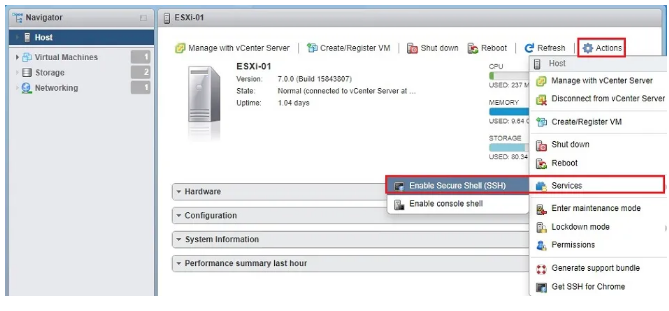
In the opened window, find the Services tab and enter it. Then find TSM-SSH and select it and click Start.
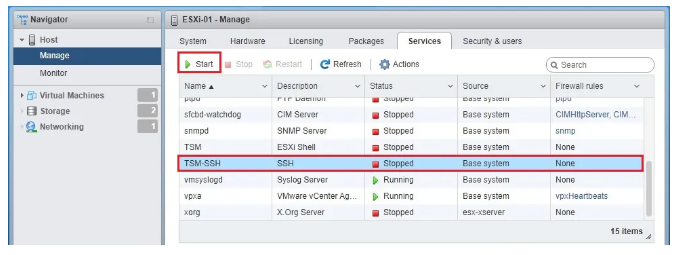
SSH protocol is now enabled on your ESXi host.
What Is SSH?
SSH, or Secure Shell Protocol, is a remote administration protocol that allows users to access, control, and modify their remote servers over the internet.
SSH service was created as a secure replacement for the unencrypted Telnet and uses cryptographic techniques to ensure that all communication to and from the remote server happens in an encrypted manner. It provides a mechanism for authenticating a remote user, transferring inputs from the client to the host, and relaying the output back to the client.
The example below shows a typical SSH prompt. Any Linux or macOS user can SSH into their remote server directly from the terminal window. Windows users can take advantage of SSH clients like Putty. You can execute shell commands in the same manner as you would if you were physically operating the remote computer.
How Does SSH Work
If you’re using Linux or Mac, then using SSH is very simple. If you use Windows, you must use an SSH client to open SSH connections. The most popular SSH client is PuTTY, which you can learn more about here.
For Mac and Linux users, head over to your terminal program and then follow the procedure below:
The SSH command consists of 3 distinct parts:
ssh {user}@{host}
The SSH key command instructs your system that you want to open an encrypted Secure Shell Connection. {user} represents the account you want to access. For example, you may want to access the root user, synonymous with the system administrator with complete rights to modify anything on the system. {host} refers to the computer you want to access. This can be an IP Address (e.g., 244.235.23.19) or a domain name.