What are brute force attacks and how should they be prevented?
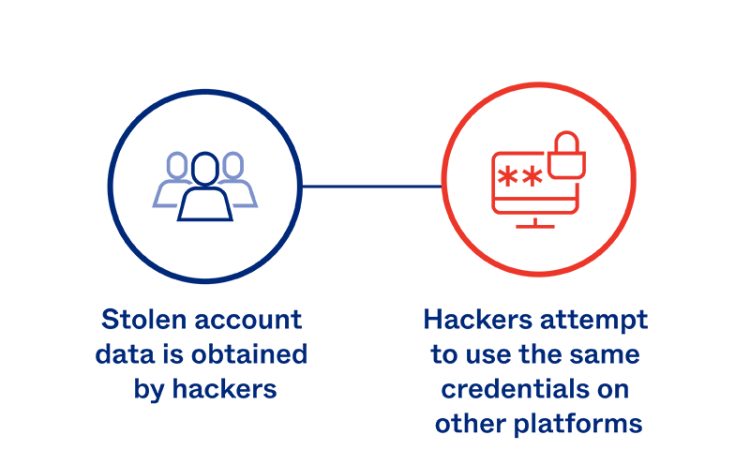
Brute Force attacks Unlike other cyber attacks such as DDoS and XSS attacks. Brute Force has nothing to do with the vulnerabilities on the website. In fact, users with weak usernames and passwords are targeted…