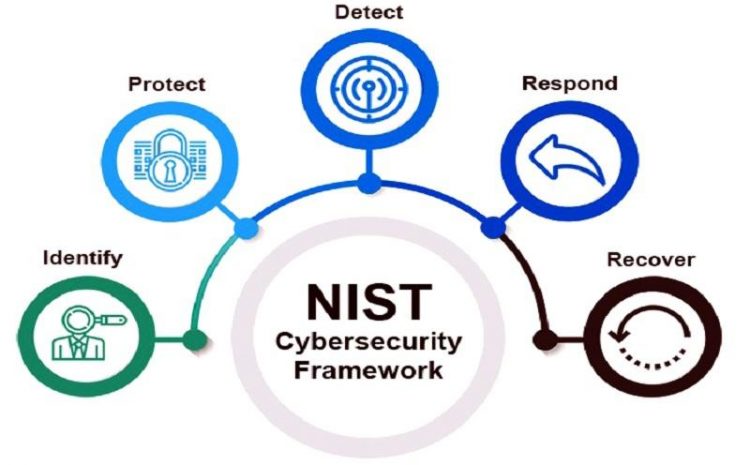
Security Plus Free Training: Penetration Testing Is Based On What Steps?
As A Penetration Tester, You Need To Make Sure Your Pentesting Process Is Similar To What A Hacker Would Do To Gain Access To Systems And Infrastructure. It is essential to understand because some security…