What is Secret Chat in Telegram?
Is secret chat or Telegram secret chat safe?
Telegram is a software that has more than 100 million users, according to the latest statistics in 2016. It is interesting to know that according to the Alexa website, the Russian compatriots of the creators of this software, namely Pavel Dorf and Nikolai Dorf, make up only 10% of the users of this messenger software. In 2015, the non-profit security firm Electronic Frontier Foundation gave the messaging section a score of 4 out of 7 and the secret chat section of the software a score of 7 out of 7.
What does Telegram say about the security of secret chat?
This application has announced on its official website that the security of Telegram’s secret chat is higher than usual and is designed for those who want to increase the privacy of their chats. All Secret chat messages use end-to-end encryption. This encryption method works in such a way that it only allows you and the recipient to read the messages, and no third party can break into it, Even Telegram itself.
In the secret chat section, messages cannot be forwarded,; when one party deletes a message, the message is also deleted for the other party. Another important feature of Telegram’s secret chat is that you can set a time for your chats so that all messages will be automatically deleted after the end of this time.
All secret chats exist only on the person’s device and not on the Telegram cloud, which means that even the person himself cannot access his secret chat through other devices. So as long as your device is safe, is your chat.
Can you be sure that the other party does not take a screenshot of the chat?
Some people think it is impossible to take a screenshot of a secret chat because Telegram sends a message to the other party, and he will know about it. However, Telegram has stated on its official website that there is no guarantee for this and that notifications may not be sent to the other party on some devices, including some Android devices and Windows Phones.
In any case, it is possible that by using methods, he bypassed sending the notification and took a picture of the chat page without the other party knowing. Also, never forget that the other person may take a picture of the chat screen with a camera or another phone; in this case, Telegram has nothing to do, So share your sensitive and confidential information only with people you trust.
In the continuation of this post, we will read the translation of an article in which a research group has tried to answer the question of whether the Telegram chat secret can be hacked.
Telegram stores encrypted messages in a plain text database.
In one of the noisiest recent works, Telegram software claimed that the security of this messenger is so high that if someone discovers the email address encrypted in this software, he will win a $200,000 prize. While being an interesting challenge for security experts, this claim misleads users because encrypting a text inside software is one thing and implementing encryption on chat is another.
The researchers of Zimperium company have researched the secret of Telegram chat. We read this research in the language of one of the experts:
After announcing this ad from Telegram, I decided to look closely at this software. I wanted to see if the text of encrypted messages can be read. This test was done on Android version 4.4.2.
Telegram claims to be a software that focuses on security, and its users can have personal and business encrypted chats. Ziprium experts proved that this claim is false, and 50 million Telegram users are at risk. Telegram’s previous encryption contest recognized breaking the protocol only at the time of encryption and transmission. This is not a good idea for two reasons:
In the real world, hackers don’t care about rules.
It was assumed that hackers would try to break the encryption in the middle, while weaknesses could be found in other protocols that would be more beneficial. (For example, GoToFail security weakness to bypass SSL encryption on iOS)
In the new encryption contest, Telegram claimed:
This time, the participants can not only check the traffic but also impersonate the Telegram server and use active attacks, increasing their abilities.
So I won’t try to break the encryption, but I will try to bypass it with an active attack on the phone. The best way to carry out this attack is to properly understand the anatomy of cyber attacks and the architecture of mobile devices. It didn’t take long after I installed Telegram to find the plaintext and encrypted messages I sent along with their database.
According to the Telegram site: Secret Chat is an encrypted person-to-person message that only the participants in this chat have the decryption key. Therefore, no person in Sumif can access the unencrypted text of the messages without access to one of the devices.
This statement took two years:
If the user does not have access to the device or a hacker has hacked it, how hard is it to recover the text of messages encrypted by Telegram?
Is the text of the messages encrypted on the device, and how?
It is easier to find a security weakness in the device and hack it with methods such as URL, PDF or MITM, and the like. Then increase access using Kernel Exploit and take control of the device.
If you are new to mobile device security, the following examples show how someone can remotely attack a device. These attacks are very convenient for government agencies like the NSA with enough resources, money, and time.
A – Client-side Vulnerability: Chrome exploit – Pwn6Own Autumn 6143
B – Kernel exploit – CVE-3453-6141 (a.k.a – TowelRoot)
At first, using Telegram Android software, I first created an encrypted message to see if it was stored somewhere unencrypted. I assumed that the messages were encrypted in memory or at least in the internal database. This assumption is not much for software with a security attitude.
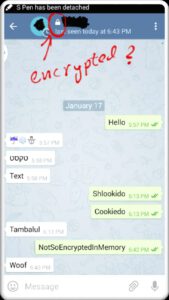
If you take a picture as an attacker, both people will be notified in the chat. Therefore, it can be understood that security and privacy are very important for Telegram. However, it is a bit wishful to assume that the attacker is taking a picture of the image instead of controlling the entire device.
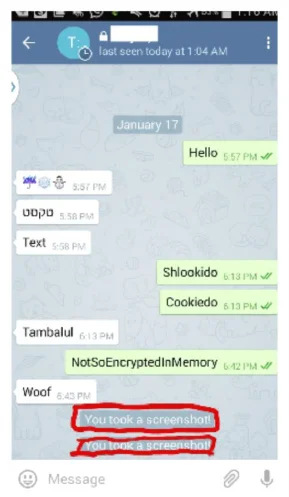
I gave Telegram a chance and did not check common mistakes in software that do not have security priority. I simulated an attack using a security weakness on the user side or software and using Kernel Exploit (using CVE-2014-3153). There were cleaner ways to get the answer, but I preferred providing proof of concept (POC). Telegram has the option of secure chat or a lock on top of the image, giving a sense of security. I took a copy from the process memory and looked for a word I used in the chat.
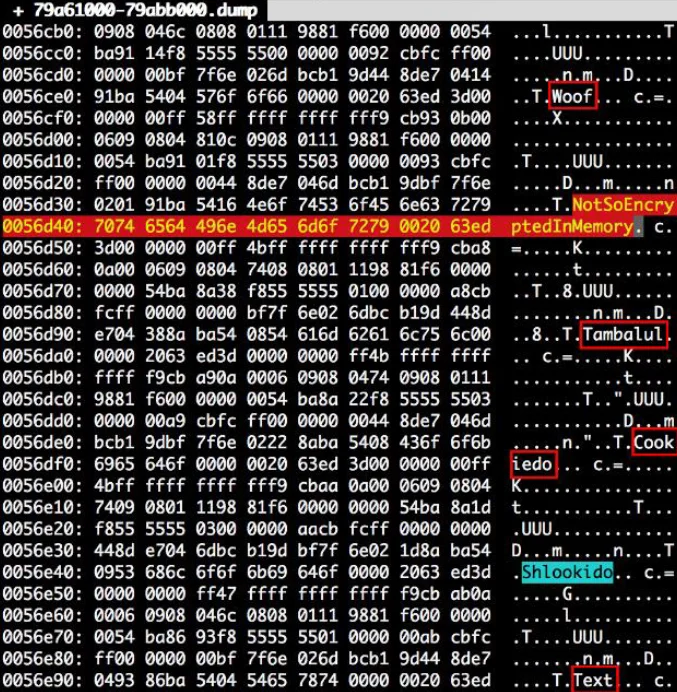
As you can see, the words:
NotSoEncryptedInMemory, Tambal, Cookie, Shlookido, Text, Woof
They are seen unencrypted in memory. Any attacker penetrating the device will have access to the text of the messages without any problems. So Telegram’s secure chat can be read as clear text. This made me wonder if there is an easier way to access the text of the messages. And unfortunately, the answer was yes.
To complete the investigation, using the root access that I had obtained with the help of Kernel Exploit, I checked the cache files /data/data/org. Telegram,.messenger/ and found the cache4—DB file in the software folder.
I assumed that the prefix enc in the names of the enc_chats and enc_tasks_v2 tables is Encrypted, so I removed the file and checked it. The file contained all secure chats in clear text.
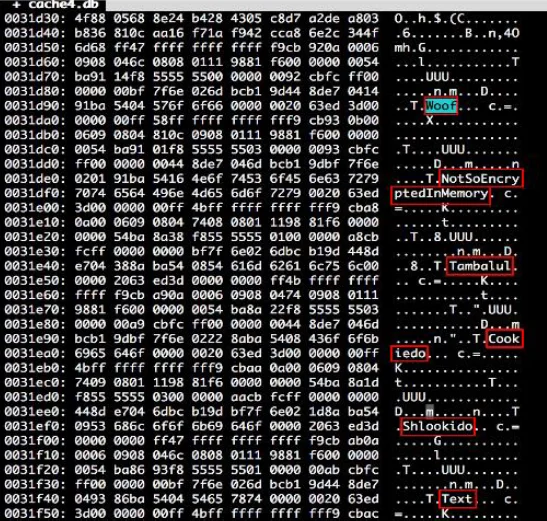
One of the interesting features of Telegram is the ability to delete messages. I tried to recover the messages deleted by the user. For this, I checked the memory and the cache4—DB file. In the settings section, I deleted the messages after 5 seconds. I expected this to happen, but the messages were not deleted. It appears to be a bug and not a security issue. I deleted the message using the Delete option.
By checking the cashe4.DB file, I did not see any traces of deleted messages. Deleted messages are usually more attractive to the attacker. Then I checked the memory, and unfortunately, the messages were still visible in the memory after deletion.
Conclusion
Telegram operates to maintain privacy and without cost to users. The attention of this software to the security of the information being transferred and ignoring the security of the information stored in the device has caused this problem. The regrettable point is the Telegram security team’s failure to respond to this weakness’s high calls. The security claimed by Telegram is nothing more than software and pages that use SSL.











