What is a port? | Types + its application in the mobile network
What is a port? | Types + its application in the mobile network
Gateway (computer networks)
The operating system divides and sends data to the central processing unit for better and more effective processing of the processing unit and better management of information on different types of data. The information ports that are responsible for this task are called software ports.
The number of software ports is from zero to 65,535, some of which are reserved by the IEEE Institute for a series of functions, and the rest are free. The firewall performs the task of managing software ports.
port functions
Identifying the types of connections between the two endpoints of the port. (example: server and computer)
You can also identify network protocols and network services.
Port 80 is used:
The TCP port is 80 on the Internet, and Hypertext Transfer Protocol is used.
In the case of an IBM PC (in English: IBM PC) — the I/O port is 80, and PostScreen can access it.
Ports are virtual ports controlled by the computer’s operating system. Each port is the starting and ending connection point of any network, and thanks to them, you can run one or more networks on your PC simultaneously without interference. Computers can separate incoming streams using these virtual ports.
In today’s world, the network and the Internet are an inseparable part of every life, and the more knowledge and information you have about it, the better you can use the Internet. This article has thoroughly and comprehensively reviewed the port and introduced its types. So if you want to know more about PORTs, stay with us.
What is a port?
As mentioned, ports are virtual ports controlled by the computer’s operating system and allow the simultaneous use of at least two Internet connections without interference or problems. In the network world, there must be three main pillars to communicate with any device.
The first pillar is the infrastructure; if you want to use the Internet or any small or large network, you must set up the network cable, modem, router, WiFi, etc.
The second central pillar is the address. Communicating is abstracted from sending any request and receiving any response. Therefore, if we do not know where the origin and destination are, we cannot imagine any network or Internet. IP Addresses are the unique addresses provided to connected devices on the Internet and the web.
The third fundamental pillar is the object that conveys requests and responses. That is, when your letter will reach its destination and in the hands of a friend, acquaintance, relative, brother, sister, mother, and in general, anyone you have chosen if there is a mail carrier or post office. The post office and postman of the Internet is a TCP protocol, which we will fully describe in a separate article.
With the explanations given, it is possible to provide the example that the Internet is exactly like a city, village, province, or country. Even the earth, whose infrastructures are roads and streets, the destination and origin are houses and buildings whose addresses are known, and sending requests and Returning the answers is also the responsibility of the postman (traditionally). Now the port will be at the door of houses, buildings, offices, shops, restaurants, and other places that can send or receive requests and responses.
What is the use of the port, and why is it there?
When using your mobile phone, PC, or even your laptop while it is connected to the Internet and you are using Telegram, for example, there are at least two different connections. The first connection is related to the filter breaker, and the second is to the Telegram network.
How is this possible using the same internet model (home or SIM data connection) now?
It must be said that it is thanks to the port that you can first turn on your filter breaker and then enter Telegram, use Google Chrome and download a file at the same time, have several download queues, and receive all at the same time, and many From other examples that will be realized with only one connection. That means you don’t need to establish a SIM card data connection for downloading movies and a home internet connection for web browsing.
A postman is a person who delivers all your letters from different places. A connection has all the codes, requests, responses, etc., simultaneously and in bulk to the phone, laptop, or any device, and each port receives and receives its bid. As a result, thousands of different networks can be used simultaneously.
Types of network ports
It is better to mention again that the meaning of port is the same as the entrance and exit door of a building. Now, this door or gate can be virtual or hardware in the computer. In general, the types of ports are as follows:
- Hardware ports
- Software or virtual ports
- Hardware ports
A port connects a flash drive, mouse, keyboard or keyboard, external hard drive, or any other hardware device to your computer, such as a USB port for connecting a mouse, flash, keyboard, or SATA port for connecting an internal SSD hard drive. The hardware port refers to the physical ports responsible for communicating between devices.
Software or virtual ports
Virtual ports or software ports are responsible for establishing virtual communication to receive virtual data. A computer will eventually have 50 different hardware ports, but 65535 virtual ports are specified as numbers and are also called port numbers. In the following, we will discuss the complete and detailed analysis of port numbers and their types, so stay with us as we continue the article.
What is the port number?
Maybe this question has troubled your mind, how do the ports find out which message belongs to them from the multitude of received messages? In response, it should be said with port or port numbers. First, it is better to give a brief explanation about packets.
Each request and response is not sent ultimately; that is, if you have a request such as loading a page from a site, all the data of that screw is sent piece by piece (the size of each piece is approximately 1400 bytes), and finally the packets are combined, and the page is loaded. (Of course, the size of the packages is different and depends on other elements).
In addition to the requested data, the packets contain other information, including the port number. The port number can be any number (e.g., 1245). After reaching the destination, each package will be received by the corresponding port, which is identified by the same port number.
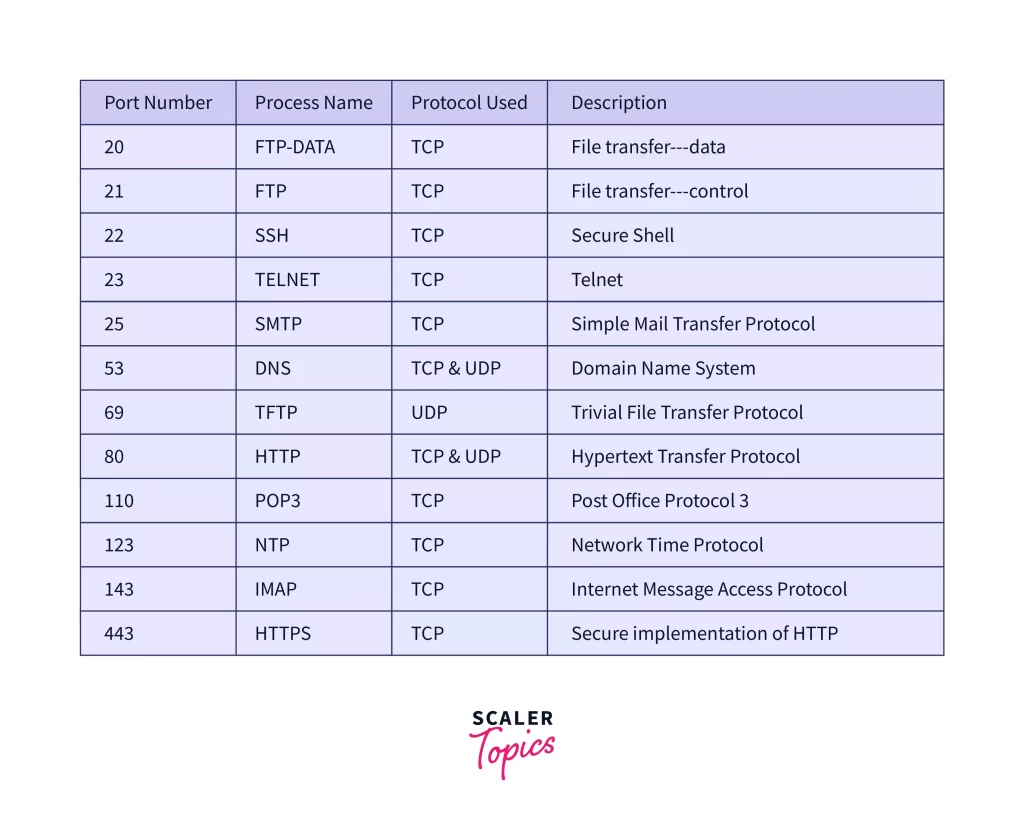
Checking some commonly used port numbers
It should be mentioned that there are 65,535 different ports, but it is not common to use all of them. It means that some port numbers are being used continuously by necessary protocols, which we will examine further.
- Port numbers 20 and 21: The FTP protocol uses These port numbers. FTP is File Transfer Protocol that transfers data and files between the client and the server. This means all the packets sent and received in this protocol enter the device through ports 20 and 21.
- Port number 22: This number is used by the SSH protocol. SSH stands for Secure Shell, one of the many tunneling protocols to secure network connections.
- Port number 25: This port number is used by Simple Mail Transfer Protocol or SMTP for short. When you open your e-mail management program, all the data related to received e-mails or e-mails you want to send will enter and exit door 25.
- Port number 53: port number 53 is used by the DNS or Domain Name System protocol. To get familiar with this protocol, suppose you enter a website address in your browser’s search box. As mentioned, there is a unique IP address for every object connected to the Internet (like this site you are browsing).
But the format of these IP addresses will be 123.123.123.123 or 2702:A0B3:8012:D0E5:0000:0000:0000:B25F:
Admittedly, it’s hard to remember these numbers even for a single site, let alone trying to keep any site’s address in this format. To solve this problem, the DNS protocol was created, and when you search for any site address like google.com, the Domain Name System takes this phrase and exits through port 53 (the same as port 53) after finding the original IP from the same Door 53 is entered, The basic format of the address is delivered to the browser.
Port number 80 is one of the most important port numbers used by the famous HHTP protocol. It is rare to find anyone who has not seen the word HTTP next to URLs at least once.
This protocol stands for Hypertext Transfer Protocol, the foundation and cornerstone of the World Wide Web or WWW.
The task of HTTP is to transfer metatexts such as images, videos, programming codes, simple texts, etc., which designers place on each site page through PORT NUMBER 80. We will further investigate this protocol in the future.
- Port number 123: The NTP or Network Time Protocol uses this number to synchronize computer clocks. It is also part of the process used to encrypt other protocols or transfer data.
- Port number 179: Number 179 is assigned to BGP or Border Gateway Protocol. This character creates excellent and efficient communication paths between large networks that eventually make the Internet.
- Port number 443: https port or port number 443 is used by HTTPS. A protocol that is a secure and encrypted HTTP mode and stands for Secure Hypertext Transfer Protocol. Some security protocols, such as SSL or TLS, encrypt data in transit. In addition to HTTP, some sites use one of these protocols (often SSL) for greater security and to prevent manipulation of site codes during sending or receiving.
- Because SSL itself runs inside HTTP, you’ll see HTTPS next to the site’s URL instead of HTTP. It should be noted that the DNS protocol is implemented through HTTPS and connected through port 443.
- Port number 500: The Internet Security Association and Key Management Protocol (ISAKMP) uses port number 500 to implement and execute part of the secure IPsec connection process.











