What is the ProgPow algorithm? Ethereum extraction algorithm
One of the most important pillars of a digital currency network is the hash algorithm. Hash algorithms provide network security and greatly affect the speed of transactions on the network. The ProgPoW algorithm is one of the most popular hash algorithms based on the Ethash algorithm used in the Ethereum digital currency network. This algorithm is one of the atrium extraction algorithms. The ProgPoW algorithm and the Ethash extraction algorithm are that ProgPoW is a programmable proof-of-work algorithm, and each network can program its optimal proof-of-work method.
What is the ProgPoW algorithm?
The ProgPoW algorithm is a short form of programmable proof of work and stands for Programmable proof of work. It is sometimes popularly called PorgyPoW. This algorithm is developed from the Ethash algorithm that is GPU compatible to minimize the performance gap on fixed-function hardware.
This paper reviews the technical specifications and performance criteria of this algorithm. This article does not provide a justification or rationale for using this algorithm in a digital currency, and each digital currency should use its network-based algorithm based on its research.
To improve extraction efficiency, proven proof-of-work algorithms, and developed hardware. But ProgPow did the opposite, fixing the hardware and modifying the algorithm.
If an algorithm is efficient, it must be compatible with access patterns and the space available in the extraction hardware. That’s why AMD saw a huge increase in performance in Ethereum; Because the access patterns of the memory, chips were compatible with the Ethash extraction algorithm.

Ethereum currently uses the Ethash algorithm. This algorithm is a proof-of-work algorithm that works well with GPUs. This algorithm requires almost a lot of buffer (currently about 2.5 GB) and a lot of bandwidth, both of which are provided in the GPU.
One of the challenges of the Ethash algorithm is that it reads only 128 bytes of main memory, which is very small. This low availability makes GPUs that use GDDR5x memory inefficient to run the Ethash algorithm.
Another issue with using a GPU card is that Keccak (the hash function at the beginning and end of Ethash) can run much more efficiently using FPGAs or ASICs.
Acorn line FPGAs are specifically designed to perform Keccak calculations offline to save system energy consumption and increase efficiency.
Based on these issues, a specialized ASIC for Ethash can be designed with the following features:
- A high-bandwidth memory interface (typically using GDDR6 or HBM2)
- A Keccak engine
- A small computing core for performing the internal FNV loop
- The resulting ASIC will be smaller and consume much less power than existing GPUs.
ProgPoW algorithm innovation
ProgPoW design started with Ethash. This algorithm has been modified to make the most of the GPU.
The hashes generated by the Keccak function and used at the beginning and end of Ethash changed from f1600, 64 bytes per word, to f800, 32 bytes long. The F1600 requires at least two instructions to run on a graphics card; because GPUs’ data path is 32 bits, it needs to be read at least twice to read a 64-bit word. The Ethash algorithm does not use additional data processed by f1600; Therefore, reducing the amount of data bytes and word length in this algorithm does not affect the security.
Requirements of the Keccak algorithm
A device to run ProgPoW must include the following:
- A high bandwidth memory interface.
- A computational kernel with a large registry file.
- A computational core with high power of the mathematical solution.
- High productivity; High cache.
- Small engines Keccak + KISS99.
These special cases are very similar to GPUs; They are only slightly smaller but have the same function.
The hash rate in the Progpow algorithm
One of the most important factors for examining extraction algorithms is the hash rate of these algorithms. The hash rate indicates the performance speed of the algorithm. In other words, the hash rate determines how fast the algorithm can hash the data. Of course, the hash speed does not only depend on the extraction algorithm but also the extraction hardware has a great effect on the hash speed. The table below shows the hash rates of the Ethash algorithm and the ProgPow algorithm on different hardware. Memory bandwidth consumption is also calculated in these two algorithms. The percentage of the actual hash rate in the bandwidth column is calculated as the theoretical hash rate if 100% of the GPU memory bandwidth is used, which is impossible in the real world.
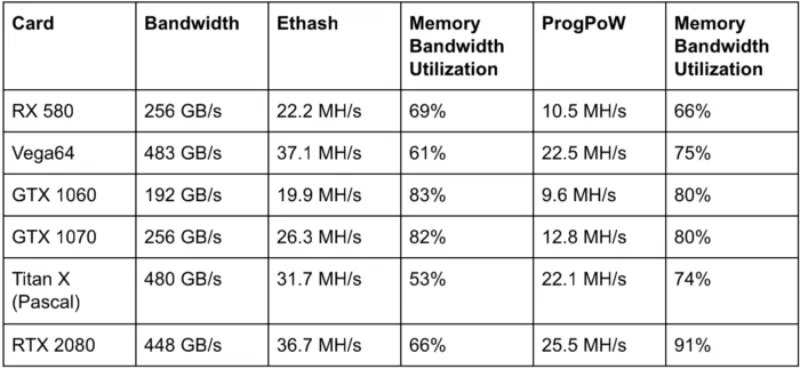
The hash rate is theoretically calculated by dividing the bandwidth by the amount of data per hash. In other words:
Bandwidth / Data-per-hash
This value equals 8 KB in the Ethash algorithm and 16 KB in the ProgPoW algorithm.
The general expectation is that ProgPoW should have about half the Ethash hash rate; Because this algorithm requires twice as much Ethash access to memory per hash. This problem is more common in GPUs that use GDDR5, RX 580, and GTX 1070 memory. GPUs that use HBM2, GDDR6, and GDDR5X memory are more efficient than the ProgPoW algorithm.

Concluding remarks
In this article, we describe the ProgPoW algorithm and its features of this algorithm. One of the concerns about this algorithm is that using this algorithm, AMD and Nvidia will be able to apply their views on the Ethereum network and create a hard fork on the Ethereum network.
Some critics also believe that ASIC devices make the network more secure and that it is useless to create algorithms such as ProgPoW and try to remove ASICs; Because ISIC manufacturers are also designing new technologies for extracting digital currencies.











