What is the Ethash Algorithm? Introduction and application of ETHash extraction algorithm
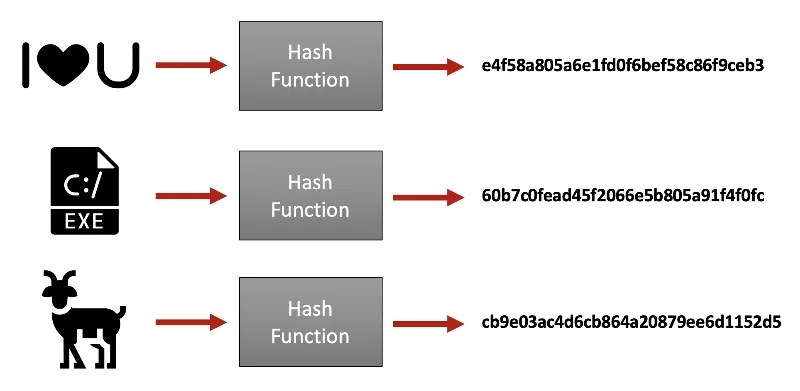
To have a secure Internet, you need hash functions. Hash functions are one of the most important and practical issues in computer science; in addition to increasing security in the Internet space, cryptographic algorithms are also very useful in digital currencies. So hash functions are mathematical algorithms that receive variable size and length data and convert it to uniform and actual output. In these functions, the input cannot be obtained from the output; For this reason, these algorithms provide a very high level of security. One of these popular hash algorithms is the Ethash algorithm. The Ethereum team designed the Ethash algorithm. In this article, we want to learn more about this algorithm. Stay with us.
What is a hash function and algorithm?
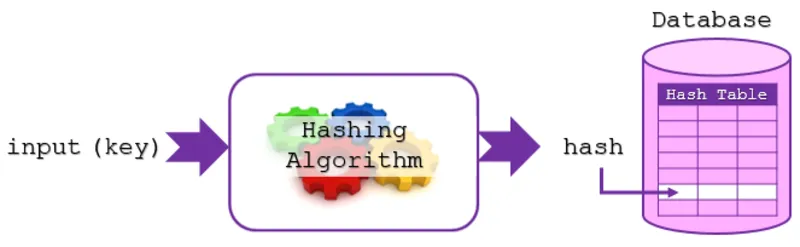
ه Hash functions are used to store and retrieve information at high speed, securely store passwords, find duplicate records, etc. Hash is created using a mathematical algorithm, and its existence is essential for blockchain management in the digital currency space. So the hash algorithm is the basis of the blockchain network.
Hash algorithms are also one of the most widely used concepts in digital currency extraction and play an important role in extraction. So company Developcoins development services and solutions based on cryptographic algorithms worldwide.

Some examples of popular hash algorithms in digital currencies are the SHA-256, Scrypt, and X11 algorithms. The number of mining algorithms is also increasing due to the large number of coins that enter the digital currency market every day. There are currently many hash algorithms used to extract various digital currencies.
We will learn more about the Ethash algorithm and how it works in the following. Also, let’s first look at Ethereum’s digital currency network, the maker of the AT hash algorithm.
Ethereum
Ethereum is not just a platform but a programming language and one of the largest and most widely used decentralized platforms.
OS allows intelligent contracts and decentralized applications (DApps) to be executed without interruption, fraud, control, or interference by a third party or intermediary. Ethereum with Ether is known in digital currency exchanges and can be used to run decentralized applications and games.
Blockchain currently uses the Proof of Work (PoW) algorithm, the latest version of the Dagger-Hashimoto algorithm, called Ethash.
Ethereum has already implemented the Keccak and Ethash algorithms. The purpose of these two algorithms is to compress the address, connect the blocks, and extract.
What is the Keccak Algorithm?
The application of Keccak and Ethash algorithms is different and used in different systems. The initial hash algorithm in the atrium is called Keccak. This algorithm collects the data and generates the output based on the previously processed data. The Keccak algorithm is used for various applications, except for extraction.
What is the Ethash Algorithm?
The Ethash algorithm is used for extraction purposes only and uses the Proof of Work algorithm built specifically for Ethereum (ETH). So the function is resistance to PoW ASIC machines. Ethash is ASIC resistant and consumes so little memory that it can only be extracted using a GPU or CPU.
Features of the Ethash algorithm
- The hash extraction algorithm is designed to be resistant to ASIC machines. To achieve this goal, this algorithm is designed to use maximum memory.
- The ethash extraction algorithm is very suitable for GPU devices.
- New blocks must be approved immediately on Light clients.
- New blocks should be handled slowly on light clients.
- Light clients should be allowed to start as soon as possible.
- The Ethash algorithm is a modification of the Dagger-Hashimoto method.
What is the Dagger-Hashimoto method?
The Dagger-Hashimoto method is part of the atrium extraction algorithm and has two main parts:
Dagger: Dagger is an algorithm designed by Ethereum creator Vitalik Buterin, which was supposed to replace existing algorithms such as Scrypt.
Hashimoto: An algorithm designed by Thaddeus Dryja that aims to achieve ASIC machine resistance by limiting input and output (IO). Hashimoto uses blockchain as the primary data source.
How does the Ethash algorithm work?
The Ethash extraction algorithm can work with both CPU and GPU. Ethash-based digital currencies are different in terms of extraction. Also, to start atrium extraction, you need a user with an extraction permit and at least a history of Ethereum. Other digital currencies based on the Ethash algorithm require a wallet or account on their networks.
CPU mining
CPU extraction Currencies based on the Ethash algorithm are almost twice as efficient and profitable as GPU extraction. Extraction with CPU in Ethereum is done with Geth. Geth is an application that connects the Ethereum network to the extraction tool. The extracted currencies are sent exactly to the miner’s address within the network.
GPU Mining
GPU extraction is the best alternative to Ethash. But Ethash consumes a lot of memory and requires at least 1 to 2 GB of RAM per GPU.
What cryptocurrencies use the Ethash algorithm?
Energi ،Metaverse ETP ،Restart Energy ،Ether Zero، Ubiq، Callisto، Pirl، Musicoin ،Expanse ،Ether-1 ،REOSC Ecosystem ،EtherGem ،Mix ،Ellaism ،Dorado ،Atheios ،Tourist Review Token، Master Contract Token ،VIP ،Ravelous ،Arorex ،Euphoria ،MUXE.
Concluding remarks
This article explains how the ETHash algorithm works and its technical features. One of the most basic concepts in digital currencies is the hash algorithm. These are the hash algorithms that provide security in digital currency networks. One of the most widely used algorithms in digital currencies is the Ethash algorithm. Also, the Ethash algorithm can perform extraction operations with both CPU and GPU. This algorithm is resistant to ISIC miners, and it is impossible to extract cryptocurrencies using the Ethash algorithm with ISIC miners. This algorithm is a proof-of-work hash algorithm designed specifically for the Ethereum digital currency but later used for other digital currencies.











