What is a Proof of Capacity (PoC) algorithm? Advantages and Disadvantages of Proof of Capacity
Most crypto enthusiasts are familiar with the pattern of proof of work and proof of stocks. Many blockchains use these algorithms to consolidate and secure the network. In recent years, new methods have emerged with numerous capabilities and benefits for network consensus. The proof of capacity algorithm is one of these methods that use hard disk space to create a new block.
What is a consensus algorithm?
In the Chinese blockchain, each network consists of many blocks that are interconnected in a chain. Development teams design processes for integration, coordination, data processing, transaction, security, and the creation of new blocks. These processes are called consensus algorithms. The capacity proof algorithm is one of these methods of network consensus.
Types of network consensus methods
The first model of consensus was called Proof of Work. Evidence of proof of work is based on hardware processing power. People who want to participate in PoW processes and earn money can create new blocks and receive rewards by purchasing processing hardware and solving hash functions.
Bitcoin, Light Coin, Bitcoin Cash, and Dodge Coin are some of the most popular blockchains that use the proof of work pattern. Details such as hash functions, required hardware, new block extraction time, and assigned rewards vary between networks that use PoW.

After proving the work, the Proof of Stake algorithm was designed. This algorithm tried to fix the shortcomings of the PoW method. The need for a high initial cost and high electricity consumption made it impossible for anyone to earn money through the proof of work model.
To participate in the PoS process, a certain amount of native network ciphers must be purchased and deposited in liquidity pools or other network protocols. In this way, each person can participate in the network consensus process with little initial capital. Perhaps the only drawback of this method is the low financial return. The rewards of the stock proof model are less than the proof of work, but there is no longer any investment risk or hassle related to the power supply and hardware maintenance.

New models have been designed in recent years, some of which have significant advantages. The developers tried to eliminate the shortcomings of the previous algorithms by creating new processes. Proof of agency shares (DPoS), proof of optional agency shares (PLoS), history proof (PoH), and proof of importance (PoI) are other developed models. In the meantime, proof of capacity (POC) became more popular and was able to find many fans at times.
What is Capacity Proof (PoC)?
The Proof of Capacity algorithm is a Chinese blockchain consensus algorithm developed based on hard disk space and storage volume. In the PoW model, the processing power of the hardware, including the graphics card or CPU, is the main factor in the extraction process. Still, in the capacity proof model, hard disks are the main factor for data processing and creating new blocks.
The free space of each hard disk is used to solve the hash function. The PoC algorithm is more efficient than PoW and PoS. Numerous blockchains such as Chia, Storj, SpaceMint, FileCoin, and Burst use this algorithm for network consensus.

There are several reasons to use the capacity proof algorithm. Energy consumption is very high in proof of work. Bitcoin mining last year created many problems for governments in terms of energy supply. Many countries have banned bitcoin mining. There are also concerns about whale dominance and centralism in the stock-proof method.
The capacity proof model is designed to avoid the problems of previous algorithms. Of course, this method also has disadvantages that we will mention in the following. Still, power consumption and lack of capitalist domination are in a better position than PoW and PoS algorithms.
How does the capacity proof algorithm work?
The larger the storage space and the size of the hard drive, the better the chances of solving the hash function and making money from the capacity proof algorithm. The execution process of proof of capacity can be divided into two stages: Plotting and Mining. The hard disks must be in a specific circuit in the plotting phase.
First, a nonce is formed. Nance is a number that will eventually lead to solving the hash function and creating a new block. Each nance consists of 8192 hashes. Both hashes form a scope. As a result, it can be said that each nance contains 4096 scoops. The more space and hard disk space you have, the more nans you can form. The image below depicts the structure of a nance.
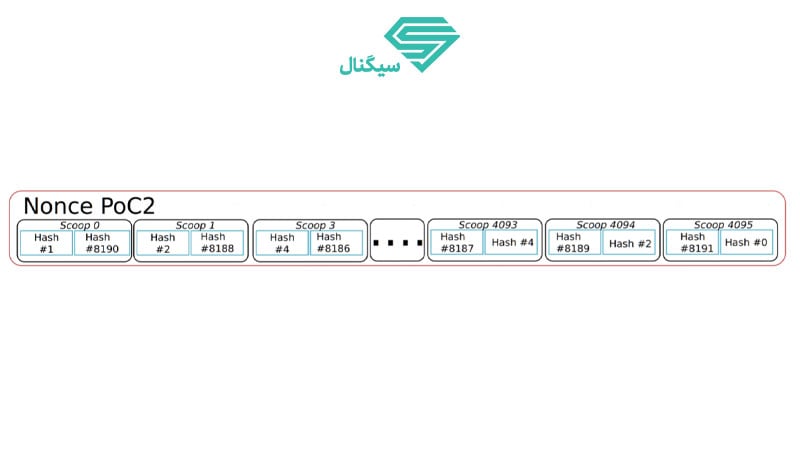
The results of the calculations will be equal to one of the numbers in the scope. After obtaining the answer to the function, the number obtained in the scope is considered. In this case, the Deadline parameter must be calculated. Deadline is the time that must have elapsed since the last block was created to allow the creation of a new block. Deadlines are calculated in each nance, and the minimum number will be the basis for creating a new block. If no new block is generated during this period, you will have a chance to extract the block and earn a reward.
Advantages and advantages of capacity proof pattern
The capacity proof algorithm has different advantages and disadvantages. Although these may vary depending on cryptocurrency conditions, digital currency prices, energy status, costs, etc. In general, the benefits of this model are:
- Ability to participate in the network consensus process with the help of ordinary hard disks
- It consumes much less energy than ASICs and GPUs
- Initial costs and lower barriers than extraction or deposit methods
- Ability to reuse hard drives after the mining process
- No need for upgrade costs and hardware upgrades
The following can also be mentioned as disadvantages of the PoC algorithm:
- Many blockchains do not use this pattern of consensus.
- Malware is more likely to be transmitted and infiltrated than other consensus methods.
- If the number of miners increases, there is a possibility of intense competition in the purchase of hard drives and the leadership of the rich.
Conclusion
The capacity proof algorithm is one of the newest methods for China Block Consensus. So this method uses the hard disk to create new blocks and process data. The more space you share, the better your chances of earning money.
Although many cryptocurrencies do not yet use this method for network consensus, several advantages make it possible for developers to embrace the algorithm in the future.










