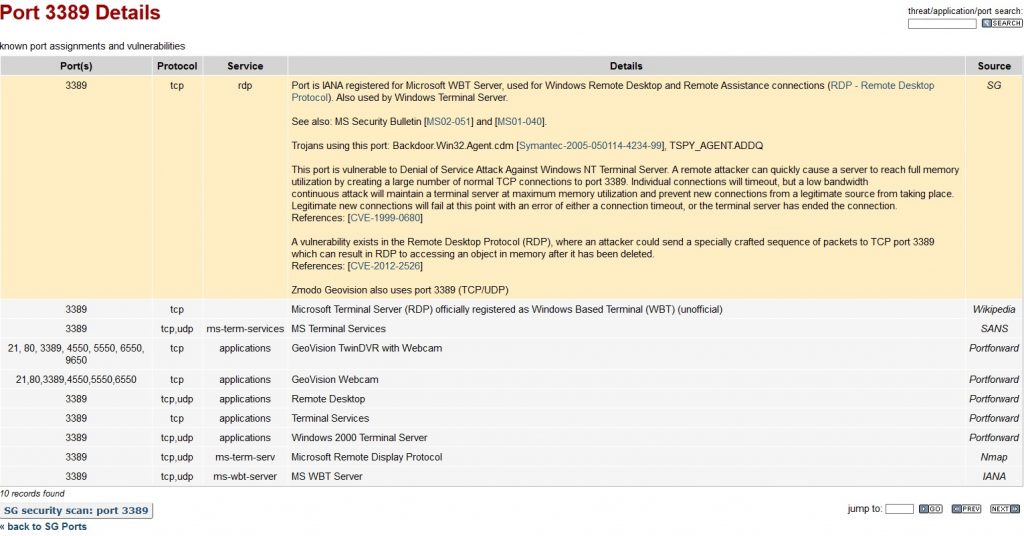
Remote Desktop Protocol 3389
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft Corporation which provides a user with a graphical interface to connect to another computer over a network connection.
The user employs RDP client software, while the other computer must run RDP server software.
Clients exist for most versions of Microsoft Windows (including Windows Mobile, but the support has ended), Linux (for example, Remmina), Unix, macOS, iOS, Android, and other operating systems. The server listens on TCP port 3389 and UDP port 3389 by default.
Microsoft currently refers to their official RDP client software as Remote Desktop Connection, formerly “Terminal Services Client.”
The protocol is an extension of the ITU-T T.128 application sharing protocol. Microsoft mak”s some specifications pub” is on its website.
What is Port 3389?
Both services use TCP port 3389. These two similar services enable access to remote computers for different purposes.
Support personnel primarily use remote assistance to help users resolve computer problems.
Remote Desktop, or RDP, enables users to access a physically remote machine and is often employed to allow employees to interact with their work computers from home.
What is port 3389 used for?
Port 3389 is used to enable users to access remote computers. While in most cases, this access is legitimate and approved by the owner of the physical machine.
There are also port 3389 vulnerabilities that make limiting access critical. Only authorized users should be able to request port 3389, eliminating the possibility of an attack using the port as a gateway to enterprise computing resources.
What are the security risks of Port 3389?
The vulnerabilities of port 3389 illustrate the dangers and complications of ensuring secure remote access, as it can be the open window through which hackers compromise your systems.
Several methods address port 3389 vulnerabilities to protect a computing environment.
- One measure can be to lock down port 3389 by implementing secure tunneling.
- Firewalls can also be configured to only allow access to port 3389 from a designed list of safe IP addresses.
Unfortunately, this method of defense can be thwarted by hackers who have hijacked a computer on the safe list and used it as their platform for initiating attacks.
Notes:
Port numbers in computer networking represent communication endpoints.
Ports are unsigned 16-bit integers (0-65535) that identify a specific process or network service.
IANA is responsible for internet protocol resources, including registering commonly used port numbers for well-known internet services.
Well, Known Ports: 0 through 1023.
Registered Ports: 1024 through 49151.
Dynamic/Private: 49152 through 65535.
TCP ports use the Transmission Control Protocol, the most commonly used protocol on the Internet and any TCP/IP network. TCP enables two hosts to establish a connection and exchange streams of data.
Well, TCP guarantees data delivery and that packets will be delivered in the same order they were sent. Guaranteed communication/delivery is the key difference between TCP and UDP.
UDP ports use the Datagram Protocol. Like TCP, UDP is used in combination with IP (the Internet Protocol) and facilitates the transmission of datagrams from one computer to applications on another computer, but unlike TCP, UDP is connectionless and does not guarantee reliable communication; it’s up to the application that received the message to process any errors and verify correct delivery. UDP is often used with witnation’sensitive applications, such as audio/video streaming and real-time gaming, where dropping some packets is preferable to waiting for delayed data.
When troubleshooting unknown open ports, finding exactly what services/processes are listening to them is beneficial.
This can be accomplished in Windows command prompt and Linux variants using the “netstat -aon” command. We also recommend runnig multiple anti-virus/anti-malware scans to rule out the possibility of active malicious software.
Security Primer – Remote Desktop Protocol 3389
Remote Desktop Protocol (RDP) is a Microsoft proprietary protocol that enables remote connections to other computers, typically over TCP port 3389. It provides network access for a hidden user over an encrypted channel. Network administrators use RDP to diagnose issues, log in to servers, and perform other remote actions. Remote users use RDP to log into the organization’s network to access email and files.
Cyber threat actors (CTAs) use misconfigured RDP ports open to the Internet to gain network access. They can then move laterally throughout a network, escalate privileges, access and exfiltrate sensitive information, harvest credentials, or deploy various malware.
This popular attack vector allows CTAs to maintain a low profile since they utilize a legitimate network service and provide the same functionality as any other remote user. CTAs use tools like the Shodan search engine to scan the Internet for open RDP ports and then use brute-force password techniques to access vulnerable networks. Compromised RDP credentials are also widely available for sale on dark web marketplaces.
In 2018, the Multi-State Information Sharing and Analysis Center (MS-ISAC) observed increased ransomware variants that strategically target networks through unsecured RDP ports or brute-forcing passwords. The ransomware is then manually deployed across the entire compromised network and is associated with higher ransom demands.

Recommendations:
- Assess the need to have RDP, port 3389, open on systems and, if required:
- Place any system with an available RDP port behind a firewall and require users to VPN in through the firewall;
- enable strong passwords, multi-factor authentication, and account lockout policies to defend against brute-force attacks;
- allowlist connections to specific trusted hosts;
- restrict RDP logins to authorized non-administrator accounts, where possible. Please adhere to the Principle of Least Privilege, ensuring that users have the minimum level of access required to accomplish their duties;
- log and review RDP login attempts for abnormal activity and retain these logs for a minimum of 90 days. Ensure that only authorized users are accessing this service.
- If RDP is not required, perform regular checks to ensure RDP ports are secured.
- Verify cloud environments adhere to best practices defined by the cloud service provider. After the cloud environment setup is complete, ensure that RDP ports are not enabled unless required for business purposes.
- Enable automatic Microsoft Updates to ensure that the latest versions of both the client and server software are running.
The MS-ISAC is the focus for cyber threat prevention, protection, response, and recovery for the nation’s state, local, tribal, and territorial (SLTT) governments. More information about this topic and 24×7 cybersecurity assistance are available at 866-787-4722, SOC@cisecurity.org. The MS-ISAC is interested in your comments – an anonymous feedback survey is available.











