Proof of work algorithm
Proof of work algorithm
In blockchain technology, no central institution or organization is responsible for confirming information and registering it. this system, users should be able to reach a consensus on the correct information using the determined algorithms and send the same information to the network’s distributed ledger. To do this correctly and to thwart cyber attacks to disable the system, a proof-of-work algorithm is used. In this article, we want to answer the question of what is the proof-of-work algorithm by examining the reasons for its need, how to set it up, and how to reach consensus among users in the network.
What is blockchain?
Before examining the question of what is the proof-of-work algorithm, we need to have information about blockchain. Blockchain is actually a type of database where information is stored in the form of interconnected blocks. Blocks are connected together by mathematical functions called “hash functions” (Hash Functions), and any change in one block leads to hash changes in subsequent blocks.
The important point in the blockchain is that the information ledger is distributed. That is, transaction information is available to all network users, and for this reason, user consensus is needed to change transaction information or add new transactions. With the consensus of users, certain information is added to the network and all users add only that information to their ledger.
As you can see, the important thing in blockchain is the consensus process. Due to the fact that users from all over the world participate in this process and naturally not all users trust each other, consensus should be made in such a way that the security of the network is ensured and users do not seek to disturb the balance of the network. Next, we will examine the consensus algorithm.
What is consensus algorithm?
Consensus is a fault-tolerant mechanism used in computer systems and blockchains to reach the required agreement on a data value or a state. In multi-agent and distributed systems such as cryptocurrencies, the network fails without a consensus algorithm. Another use of the consensus algorithm is in recording the history and records of transactions and activities of network users.
In any centralized system such as the driver’s license database of people in a country, a central entity has the power and ability to maintain and update the database. Making any changes in the information such as adding new data, deleting part of the data and updating the information of different users are all done by this central authority so that only real and up-to-date information is stored in the database. This system is based on users’ trust in the central institution.
Public blockchains operate as decentralized, self-regulating databases without any central authority on a global scale. Hundreds of thousands of people participate in these networks and work on verifying and recording transactions made on the blockchain and block mining activities.
In such a network that is constantly changing and new information needs to be added to the network, we need an efficient, fair, reliable, secure, fast, and efficient mechanism to ensure that all transactions made in the network are genuine.
All participants agree on the current state of the network.
Such work is done in blockchain by consensus algorithm. A consensus algorithm is a set of rules that decide the legitimacy of network users to register and confirm transactions. The consensus algorithm ensures that the same information is sent to the network’s distributed ledger and all users have the same copy. In addition, the presence of rewarding mechanisms in consensus algorithms will encourage many users to participate honestly, and this issue will increase the network’s security. In the following, we will examine the question of what is the proof-of-work algorithm.
What is the proof of work algorithm?
“Proof of Work | PoW consensus algorithm” is the first consensus algorithm used in blockchain networks, but its history dates back to 1993. This algorithm was used at the time as a method against “Denial of Service” (DOS) attacks to disable systems and spam the Internet.
A few years later, “Hall Finney”, a scientist in the field of cryptography and computer science, used this algorithm to generate digital money, but he did not get much success. Finally, in 2009, Satoshi Nakamoto, the anonymous creator of Bitcoin, used this algorithm along with other cryptographic techniques for consensus on the network.
The proof-of-work algorithm in blockchain is used to confirm transactions and create new blocks for the chain. With the PoW algorithm, miners compete with each other to complete transactions to receive rewards from the network. In a blockchain network, users send their digital currency tokens to each other.
Distributed and decentralized ledger collects transaction information in the form of information blocks.
The important issue in this section is the confirmation of transactions and the order of adding blocks to the network. The responsibility of doing these things lies with the miners who do this during the process of mining digital currency. The main principles of doing the work is to use a mathematical equation that is difficult to solve but the proof of its solution is simple. Next, we will examine the components of this equation and how to implement the digital currency proof-of-work algorithm.
Hash functions and proof-of-work algorithm
In the proof of work algorithm, hash functions are used as complex mathematical equations. Any cryptocurrency that uses a proof-of-work algorithm may use a specific hash function. The hash function used in Bitcoin is SHA-256. Hash functions are one-way functions that provide a unique but fixed-size output for any input of any size. The output of these functions is called “hash”. Hash functions have different features, including the following.
Functions are one-way, so it is not possible to reach the input from the output. This feature is used to create public keys from private keys, and users cannot access the private key through the public key.
The output of each unique input is unique and the possibility of finding the same output for two different inputs is zero. Therefore, the smallest change in the inputs of the function leads to a change in the output.
Hash functions can be used to verify information without sending the information itself. For example, you can prove that you know the answer to a math equation by hashing the answer and sending the hash to someone else. If the other person knows the correct answer, he can compare the resulting output with your desired output by putting the answer in the hash function and thus evaluate your answer.
What is the difficulty of the network in the proof of work algorithm?
As mentioned in the proof-of-work algorithm section, the solution value of the equation in each block is determined by the network. The answer determined by blockchain can make the equation harder or easier. The purpose of changing the difficulty of the equation is that the processing power available in the network has the ability to mine digital currencies in a certain period of time. This period of time is in order to maintain the security of the network and has a different value in different networks. For example, in the Bitcoin network this number is 10 minutes and in Litecoin it is about 2.5 minutes.
The parameters of the number of network users, the current processing power and the size of the network affect the difficulty or ease of the equation. The main parameter among them is “Network Difficulty”. The difficulty of the network depends on the processing power of miner devices in the network. The higher the processing power, the less time there is to solve the equations. Therefore, with the increase in the processing power of the devices in the network, the equations become more difficult so that the time required to extract each block remains around ten minutes.
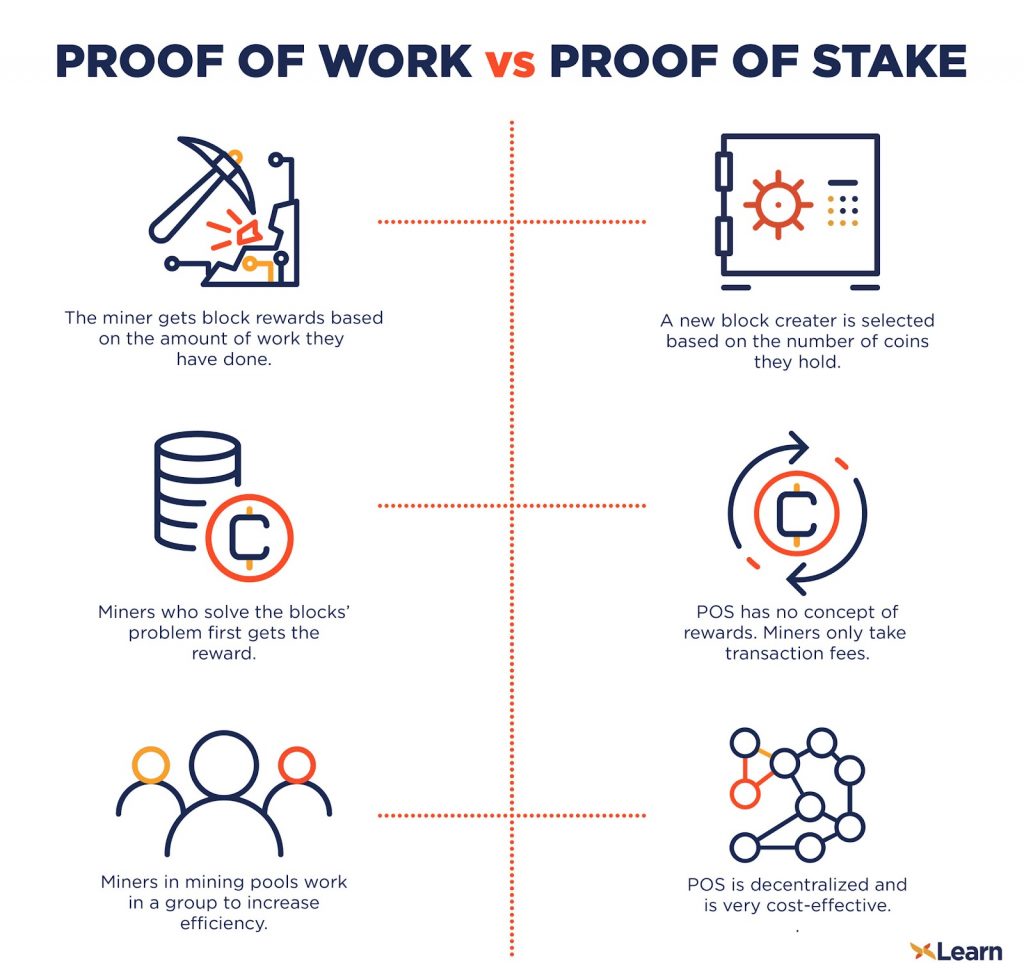
What is the difference between proof of shares and proof of work?
In the proof-of-work consensus algorithm section, it was said that this algorithm is the first consensus algorithm used in cryptocurrencies, but over time, various consensus algorithms were introduced and used for user consensus in distributed and decentralized blockchain systems. The most famous algorithm after proof of work is the proof-of-stake consensus algorithm, which has been used in various projects such as Cardano and Solana. The purpose of proof of stake, like proof of work, is to ensure the security and efficiency of the network, but the method of achieving this goal is completely different in these two methods.
And What are the advantages of the proof-of-work algorithm?
The main advantage of proof of work is resistance to dos attacks. There are limitations to the activity in the Bitcoin network. Hackers need to consume a lot of energy to perform their desired actions on the network. In addition to high computing power and energy consumption, an efficient network attack also requires a lot of time. Therefore, although attacking the network is possible in theory, it is ineffective in practice due to the financial cost and time required.
What are the disadvantages of the proof-of-work algorithm?
The first disadvantage of the proof-of-work algorithm is its high costs. Mining Bitcoin and other cryptocurrencies with a proof-of-work algorithm requires specialized computing hardware to run complex algorithms. Miner devices consume large amounts of energy for mining, which increases costs. As the difficulty of the network increases, it becomes impossible to mine Bitcoin with a home computer. Today, even Bitcoin mining with a graphics card is not profitable, and mining is done only using “ASIC” devices.