Convert Computer RAM To WIFI Card Two-Tailed Magnetic Blade: Wireless Charging Of Flying Robots
Now That You Are Reading This Article, All Kinds Of Electromagnetic Waves Have Filled The Space Around You. We Make Great Use Of These Invisible Waves.
I read content, downloaded videos and photos, sent messages to others, and. Of course, these waves have other uses as well.
They can use it to charge a flying robot remotely or steal other people’s information! These two are examples we will see in this article.
Convert computer RAM to WiFi card
A group of researchers has succeeded in attacking a computer’s main memory so that it can send information wirelessly.
So that a WiFi receiver can receive these signals, in this way, attackers can steal sensitive information wirelessly from a computer with no Wi-Fi or Internet connection, using only a memory card.
Over the past five years, researchers have conducted dozens of studies to investigate unusual methods of stealing from air-gapped networks. This type of attack uses channels to steal information that many ordinary people do not consider dangerous.
The term air gap refers to local networks and computers connected to them that do not have access to the external Internet.
Such networks are usually set up in sensitive government or military centers or where sensitive information needs to be stored.
These networks are attractive prey for attackers.
Researchers propose a new method to penetrate such networks because electromagnetic waves are emitted by passing an electric current through each electronic component. WiFi radio signals are also electromagnetic waves.
The malicious code embedded in the victim system modifies the electric current flowing through the system memory card to generate electromagnetic waves within the Wi-Fi limit of 2400 GHz.
In other words, these researchers have succeeded in setting the timing of the read-write operation on a computer memory card to create conditions in which the memory bus emits electromagnetic waves in the form of weak Wi-Fi signals.
The transmitted signal can be received by any device that can receive the WiFi signal within a few meters of the victim system, such as smartphones, laptops, IoT devices, and smartwatches.
The researchers tested the attack on several computers with Wi-Fi cards disconnected and were able to steal data from those computers at speeds of up to 100 beats per second.
The current method is one of the most direct attacks because the attacker does not need high-level access, and the victim’s system can be easily infected.
This feature makes this attack possible through any operating system and even through a virtual machine.
Although most newer RAMs can transmit signals in the 2400 GHz frequency range, the researchers say that by overclocking older RAMs.
One of the solutions that researchers have proposed to prevent such attacks is to send noise to disrupt Wi-Fi-based communications in the environment around computer systems.
Figure 1 – A computer that does not have an Internet connection is infected with malware (A). The malware uses the infected computer’s DDR memory to generate signals in the 2.4 GHz (WiFi) frequency band. Can receive Binary information by mounting this signal from nearby devices such as laptops (B) or smartphones (C).
Wireless charging of flying robots
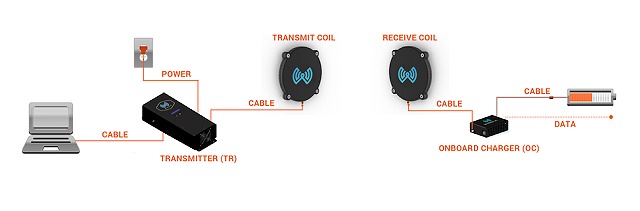
Figure 2 – Diagram of WiBotic’s charging system
Founded four years ago, the WiBotic startup seeks to provide solutions for charging flying robots so that these devices can achieve more excellent flight continuity. The company works on wireless charging of various robots, from industrial to swimming and flying robots. WiBotic has implemented its solution by combining two conventional wireless charging methods and using some software methods.
The idea of wireless charging has a long history, dating back to the late 19th century and Tesla’s efforts. Although the concepts of this method are well known, the design and positioning of wireless power transmission components to achieve the best efficiency is one of the significant challenges in implementing such chargers and requires careful design and the use of numerical simulations.
The induction connection method is standard in home appliances, but it is useful when the power transmitting antennas are very close. Robots, especially flying robots, cannot place the antennas close enough to each other, which reduces the efficiency of the induction connection method.
The flexibility of magnetic resonance imaging is more significant than inductive bonding, but there are a few things to keep in mind to achieve maximum efficiency.
WiBotic charging technology has tried to combine the capabilities of these two methods.
In this method, the relative location of the antennas is continuously monitored, and the software and hardware parameters are dynamically adjusted. Many parameters are adjusted in software to get the best charge in this solution. This charging system consists of four main parts of the hardware.
These sections include the transmission unit, power transmission antenna, charging unit, and the power receiving antenna. The charging station for flying robots is a platform with a diameter of 90 cm.
As the flying robot approaches the charging unit and lands, the intelligent infrastructure detects the robot’s battery type and adjusts the charging parameters accordingly. The system uses an STM32 microcontroller based on ARM processors, which runs a complex state machine with active control algorithms.












