Open network ports are golden opportunities to launch hacker attacks. If you don’t do the necessary things to protect your Mikrotik router and network, you can be sure that hackers can easily take advantage of this opportunity. The weaknesses of the network are identifying open ports and using them for attacks such as brute force and DDoS. This is where closing the scanner port becomes important.
Blocking the scanner port in Mikrotik increases network security against malicious attacks. For this, it is enough to open Winbox and, using Winbox’s graphical interface or terminal, create a list to store the IP addresses of the port scan and then use the drop action to block these addresses.
Although port scanning is one of the ways to discover network errors and weaknesses, and network experts use tools such as Nmap to identify active or open network ports before hackers, and do the necessary work to maintain network security, it is not 100% possible to prevent the penetration of hackers.
There are hackers who find a way to infiltrate the network, scan the ports, and use the reports about the ports in use to carry out malicious attacks.
If you, like most Mikrotik router users, are concerned about the security and stability of your network and you don’t want to pay a heavy price for neglecting the open ports of your network, it’s time to get started.
First of all, it is better to buy a safe and reliable Mikrotik virtual server. You don’t need to worry about this because we are by your side and have prepared great plans. By choosing the right plan for your network, you can own a secure yet powerful Mikrotik router.
Next, you need to learn how to close port scanners and prevent hackers from finding open ports on your network.
The solution that we have presented in this article will help you to handle this task in the best possible way. Therefore, we recommend that you read this article to the end and do the necessary things to maintain the security and strength of your network.
Table of Contents
- What is a port scan?
- Steps to close the scanner port in Mikrotik with the Winbox graphical interface
- How to close the scanner port using the Winbox terminal
- A few additional tips for better performance in preventing Mikrotik port scans
What is a port scan?
As in the article “What is Nets Can?” We have already mentioned that port scanning is a process during which all the open or active ports of the network are identified. This process is carried out for different purposes, the main of which is to discover open ports or active services that are considered a kind of network penetration hole.
Now, if network specialists do this to discover their network’s weaknesses, port scanning is a positive and productive action, but no law requires these scanning operations to be performed only by network specialists.
Many hackers use port scanner tools to try to identify open ports or overall weaknesses in the target network and use them as a starting point for their malicious attacks.
This is where you should consider protecting your network against port scanning by hackers and preventing such attacks by managing and controlling access.
Fortunately, with Mikrotik’s inbox tool, you can easily handle these tasks. Of course, if you can’t use the Winbox graphical interface, we also provide you with commands to close the scanner port so that you can act like a Winbox terminal.
Steps to close the scanner port in Mikrotik with the Winbox graphical interface
To close Mikrotik’s port scanning feature, you must first identify the IPs used for scanning and add them to a list. Next, configure the new firewall rule to filter connections from these IPs.
It’s time to go through this process step by step and visually:
Step 1. Add IPs related to port scan connections to a list.
- Open your Winbox and click on firewall from the IP menu.
- Then, click + to open the window to create a new firewall rule.
- Select the input option for the chain field and 6 (TCP) for the protocol type field.
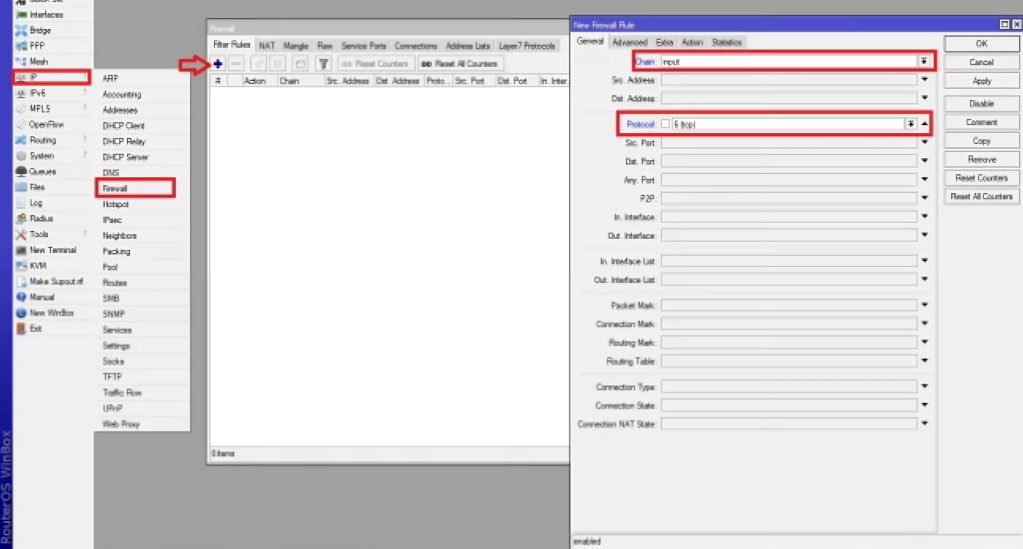
- Next, click on the action tab.
- For the action field, select the add src to address list method.
- Using the Address list field, name the IP address list Scanner list.
Finally, click Apply and OK, respectively, to add the scanners’ port IPs to the Scanner list.
Step 2. Delete or filter connections related to the Scanner list.
Now that the list of IP addresses used for scanning is created, it’s time to include the new firewall rule for this list.
- From the Winbox IP menu, select the firewall option.
- Click + to open the Create New Firewall Rule window.
- Select the input option for the chain field and 6 (TCP) for the protocol type field.
- Click on the advanced tab.
- In the Src field. Address List, enter the name of the list you specified in the previous step. In this tutorial, we named this list the Scanner list.
- Then click on the action tab.
- Select the drop-down option for the action field.
- Launch operation drop
Finally, click apply and ok respectively, to complete this action.
Following these steps will block connections related to the IPs used for port scanning. This will prevent unauthorized access and close the scanner port.
But this can also be done using the Winbox terminal.
How to close the scanner port using the Winbox terminal
The process of this method is the same as the previous method. However, in this method, instead of the graphical interface, we make all the tasks in the form of commands and execute them in the terminal.
This technique is more comprehensive than the previous one, and it can be used to close the scanner port in Mikrotik more precisely.
First of all, enter the WinBox and open the terminal.
Run the following command to enter the firewall settings:
/ip firewall filter
Then copy the following commands one by one and run them in the Mikrotik terminal:
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”Port scanners to list ” disabled=no
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”NMAP FIN Stealth scan”
add chain=input protocol=tcp tcp-flags=fin,syn action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”SYN/FIN scan”
add chain=input protocol=tcp tcp-flags=syn,rst action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”SYN/RST scan”
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”FIN/PSH/URG scan”
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”ALL/ALL scan”
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”NMAP NULL scan”
In the commands above, you see changes or details that were not there in the previous method.
The most important of these changes is the type of port scanning techniques that have been included. In this way, the identification of port scan IPs is done for all port scan techniques, and the list of IPs is collected by identifying the types of scans (NMAP FIN Stealth, SYN/FIN, SYN/RST, FIN/PSH/URG, ALL /ALL, NMAP NULL).
These scans are specified through the TCP-flags variable in the add chain commands, and the IP addresses of the requests that contain these flags are identified and stored in the port scanners list.
After you have created the list of port scan IP addresses, it is time to execute the drop action for these addresses. Then run the following command in the Winbox terminal:
add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no
After executing these commands, all IP addresses that intend to scan the port will be blocked, and you will succeed in closing the port scanner in Mikrotik.
A few additional tips for better performance in preventing Mikrotik port scans
- Close the ports related to unnecessary or unused services.
- Define correct and accurate firewall rules for the Mikrotik router.
- Restrict access to WinBox so that only valid IPs can access this tool.
- Update Mikrotik software and operating system to avoid security vulnerabilities.
- Monitor network traffic using commands and tools like PRTG.
- Check Mikrotik router reports frequently to identify and block unknown and suspicious activity.
- By teaching how to back up Mikrotik settings, backup information, and settings to return to the previous state in case of security problems.
- Changing the default ports makes it harder for hackers to detect common ports like ssh.
We hope that with the instructions in this article, you can properly implement the necessary security settings in the field of closing the scanner port in Mikrotik and protect your router and network from security threats.
Conclusion
Closing the scanner port in Mikrotik is one of the most important security measures in the network, which can be used to identify and block unauthorized access that leads to the discovery of network weaknesses. For this, you can use Winbox or Terminal graphical interface, each of which has simple and short steps and can lead you to the desired result.
Thank you for staying with us until the end of the article. We hope that reading this article was useful for you. If you have any questions or requests and need guidance, you can contact us by registering your opinion so that we can answer you as soon as possible.
FAQ
Why should I block port scanners on MikroTik?
Port scanners probe your router for open ports, which can expose vulnerabilities and risk unauthorized access.
How can MikroTik firewall rules help?
You can create filter rules that detect and drop suspicious scanning traffic before it reaches critical services.
What’s a basic step to stop port scanning?
Identify scanning patterns and configure firewall rules that limit connection attempts and block offending IP addresses.