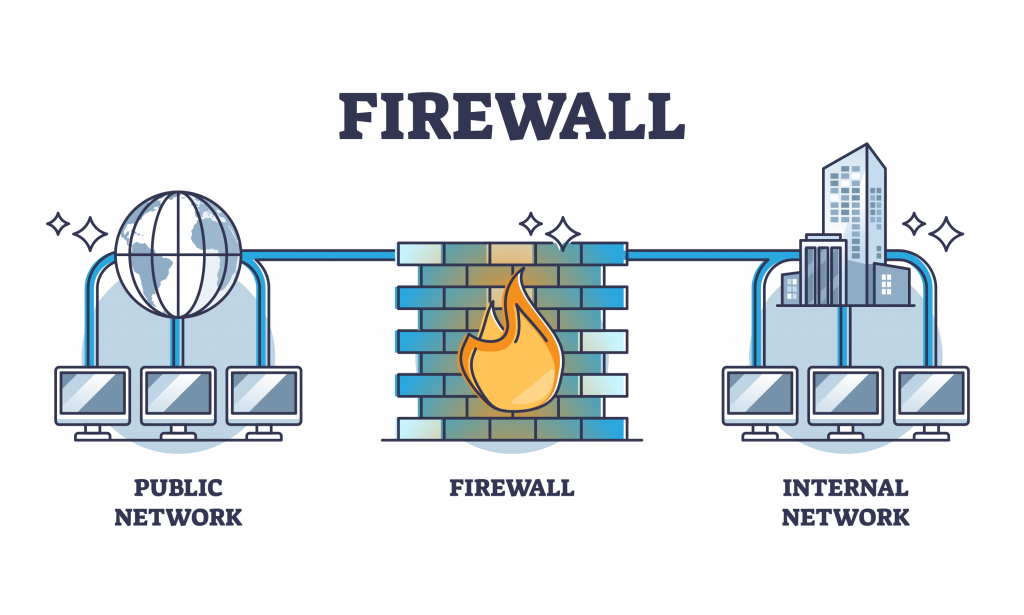
The concept of firewalls dates back to the 1980s, and the first firewall was developed in the late 1980s by engineers at Digital Equipment Corporation (DEC). The idea behind firewalls was to provide a layer of Security between internal networks and external networks, such as the Internet. The term “firewall” is believed to have been coined by engineers at DEC, who were looking for a term describing a System that could protect networks from external threats.
The first firewalls were simple packet filtering, which inspected Network packet source and destination addresses and allowed or blocked traffic based on predefined rules. Over time, firewalls became more sophisticated, and newer technologies, such as stateful inspection and application-level filtering, were developed to provide more advanced Network Security.
Today, firewalls are an essential component of network security. They protect networks from a wide range of threats, including malware, phishing attacks, and data breaches. Firewalls are widely used in enterprise environments, in-home networks, and small business environments to protect against unauthorized access and data theft.
As mentioned earlier, firewalls protect networks from unauthorized access and network-based threats. They are commonly used in enterprise and home networks to protect against internet-based threats.
In Part 1, we introduced some firewalls and explained their features and limitations. Here we provide you with more types:
Proxy Firewalls
Proxy Firewalls are a type of firewall that acts as an intermediary between a client and a server and can protect against attacks that exploit vulnerabilities in network protocols. They can inspect and modify network traffic before passing it on to the client or server. Proxy firewalls can also provide anonymity for clients by hiding their IP addresses from the servers they are communicating with.
Proxy firewalls intercept traffic between clients and servers and forward it to the appropriate destination. While doing so, they can inspect the contents of the traffic and apply Security policies, such as blocking traffic containing specific keywords or patterns. They can also modify the traffic, such as changing the client’s source IP address to provide anonymity.
Here are some examples of proxy firewalls:
1. Squid Proxy
Squid Proxy is an open-source proxy server commonly used for caching and filtering web traffic. It can be configured to provide a range of Security features, including content filtering, access control, and SSL/TLS encryption.
2. Blue Coat Proxy
Blue Coat Proxy is a hardware-based proxy firewall that provides advanced Network Security for enterprise environments. Its security features include content filtering, application layer traffic management, and SSL/TLS decryption.
3. Zscaler Proxy
Zscaler Proxy is a cloud-based proxy firewall that provides advanced Network Security for cloud-based environments. It provides a range of Security features, including content filtering, data loss prevention, and user authentication.
Proxy firewalls provide more advanced Network Security than other types of firewalls by intercepting and modifying Network traffic and providing anonymity for clients. This allows proxy firewalls to provide more comprehensive protection against network-based threats, such as DoS attacks and port-scanning attempts. However, proxy firewalls can still have limitations, such as the inability to detect more advanced threats, such as zero-day attacks or malware hidden within legitimate traffic.
Overall, proxy firewalls are an important component of Network Security, especially for environments that rely heavily on web applications and cloud-based services. It is important to regularly review and update firewall rules to ensure adequate protection against known threats and that the firewall is configured to provide optimal Security for the Network’s specific needs.
Limitations of proxy firewalls
While proxy firewalls are more advanced than other types of firewalls, they still have limitations that should be considered when implementing network Security measures. Here are some limitations of proxy firewalls:
1. Inability to Detect Advanced Threats
Proxy firewalls can only inspect and modify Network traffic and enforce specific Security policies. They cannot detect more advanced threats, such as zero-day attacks or malware hidden within legitimate traffic.
2. Limited Scalability
Proxy firewalls can become overwhelmed by high traffic volumes, leading to reduced performance and potentially enabling attackers to bypass the firewall.
3. Complexity
Proxy firewalls can be complex to configure and require a thorough understanding of the protected applications and the Security policies enforced.
4. Performance Overhead
Proxy firewalls can introduce additional latency and performance overhead due to the need to intercept and modify Network traffic.
5. Limited Protocol Support
Proxy firewalls are designed to protect specific applications and may not support all protocols used by the applications.
Overall, proxy firewalls are effective in some scenarios and are commonly used with other Security measures to provide comprehensive Network Security. However, the limitations of proxy firewalls should be considered when implementing Network Security measures, and other types of firewalls, such as intrusion prevention systems and user behavior analytics, should be considered for more advanced Security needs. Additionally, it is important to regularly review and update firewall rules to ensure that they are providing adequate protection against known threats.
Next-Generation Firewalls
Next-Generation Firewalls (NGFWs) combine traditional firewall capabilities with advanced Security features, such as intrusion prevention, application awareness, and deep packet inspection. They are designed to provide more comprehensive protection against network-based threats than traditional firewalls and are commonly used in enterprise environments.
NGFWs work by examining Network traffic at the application layer of the OSI model, providing visibility and granular control over Network traffic. NGFWs can also inspect the contents of Network traffic and apply Security policies, such as blocking traffic containing specific keywords or patterns. They can also block traffic based on the specific application, protecting against application-specific attacks, such as SQL injection and cross-site scripting (XSS).
Here are some examples of Next-Generation Firewalls:
1. Palo Alto Networks Firewall
Palo Alto Networks Firewall is a hardware-based NGFW designed to provide advanced Network Security for enterprise environments. It provides a range of Security features, including application awareness, intrusion prevention, and SSL/TLS decryption.
2. Fortinet Firewall
Fortinet Firewall is a hardware-based NGFW designed to provide advanced Network Security for enterprise environments. It provides a range of Security features, including application awareness, intrusion prevention, and SSL/TLS decryption.
3. Cisco Firepower
Cisco Firepower is a hardware-based NGFW designed to provide advanced Network Security for enterprise environments. It provides a range of Security features, including application awareness, intrusion prevention, and SSL/TLS decryption.
NGFWs provide more advanced Network Security than traditional firewalls by combining traditional firewall capabilities with advanced Security features, such as intrusion prevention, application awareness, and deep packet inspection. This allows NGFWs to provide more comprehensive protection against network-based threats, such as DoS attacks, port-scanning attempts, and application-specific attacks.
However, NGFWs can still have limitations, such as the inability to detect more advanced threats, such as zero-day attacks or malware hidden within legitimate traffic. Additionally, NGFWs can be complex to configure and can introduce additional latency and performance overhead due to the need to inspect and analyze Network traffic.
Overall, NGFWs are an important component of Network Security, especially for enterprise environments that require advanced Network Security capabilities. It is important to regularly review and update firewall rules to ensure adequate protection against known threats and that the firewall is configured to provide optimal Security for the Network’s specific needs.
Limitations of NGFWs
While Next-Generation Firewalls (NGFWs) are more advanced than traditional firewalls, they still have limitations that can affect their effectiveness. Here are some limitations of NGFWs that can affect their efficacy:
1. Inability to Detect Advanced Threats
They can only inspect and analyze Network traffic and apply specific Security policies. They cannot detect more advanced threats, such as zero-day attacks or malware hidden within legitimate traffic.
2. Limited Scalability
NGFWs can become overwhelmed by high traffic volumes, reducing performance and potentially enabling attackers to bypass the firewall.
3. Complexity
Configuring can be complex and requires a thorough understanding of the applications being protected and the Security policies being enforced.
4. Performance Overhead
NGFWs can introduce additional latency and performance overhead due to the need to inspect and analyze Network traffic.
5. Limited Protocol Support
They are designed to protect specific applications and may not support all protocols used by the applications.
6. Cost
NGFWs can be more expensive than other types of firewalls, especially when considering the cost of hardware and licensing.
Overall, NGFWs are effective in some scenarios and are commonly used with other Security measures to provide comprehensive Network Security. However, the limitations of NGFWs should be considered when implementing Network Security measures, and other types of firewalls, such as intrusion prevention systems and user behavior analytics, should be considered for more advanced Security needs.
Additionally, it is important to regularly review and update firewall rules to ensure that they are providing adequate protection against known threats. It is also important to ensure that NGFWs are correctly configured and managed to ensure optimal Security and performance. Finally, organizations should consider the cost-effectiveness of NGFWs compared to other Security solutions and ensure they get the best return on their investment in Network Security.
Last Words
Overall, firewalls are an important component of Network Security and can protect against various vulnerabilities and threats. However, it is important to note that firewalls are not a comprehensive solution and should be combined with other security measures, such as antivirus software, intrusion detection systems, and user authentication mechanisms.
FAQ
What is a proxy firewall and how does it differ from basic firewalls?
A proxy firewall acts as an intermediary between clients and servers: it inspects or modifies traffic at the application level before forwarding it, providing content filtering, IP hiding, and more control than basic packet filtering.
What additional protections do Next-Generation Firewalls (NGFWs) offer?
NGFWs combine traditional firewall functions with features such as deep packet inspection, application-level awareness, intrusion prevention, SSL/TLS decryption and fine-grained policy enforcement for better defense against modern threats.
Are advanced firewalls enough to fully secure a network by themselves?
No — while they significantly improve security, firewalls should be part of a broader security strategy that includes antivirus, intrusion-detection/prevention systems, secure policies, and regular monitoring for best protection.