In today’s Cyber World, Hackers Are Constantly Updating Their Knowledge Of Vulnerabilities And Techniques That Companies And Security Experts Use To Counter Threats.
Security Expert, Due to the flood of hacker attacks on organizational infrastructures and networks, information breaches, digital frauds, and ransomware attacks, maintaining the cyber security of infrastructures is not easy.
So that in some cases, security experts resign from their jobs and go to another job because, in the event of a successful attack, the first part of the organization that is condemned and held accountable is the security department and then the network.
We must first learn cyber security’s basic and essential principles to evaluate the solutions carefully to eliminate these risks.
Also, we should seek to use strategies and techniques that provide the best results. Vulnerability, threat, risk, and security measures are essential cybersecurity terms that every security expert should know about.
Therefore, if you want to enter the world of security, I suggest you keep this magazine issue and this article as a guide, as we will cover some critical points in cyber security.
Familiarity with basic concepts
One of the first concepts a cyber security expert should know is “vulnerability.” A vulnerability is a weakness that hackers can use to gain unauthorized access to an organization’s digital assets or ordinary users.
With this access, hackers can run malicious code, install malware, distort data, or steal sensitive data. There is a subtle point about vulnerability; In most cases, vulnerabilities are essentially backdoors that programmers and software companies put in to make necessary or desirable changes to the software.
However, sometimes hackers manage to identify these backdoors and exploit them. So, as a security expert, you should check published reports about critical vulnerabilities daily so that if a patch is released for your organization’s software, download it and install it after reviewing and performing technical evaluations.
The second most important term in the security world is “Threat.” In its simplest definition, a threat refers to a malicious activity or set of activities that exploit vulnerabilities to damage, expose, or steal sensitive data or disrupt access to digital assets.
Threats are divided into different degrees, but not all are severe risks for the organization.
For example, the Windows operating system’s warning about updating or not installing OneDrive if you do not use this cloud infrastructure will not cause a particular problem.
The third important concept in the field of security is “Risk.” Risk refers to the possibility of damage or loss if hackers exploit a vulnerability. In addition, the risk is defined as the product of impact and feasibility.
“Security Measures” (Security Measures), or security controls, are strategies to reduce the risks that target the organization’s digital assets. To secure cyberspace and reduce risks, security experts and managers of the organization’s security department must use various security methods and tools to minimize threats to the lowest possible level.
Now that we have obtained general information about the fundamental concepts of the security world, it is time to get acquainted with more advanced concepts in this field, namely Vulnerability Management, Penetration Testing, and External Attack Surface Management. Then let’s examine the similarities, differences, and solutions they offer.
What is vulnerability management?
The vulnerability management process is implemented continuously to identify, evaluate, prioritize, manage, and reduce the impact of security vulnerabilities. In the above process, cyber security experts constantly scan for vulnerabilities to identify new vulnerabilities and implement security patches and necessary measures to fix them.
Typically, security experts prioritize security patches; Cyber uses vulnerability rating schemes such as Common Vulnerability Scoring System (CVSS) and Risk Calculations. In vulnerability management, the scope of each asset is defined, and no new purchase is placed beyond this scope.
An essential principle in this context is that the set of known IPs of the organization should be used to best define the range of assets. Next is identifying vulnerabilities that prevent hackers from successfully exploiting vulnerabilities.
In this context, be aware that some detected vulnerabilities may not be exploitable, resulting in the possibility of false positive detection that you should consider. Overall, vulnerability management provides real-time visibility into known assets.
What is penetration testing?
Penetration testing refers to actions aimed at simulating attacks to detect vulnerabilities that hackers can exploit and gain unauthorized access to systems or data. This test is carried out in a specific area based on certain permissions and is pre-coordinated with the organization’s management.
Like vulnerability management, penetration testing also has specific scope and permissions, but its area is more limited than vulnerability management. To be more precise, based on the previous knowledge about the system or systems to be tested, this test has different classifications, the most important of which are black box, white box, and gray box tests.
In black box testing, security experts have no information about the system. Still, in white box testing, detailed information about the system that will be simulated hacker attack is provided to security experts.
The third most effective test in this field is the gray box.
In the mentioned test, hackers may already have some access and privileges. In all these cases, penetration testers try to violate system security using tools and techniques similar to those used by hackers.
Additionally, security experts may use automated or manual tools. In all three tests, penetration testers attempt to exploit known vulnerabilities to map out detailed information about attack paths to an organization’s infrastructure.
Therefore, false positive detection is at the lowest level in the mentioned method. Cyber security experts suggest that penetration testing be repeated every six months to a year to gain a real-time view of the attack level.
Overall, penetration testing verifies the effective functioning of defense mechanisms and makes addressing known vulnerabilities and updating security policies more accurate.
External attack surface management
An attack surface refers to any nature that hackers can discover and exploit while researching the Internet about the target, which is the organization. We can reduce the attack surface by proactively mapping digital footprints, monitoring online channels for signs of attack, quickly neutralizing known threats, and protecting customers, employees, and networks.
The external attack surface management is an ongoing task that identifies and manages risks to Internet-connected assets. In the said process, all known or unknown assets in the organization, cloud environment, company subcategories, supply chain, and partners are checked from a hacker’s point of view and in a trans-organizational way. It is important to note that security experts can only reduce the attack level by viewing all assets visible to hackers.
Unlike penetration testing and vulnerability management, external attack surface management depends on accurately identifying all devices deployed in the enterprise network.
At this stage, security experts can find unknown devices.
Similar to vulnerability management, our focus is not on exploiting the findings at this stage. Hence, the range of assets includes not only what has already been identified but also undetected and new assets. Therefore, false positive diagnoses are possible, but these incorrect positive diagnoses can be ignored, considering the primary goal of achieving the whole vision.
The external attack surface monitoring covers known and unknown digital assets managed by the organization or authorized third parties. Still, the attack surface extends beyond this to include malicious or fraudulent purchases created by attackers and sensitive data disclosed by employees or customers. For this reason, in managing the external attack level, we must pay attention to the following:
- Assets that may be counterfeited and used for fraud and branding.
- It was stolen and leaked information from accounts or sensitive customer or employee data.
All in all, we must say that we can reduce the risks around digital assets to the lowest possible level through vulnerability management in identified assets.
Similarities and differences
As a cybersecurity expert, be aware that vulnerability assessment and scanning tools can be used in vulnerability management, penetration testing, and external attack surface management.
Vulnerability and external attack surface management have similar detection, assessment, prioritization, and countermeasures functions. Still, the main distinguishing feature of external attack surface management is the continuous identification of assets.
Vulnerability management and external attack surface management are ongoing activities, while penetration testing is done every six months or once a year. Hence, vulnerability and external attack surface management provide real-time visibility, not penetration testing.
In vulnerability management and penetration testing, the system is evaluated from the perspective of the internal or external network or the state between the two. Still, in external attack-level management, the system is considered from an attacker’s view or an individual outside the organization. In vulnerability management and external attack surface management, no attempt is made to exploit known vulnerabilities, but in penetration testing, evaluation is done by exploiting vulnerabilities.
In penetration testing, we can exploit vulnerabilities to identify vulnerabilities.
Therefore, positive diagnoses in this method are less than in the other two cases.
In external attack surface management, we are not limited to known assets and are tasked with finding unknown aids. Still, we do not attempt to find help in vulnerability management and penetration testing.
As you can see in Figure 1, which represents attack surface reduction, only known assets are considered in vulnerability management and penetration testing, but in external attack surface management, in addition to identified assets, unidentified assets, third party, impersonation, and stolen assets or takes into account the disclosed. A summary of the similarities and differences between the concepts discussed in this article is presented in Table 1.
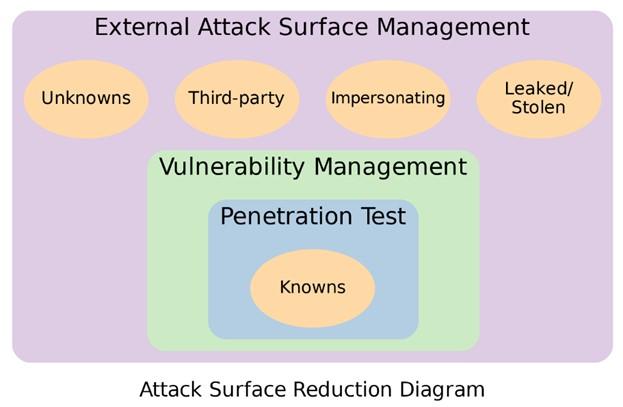
figure 1
last word
As you may have guessed, each of the methods mentioned earlier has advantages, so simultaneously applying all three is necessary to strengthen cyber security.
For example, vulnerability management focuses on known vulnerabilities. Still, penetration testing can identify unknown vulnerabilities in products used by the organization, while external attack surface management can identify undisclosed vulnerable assets.
Usually, the organization’s security department prioritizes based on the risk formula due to budget constraints, which means that the impact is multiplied by the probability.
Here, you should consider the critical point that we cannot take appropriate measures if we do not fully calculate the risk. Note that we must specify the risk score of all visible assets or items not visual in the external attack level management.
By increasing the visibility of the attack surface, the risk impact factor increases; In the sense that hackers can identify the path with the lowest level of resistance to enter the organization; therefore, the probability of attacking assets in contact with the Internet is higher.
With this description, we must say that among the above three methods, external attack surface management is the first one you should consider.