What is Tor Browser? Is it Safe to Use?
Tor Browser is a free, open-source software that protects users’ privacy and security. Using Tor, you can operate anonymously on the Internet, and rest assured that no one can track your traffic and activities.
These days, users’ awareness has increased, and they care more about their privacy. The Tor project (short for The Onion Router) is a non-profit project designed to secure users so that others, including the government and large organizations, cannot track a person’s location or behavior on the Internet.
Browsers such as Chrome, Firefox, Opera, etc., use cookies, user search history, location, etc., to improve the user experience. The same issue endangers users’ privacy if the Tor browser almost solves this problem and prevents spying on people’s traffic.
In Tor, search history and cookies are automatically deleted each time you browse the web. With this browser, no one can monitor your web browsing; all they can see is that you are using Tor. In the Tor browser, all users are the same, so tracking them is generally impossible. In this browser, you can surf the web freely without being afraid of being detected or having your access restricted to certain sites.
How does the Tor browser work?
The Tor browser uses layered encryption, and for this reason, the shape of an onion can be seen in the logo image of this browser, because the Tor encryption method works like the layers of an onion. First of all, you need to know that Tor has various servers around the world that are run by volunteers and are known as Tor relays. User traffic is encrypted in three stages. In such a way, the user’s information is encrypted each time it reaches one of these nodes, which are chosen completely randomly, and this work is repeated for two more steps. Then the information is sent to the final destination.
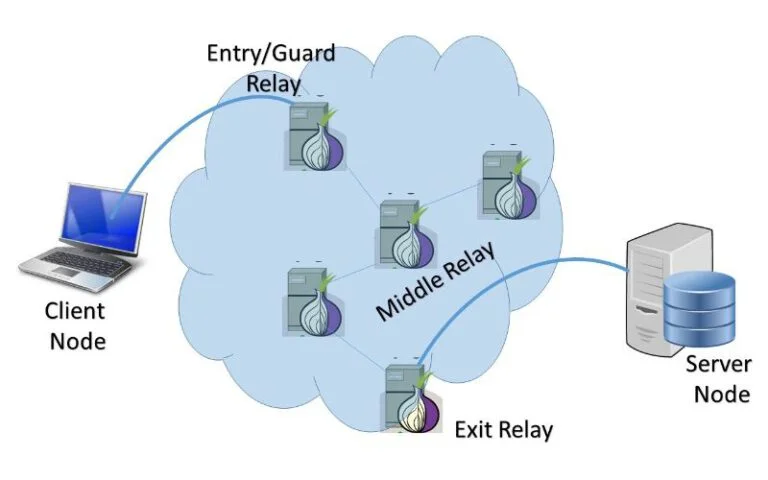
Advantages of using Tor
For those who care about privacy and are looking for a way not to reveal their identity online, using browsers like Tor is an ideal solution. Let’s review some of the advantages of Tor:
- Tor is free to use: You can download this browser completely free of charge. Tor is compatible with Windows, macOS, Unix-like systems, and Android.
- Free browsing is one of the founding principles of this browser. Tor is a distributed network. A distributed network is managed jointly or separately by its nodes, which increases the processing and storage workload and ultimately makes it difficult to track users.
- Volunteers run this network. Tour volunteers are community-minded people who help support this ecosystem. These volunteers provide their computing resources as relays, information transmitters, and support to the tour project.
- The Tor network is resistant to government interference. Because this network is a distributed network managed by a wide range of volunteers, it is difficult and impossible to destroy it because by destroying one or more relay nodes, the entire network does not fail.
What are the risks of the Tor browser?
Many practical experiences have shown that the security of the Tor browser is not perfect, and you cannot count on the safety of Tor 100%. Like any other system, the Tor browser has its weaknesses. Although security holes and information leakage holes in Tor are constantly being patched, there can never be any assurance that these patches will be released promptly. Apart from this issue, there are more reasons to worry about the safety of the Tor browser, which we will mention below.
First of all, Tour users are regularly hacked. This is usually not the fault of Tor itself; rather, these hacks occur because the user’s device is not properly protected. Hacking while using Tor Browser can happen to anyone, so all Tor users should be aware of this issue. Cybercriminals, malware, viruses, and malicious content may lurk on the pages you visit; Especially when you’re surfing the dark web. Therefore, you should always be aware of very link you click.
The second risk is that even when you use the Tor browser, you can track your activity on the Internet. Insecure exit nodes are one of the methods that can be used to track the activity of Tor browser users. The exit Node or exit node in the tour is the last place you connect to before connecting to the website or page. Whoever owns this node can see all the traffic passing through it if they want.
If this happens, the privacy of your browsing data will be destroyed (something the US National Security Agency, the NSA, has done in the past; this security agency has a huge portion of Tor’s exit nodes, and through this, the traffic, of the number Many of the users of the tour were listening). So there is practically at least one person who can directly find out about the pages visited by you. Still, one thing to note is that you usually remain anonymous in such situations. Even the owner of the outgoing node cannot find the source of the data because the data has passed through at least two other nodes before reaching it.
Is the Tor browser secure?
Tor is completely safe for the use of the average internet user. But like any other program, along with its advantages, it also has problems and vulnerabilities. In some situations, Tor is less secure than a VPN. But if you use the Tor browser with a VPN, you can be sure that your security and privacy will be preserved.
Disadvantages and vulnerabilities of Tor
Three of the biggest disadvantages of touring are:
Tor Browser opens web pages more slowly than regular browsers.
Some major web services do not serve Tor users.
Authoritarian regimes have banned the use of the Tor browser.
The Tor browser is generally secure, but it has the following vulnerabilities:
The last Tor exit node can be identified. The output node is the last node that controls the information before reaching its final destination. The information in this node is completely decrypted; if this traffic is not through HTTPS, the information is exposed to the operator who manages the output node.
Tor is vulnerable to verification attacks. Powerful entities like the NSA can compromise the anonymity of Tor users. For example, they can identify patterns by examining the relationship between input and output nodes.
Windows digital files are vulnerable. Downloading and opening Windows digital files that have DRM copyrights can compromise the identity of Tor users. The user exposes his location and identity by opening the DRM file and downloading the code. Connecting to a VPN makes the Internet service provider unaware of the user’s access to the Internet. Using unlogged Internet prevents the VPN provider from logging in. Using a VPN allows the user to choose a server in another country, which is another layer of security for the anonymity of the user’s identity and geo-restrictions.
Nodes are vulnerable during the final egress path. The security of the tour browser is based on the assumption that most tour volunteers are honest and not spying. But Tor forensic researchers have found exit nodes that try to create man-in-the-middle attacks by interfering with user traffic. Also, recent research shows some hacker intrusion techniques, from automated probing to dangerous SQL injection, have been used to steal login information.
How to use the Tor browser safely
Downloading and installing Tor Browser is as easy as any other browser, including Chrome, Firefox, and Safari. In addition to standard sites, Tor also opens .onion websites that are only accessible through the Tor network. For example, The New York Times Magazine also hosts a .onion site for those who want to read the news anonymously.
It is necessary to know that the Tor browser can hide the user’s location and identity, but its security level is still not at the VPN level. To eliminate this problem, you can use Tor and a VPN at the same time. This way, you launch the VPN service and then open the Tor browser. The advantages of this method are:
Eventually, The Tor browser provides you with a good level of security, which is increased by using a VPN. As we said before, Tor is also used to enter the dark web. According to the points mentioned in the article What is the Dark Web, when entering such sites, be careful not to click on any file or download anything not to endanger the security of the system and yourself.











