The Cybersecurity Triad, also known as the CIA Triad, is a conceptual model that describes the three fundamental principles of information security: Confidentiality, Integrity, and Availability.
Confidentiality ensures that information is accessible only to authorized individuals and is protected from unauthorized access.
Integrity refers to maintaining the accuracy and completeness of information, ensuring it remains unaltered and untampered with. Availability means that data is accessible to authorized individuals whenever needed.
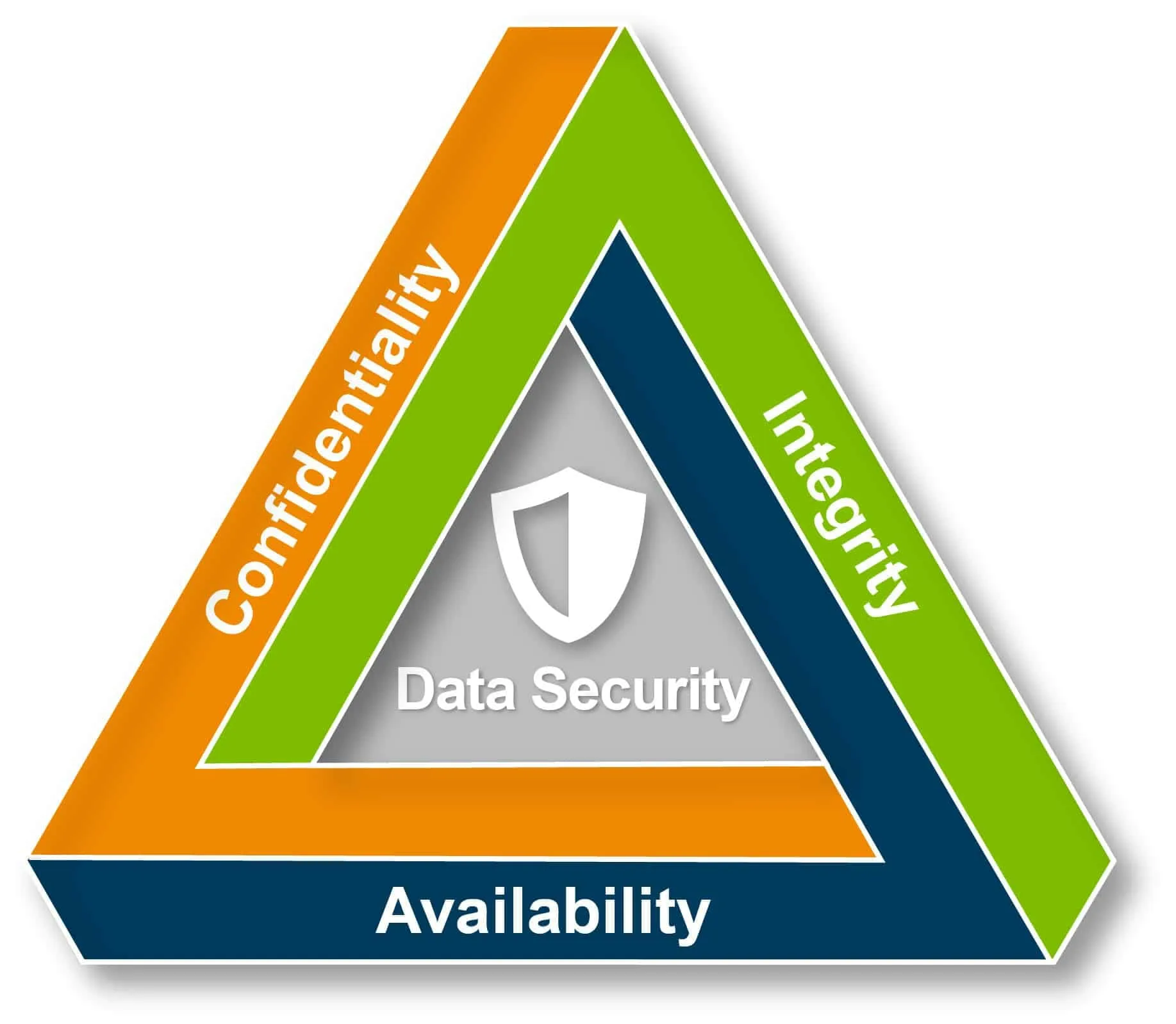
Together, these three principles form a triad, with each side representing one principle. A balance among these principles is essential for creating a robust and effective security system. For example, overemphasizing confidentiality may compromise availability, or focusing too heavily on integrity may risk confidentiality. Thus, a comprehensive security system requires a balanced approach to these principles.
The CIA Triad serves as a general framework for designing and implementing security systems, helping organizations identify strengths and weaknesses in their systems and take necessary actions to enhance security.
Additionally, the triad is used as an educational tool, simplifying and clarifying the core concepts of information security for training purposes.
It also enables organizations to communicate using a common language regarding information security and reach a shared understanding of their security needs.
In today’s world, where data volumes are rapidly increasing and cyber threats are becoming more sophisticated, securing information has become one of the most critical challenges for organizations.
The Cybersecurity Triad provides a comprehensive framework for information security, helping organizations resist these threats and protect their data.
Confidentiality: Protecting Information from Unauthorized Access
Confidentiality, one of the three pillars of the Cybersecurity Triad, refers to safeguarding sensitive information from unauthorized access. Simply, it ensures that only authorized individuals with the necessary permissions can access information.
This principle is of utmost importance, as disclosing confidential information can severely affect individuals, organizations, and nations.
To maintain confidentiality, various methods are employed, including:
- Encryption: Converts information into an unreadable format for unauthorized individuals.
- Authentication: Verifies the identity of users to ensure that only legitimate individuals access the system.
- Access Control: Determines the user’s access level to different information.
- Virtual Private Networks (VPNs): Secure data transmission over networks.
- Firewalls: Protect systems from unauthorized access.
- User Training: Educates users on security best practices.
In today’s data-driven world, with rapidly growing data volumes and increasingly complex cyber threats, the importance of confidentiality is more pronounced than ever.
Sensitive information, such as personal data, financial details, business secrets, and government records, is constantly at risk of theft and misuse. Therefore, protecting confidentiality is a top priority for organizations and governments.
Integrity: Ensuring the Accuracy and Completeness of Information
Integrity ensures that information remains unchanged and untampered since its creation or last authorized modification. This principle means that information must be accurate, complete, and reliable, with intentional changes and proper authorization.
To maintain integrity, several methods are used, including:
- Access Control: Ensures that only authorized individuals can modify information.
- Hashing: Generates a fixed-length string (hash) from variable-length input, where any change in the input alters the hash.
- Digital Signatures: Verify the authenticity and integrity of a message or document.
- Intrusion Detection Systems: Identify and prevent cyberattacks that could alter or destroy information.
Integrity is crucial today, where information is considered a valuable asset. Unintended changes to information can have serious consequences for organizations and individuals. For example, alterations to financial data can lead to monetary losses, while changes to medical records can harm individuals’ health. Thus, maintaining information integrity is a key priority for organizations and governments.
In conclusion, integrity is one of the most critical information security principles, and preserving it requires implementing appropriate security measures at all organizational levels. By adopting robust security solutions, organizations can ensure that their information remains accurate, complete, and trustworthy
Availability: Ensuring Continuous Access to Information
Availability, the final pillar of the Cybersecurity Triad, ensures that information is accessible to authorized individuals whenever needed. In simpler terms, it guarantees that systems, networks, and data are continuously available to users without interruption.
This principle is critical, as a lack of access to information can significantly harm businesses, organizations, and individuals.
Availability is essential for several reasons:
- Business Continuity: Many businesses rely heavily on their information systems, and any disruption in access can harm daily operations and lead to financial losses.
- Customer Satisfaction: Customers expect continuous access to services and products, and unavailability can result in dissatisfaction and customer loss.
- Organizational Survival: In industries like healthcare and finance, continuous access to information is vital, and disruptions can have irreversible consequences.
To ensure availability, organizations employ methods such as:
- Regular Backups: Create copies of data to restore information in case of loss.
- Server Redundancy: Use multiple servers to ensure continuous operation.
- Load Balancing: Distribute workloads across servers to prevent overload.
- Incident Detection and Response Systems: Identify and mitigate issues quickly.
Availability is fundamental to information security, and maintaining it requires robust security measures across all organizational levels.
By implementing solutions to enhance availability, organizations can ensure that their information is always accessible to authorized users, allowing their operations to continue uninterrupted.
Example of Applying the Cybersecurity Triad in Computer Network Security
The Cybersecurity Triad, with its three pillars of confidentiality, integrity, and availability, provides a comprehensive framework for evaluating and improving the security of computer networks. For example, in a financial organization, the triad can be applied as follows:
- Confidentiality: Customers’ financial information, such as account numbers and transaction histories, is among the most sensitive data for a financial organization. To protect confidentiality, the organization uses strong encryption to secure data during transmission, two-factor authentication for internal system access, and precise access controls to determine which users can access specific information. These measures ensure that only authorized individuals can access sensitive data, preventing unauthorized disclosure.
- Integrity: In a financial organization, integrity means that customers’ financial information must be accurate, complete, and reliable, with any changes made intentionally and with authorization. To maintain integrity, the organization uses data hashing to verify that information has not been altered during transmission, digital signatures to confirm the authenticity and accuracy of data, and intrusion detection systems to identify and prevent attacks that could change or destroy information.
- Availability: In a financial organization, availability ensures customers can access online banking services continuously and without interruption. The organization maintains availability through regular data backups, server redundancy, load balancing across servers, and incident detection and response systems. These measures ensure that services can be quickly restored in case of technical issues or cyberattacks, allowing customers to continue their activities.
Overall, the Cybersecurity Triad helps financial organizations adopt a comprehensive approach to protecting sensitive information. Given the importance of economic data, maintaining confidentiality, integrity, and availability is a top priority for these organizations.
The Hackers Triad (DDD): Countering the Cybersecurity Triad
In contrast to the Cybersecurity Triad, which focuses on preserving confidentiality, integrity, and availability, hackers use a three-part model for their attacks, known as the DDD Triad. DDD stands for Disclosure, Destruction, and Denial, with each side representing a different hacker objective.
- Disclosure refers to the exposure of confidential information. Hackers infiltrate systems, steal sensitive data, and then publish or exploit it.
- Destruction: Involves disrupting or damaging systems, rendering them inoperable. By attacking servers, networks, or other IT infrastructure, hackers can cause significant harm to businesses and organizations, leading to data or service loss.
- Denial refers to denying responsibility for an attack or creating uncertainty about its source. Hackers use techniques like concealing their tracks or using anonymizing tools to avoid detection and shift blame.
The DDD Triad is essentially a mirror image of the Cybersecurity Triad, with each side countering one of the CIA principles: disclosure opposes confidentiality, destruction opposes integrity, and denial opposes availability.
Understanding the DDD Triad helps organizations better identify cyber threats and implement appropriate preventive measures. By recognizing hackers’ objectives, organizations can pinpoint vulnerabilities in their systems, address them, and enhance their information security.
Differences Between CIA and DDD: Two Sides of the Cybersecurity Coin
The CIA and DDD models are distinct yet complementary in cybersecurity. CIA (Confidentiality, Integrity, Availability) takes a defensive perspective, focusing on protecting information from external threats. Its goal is to secure information by preventing unauthorized access, ensuring data accuracy and completeness, and guaranteeing continuous access for authorized users.
In contrast, DDD (Disclosure, Destruction, Denial) adopts an offensive perspective, representing hackers’ standard methods to attack systems. Hackers aim to expose confidential information, disrupt systems, and evade responsibility for their actions.
In simple terms, if the CIA Triad represents the shield organizations build to protect their information, the DDD Triad represents the tools hackers use to break through that shield.
Both models provide a complete picture of the cybersecurity landscape, and understanding both is essential for organizations and security professionals.
Understanding the CIA Triad allows organizations to implement measures to safeguard their information, while understanding the DDD Triad will enable them to identify and mitigate system vulnerabilities.
This dual understanding enables organizations to become more resilient against cyberattacks and better protect their information.
FAQ
What is the cybersecurity triad?
It refers to the three core principles of security: Confidentiality, Integrity, and Availability.
Why is Confidentiality important?
It ensures that sensitive information is accessed only by authorized users.
What does Availability mean in security?
It means systems and data are accessible and functional when needed by authorized users.