One of the most important tasks of network experts is monitoring the Performance Of Employees And The Equipment That Exchanges Information.
There are various tools and solutions for monitoring the activity of nodes under a network. Still, switches have port symmetry that uses a port or virtual LAN to receive packets.
Port Mirroring is a feature provided by management switches. It is an efficient feature that allows you to monitor the traffic exchanged by a network node closely without reducing network performance.
What is Port Mirroring?
When we want to obtain information about intrusion prevention, intrusion detection, and traffic monitoring systems of network equipment and use solutions like NetFlow in this field, we must first send the traffic to the analytics software to interpret the intended traffic.
The best way to get real-time traffic at the lowest possible cost from network equipment, especially switches, is to use the Port Mirroring solution.
Port Mirroring is one of the most important features provided by switches, indicating the port monitoring principle. Network administrators use this feature to detect errors and problems and review client activities.
The above feature allows you to receive a copy of the information exchanged by the switch or, if necessary, direct the full traffic of a local network to a specific port of the switch so that the analytics software can interpret the traffic.
The above feature has two crucial advantages: first, it allows you to troubleshoot without making the network inaccessible, and second, it enables you to accurately track the traffic the system exchanges if you have highly suspicious client activity.
Port Mirroring A network switch sends a copy of packets sent by a node or a VLAN. Switch manufacturers use different names to describe Port Mirroring.
For example, Cisco switches use the RSPAN term Remote Switched Port Analyzer or Switched Port Analyzer. Other vendors use other names, such as RAP Roving Analysis.
Port Mirroring helps network administrators closely monitor network performance and identify causes of problems by receiving a copy of incoming or outgoing traffic through a port. Port Mirroring: A network switch is used to send a copy of the packets sent by a node or a VLAN.
Switch manufacturers use different names to describe Port Mirroring. For example, Cisco switches use the RSPAN term Remote Switched Port Analyzer or Switched Port Analyzer.
Other vendors use other names, such as RAP Roving Analysis.
Port Mirroring helps network administrators closely monitor network performance and identify causes of problems by receiving a copy of incoming or outgoing traffic through a port.
Port Mirroring A network switch sends a copy of packets sent by a node or a VLAN. Switch manufacturers use different names to describe Port Mirroring.
For example, Cisco switches use the RSPAN term Remote Switched Port Analyzer or Switched Port Analyzer. Other vendors use other names, such as RAP Roving Analysis.
Port Mirroring helps network administrators closely monitor network performance and identify causes of problems by receiving a copy of incoming or outgoing traffic through a port.
For example, Cisco switches use the RSPAN term Remote Switched Port Analyzer or Switched Port Analyzer.
Other vendors use other names, such as RAP Roving Analysis.
Port Mirroring helps network administrators closely monitor network performance and identify causes of problems by receiving a copy of incoming or outgoing traffic through a port. For example, Cisco switches use the RSPAN term Remote Switched Port Analyzer or Switched Port Analyzer.
Other vendors use other names, such as RAP Roving Analysis. Port Mirroring helps network administrators closely monitor network performance and identify causes of problems by receiving a copy of incoming or outgoing traffic through a port.
How is Port Mirroring different from NetFlow?
Some users think Port Mirroring and NetFlow have the same functionality, but this is not true. In NetFlow, the network administrator receives metadata from the network and never gets the original information.
To be more precise, the original data is deleted. For the traffic monitoring software, only the metadata containing the general and ancillary information of the packets is sent. In contrast, in Mirroring, all the packets are exchanged by the equipment and are entirely sent to the specified port.
For this reason, it is possible to analyze the information’s content. The technique is known in Cisco switches as SPAN or RSPAN, the first mode for eavesdropping on the local area network and the second for remote eavesdropping.
Port Mirroring allows network administrators to analyze data, debug networks, analyze network performance, and fix problems quickly.
Port Mirroring allows the ability to receive inbound (Ingress) and outbound (Egress) traffic. However, in most cases, only inbound traffic is analyzed.
This traffic can be received from a specific switch port or all of a switch’s connections. Port Mirroring is typically used in conjunction with the Port Scanner.
Port Scanner is a program used to identify a server or host’s open ports. It helps managers evaluate network security policies and ensure no unknown vulnerabilities can be misused to access network services. Port Mirroring is typically used in conjunction with the Port Scanner.
Port Scanner is a program used to identify a server or host’s open ports. It helps managers evaluate network security policies and ensure no unknown vulnerabilities can be misused to access network services. Port Mirroring is typically used in conjunction with the Port Scanner.
Port Scanner is a program that identifies a server or host’s open ports. It helps managers evaluate network security policies and ensure no unknown vulnerabilities can be misused to access network services.
What is SPAN?
Cisco switches have a SPAN feature, which receives traffic from a specific physical port or virtual local area network. Cisco switches’ SPAN technology allows network administrators to specify the source and destination addresses whose traffic must be received and forwarded to another port on the same switch.
In this case, the source node defined in SPAN refers to a physical port or a virtual local network on the switch on which the monitoring process is performed.
In addition, the destination port must be on the same switch. Once configured, SPAN Source traffic is sent to the SPAN Destination. If the traffic must be received from another switch and the destination is a remote switch, the Remote SPAN technique is used.
For RSPAN to work correctly, a dedicated virtual local area network (VLAN) must be assigned to the RSPAN to allow the monitored traffic between the source and the switch to pass through.
What is RSPAN?
The policies for RSPAN Source are similar to those for SPAN Source. The source must have at least one physical port or VLAN on the switch.
The main difference between RSPAN and SPAN is the destination, which in RSPAN does not need to be the destination of one port on the same switch, but can be defined on another switch.
In this case, to implement RSPAN, we create a dedicated VLAN called RSPAN VLAN. This VLAN contains the ports defined in the source and destination switches.
How does SPAN work?
Network administrators can analyze traffic using SPAN or RSPAN via a port or virtual LAN and send a copy to another port on the switch. The network analyzer, monitoring tools, or other security solutions are connected… SPAN intelligently sends incoming or outgoing traffic from the source port or virtual local area network to the destination port for detailed technical analysis.
SPAN works by not changing the traffic pattern of the source port or VLAN. In this case, the destination port receives only the traffic required for SPAN or RSPAN sessions.
One thing that some network experts do not know much about is how to do this process. For example, if you monitor incoming traffic, you can not monitor traffic being transferred from one third-party LAN to another. However, you can monitor the traffic that the third-party VLAN sends to the destination VLAN.
In addition, it is possible to use SPAN or RSPAN destination ports to enforce security policies.
For example, if a Cisco intrusion detection system is connected to the target port, the IDS device can send a TCP reset packet to close the TCP session that is suspected of being attacked.
The SPAN feature is generally designed for switches because hubs do not require this feature. When a hub is installed on a network, and a node in the network sends a packet, the packet is sent to all the hub ports, but the switches manage the packet sending process based on the node address or physical address of the nodes.
In this case, the switch searches in the meta-address table to reach the packet sent by the source node to the destination. Figure 1 shows how a hub sends the packet it receives to other devices on the network.
A network eavesdropper can monitor network traffic since the hub sends the input packet to all ports.
figure 2
To be more precise, the hub distributes packets based on the all-distribution approach, which allows the listening and monitoring devices to receive traffic. In contrast, the switch distributes packets based on the single-distribution approach. Fortunately, network monitoring tools can receive and analyze all-broadcast, single-broadcast, multi-broadcast, and single-broadcast traffic.
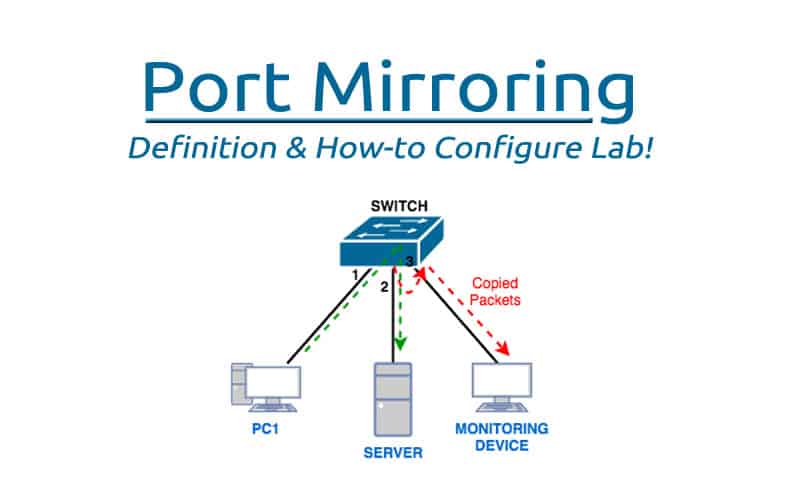
Norm, Ally, when a client connected to a switch (e.g., computer B) sends a packet, it depends on the port. It reaches the destination, but port traffic to a particular client is delivered when the Port Mirroring feature is enabled on the switch.
Consider (computer A, for example). When computer A sends packets to nodes on the network, a copy of the information is sent to the port and the computer that will evaluate the packets (computer D, for example).
Figure 3 shows how the switch works in normal mode and Port Mirroring. As you can see in Figure 3, the switch sends the traffic switch only to the destination it finds, so the SPAN feature on Cisco switches or Port Mirroring on other switches must enable access to the forwarded traffic.
When the above feature is enabled on the switches, a copy of the traffic is sent to the listening port (Figure 4).
Figure 3
Figure 4
Local SPAN
Local SPAN fully supports a SPAN session on a switch. In this case, all the source ports or the source and destination ports are on the same switch or switch stack. Local SPAN copies the traffic of one or more source ports in each virtual network or LAN to the destination port for analysis.
For example, in Figure 5, the traffic of port 5 (source port) is sent (ported) to port 10 (destination port). The network analyzer in port 10, instead of physically connecting to port 5 and receiving the information, logically receives any network traffic exchanged through port 5.
Figure 5 shows the Local SPAN configuration on a switch. If you need to implement Local SPAN on a set of switches, where the source and destination ports are located on different switches, the configuration is shown in Figure 6.
RSPAN supports source ports, virtual source LANs, and destination ports on multiple switches (or stacks of switches), so remote monitoring of various switches on the network is also possible.
Figure 7 shows how the source ports are configured on switches A and B.
Traffic for each RSPAN session is routed through an RSPAN VLAN specified by the network administrator.
RSPAN traffic is copied from the source port or virtual local network to the RSPAN VLAN and sent to the relevant session via the RSP VLAN host relay port.
In the above method, each RSPAN source switch must have a port or a virtual local area network as the RSPAN source. In Figure 7, switch C is selected as the destination. SPAN is configured in two modes: Local SPAN and Remote SPAN, using the following commands:
Figure 5
Figure 6
Figure 7
Local SPAN:
Switch (config) # monitor session 1 source interface fast 0/1 – 3
Switch (config) # monitor sessionone1 destination interface fast 0/4
Remore SPAN:
Source Switch:
Switch (config) # vlan 30
Switch (config-VLAN) # remote-span
Switch (config) # monitor session 1 source interface fast 0/1 – 3
Switch (config) # monitor session one destination remote vlan 30 reflector-port fast 0/24
Destination Switch:
Switch (config) # monitor session one source remote VLAN 30
Switch (config) # monitor session one destination interface fast 0/10
FAQ
What is port mirroring in networking?
Port mirroring is copying network traffic from one port to another for monitoring or analysis.
Why is port mirroring used?
It helps administrators analyze traffic, troubleshoot issues, and detect security threats.
Does port mirroring affect network performance?
It can impact performance if not configured properly, especially on busy network switches.