Pegasus Is Used To Monitor Cyberspace Nationwide. What Is Pegasus And How Does It Work? Can You Protect Yourself? Cyber Surveillance By Government-Sanctioned Cyberspace Re-Emerged After The Guardian And 16 Other Media Outlets Exposed How Commercial Malware Was Used By Authoritarian Regimes To Target Activists, Politicians, And Journalists.
What is Pegasus?
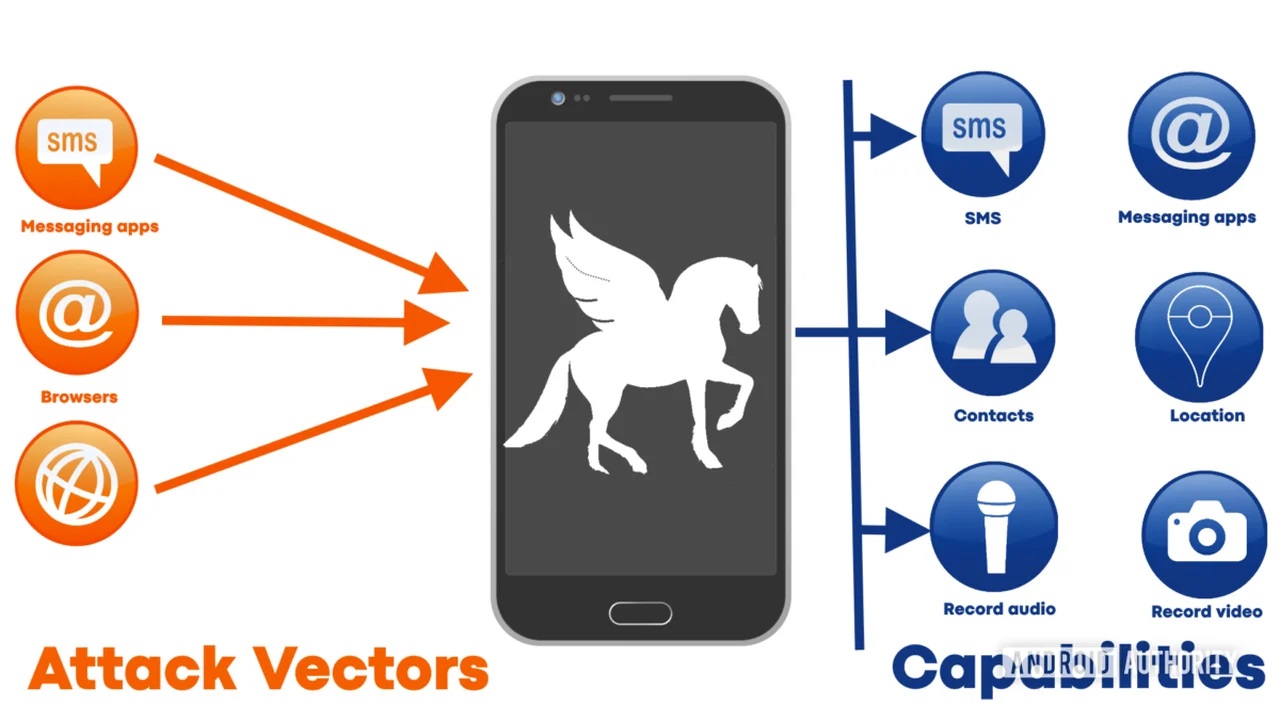
The commercial malware in use is called Pegasus and was sold for millions of dollars by an Israeli company called NSO Group. Join us today at Meg Hardware to talk about the dangerous spy Pegasus. Pegasus, known as the most sophisticated malware, can record calls, copy messages and secret videos from the owner (and close people) on any exposed device.
In short, Pegasus is dangerous commercial spyware. Unlike malware used by cybercriminals to make money by stealing and cheating their victims, Pegasus is only designed to spy.
When it secretly infects a smartphone (Android or iOS), it can become a full-fledged monitoring device. Messages, emails, WhatsApp messages, iMessages, and more are all open for reading and copying.
This program can record incoming and outgoing calls and also steal all the photos of the device.
In addition, it can activate the microphone and/or camera and record the said items. When you combine this with the potential for access to past and present location data, it is clear that those who listen from there know almost everything about the target person.
You should know that if a government agency targets you with software like Pegasus, which is a very dangerous spy, and you insist on keeping your smartphone, you will not be able to do anything unless you take away your mobile phone. Drop it.
Early versions of Pegasus have been around since 2016, so this is nothing new. However, from its earliest days, its capabilities and complexities have grown tremendously. Not everyone can afford a copy of Pegasus – this is not something that can be sold on eBay or even on the dark web. The NSO Group only sells it to governments, and it costs millions of dollars to buy it.
Fortunately, this means that it is not in the hands of delinquent groups, cybercriminals, or terrorists.
In fact, the NSO Group promotes Pegasus as “technology that helps government agencies prevent and investigate terrorism and crime to save thousands of people around the world.” It seems extraordinary, and just that being “government” is no guarantee of character, morality, and self-control.
Some governments that use Pegasus to target journalists, business leaders, religious leaders, academics, and union officials include Hungary, Mexico, Saudi Arabia, India, and the United Arab Emirates.
The NSO Group acknowledges that it has more than 40 countries on its list of real customers but says in its defense that it is destroying its customers’ human rights records.
He also points out that Pegasus cannot be used for cyber-surveillance in the United States and that no foreign customer has ever used technology to access US-owned phones. ”
0-day vulnerability
All software has errors called bugs. This is a fact. It is also a fact that the number of bugs is directly related to the complexity of the software. More code means more bugs. Most bugs are just annoying. Something in the user interface that is not working as expected.
A feature that does not work properly under certain conditions. The developers will fix the most obvious and annoying bugs in later versions. There are bugs in games, in operating systems, in Android apps, in iOS apps, in Windows apps, in Apple Mac apps, in Linux – basically everywhere.
Unfortunately, using open-source software is not a guarantee of a flawless experience. All software has bugs. Sometimes using open source actually makes the problem worse.
Because most key projects are done by a small group (or even a single individual), who work on these projects with more effort after arriving home from their normal jobs, recently found three security issues in the Linux kernel that had been there for 15 years!
And these are the security issues that are the main issue.
The user interface has a problem, and it is fixed; it is not a problem. But when a bug can weaken computer security, the situation becomes serious. These bugs are so serious that Google has a reward plan for people who may find security vulnerabilities in Android, Chrome, or Google Play. It rewards them for finding these security issues. In 2020, Google paid $ 6.7 million in rewards. Amazon, Apple, and Microsoft all have similar plans.
While large technology companies pay millions of dollars to fix these security bugs, many unknown vulnerabilities lurking in Android, iOS, Windows, macOS, and Linux. Some of these vulnerabilities are 0-day vulnerabilities – a vulnerability known to a third party but not known to the software developer. This is called 0-day because the author had zero days to fix the problem.
Software like Pegasus, which is a very dangerous spy-like other malware writers, iPhone jailbreakers, and those who root Android devices, are exposed to 0-day vulnerabilities. 0-day vulnerabilities are not easy to find, and they are even more difficult to exploit.
Nevertheless, it is possible.
NSO Group has a specialized team of researchers who review and analyze the details of operating systems such as Android and iOS every minute to find vulnerabilities. These vulnerabilities then become a way to build a device by bypassing all normal security. The ultimate goal is to use 0 days to achieve and privilege control over a device.
The ultimate goal is to use 0 days to achieve complete control over a device. After gaining control, the door is open to allow Pegasus, the dangerous spy, to install or replace system programs, change settings, access data, and activate sensors that are prohibited without the explicit consent of the device owner. . An attack path is required to use the 0-day bugs. A way to use to log in. These attack paths are often links sent in SMS or WhatsApp messages.
By clicking on the link, the user will take to a page that is the initial shipment.
The shipment has one task: to try to exploit the 0-day vulnerability. Unfortunately, there are also uses with zero clicks that do not require user interaction at all.
For example, Pegasus actively exploited iMessage and Facetime bugs during 2019, which means that it can only install itself on the phone by contacting the device.
One way to evaluate and estimate the size of the 0-day problem is to look for cases. Because we do not know what was found. Android and iOS both share a fairly equal share of reported security vulnerabilities. Commonly disclosed cybersecurity vulnerabilities are assigned Common Vulnerabilities and Exposures (CVE). For 2020, Android 859 surrounds CVE reports.
iOS had fewer reports, for a total of 304 reports. However, out of these 304 cases, 140 are allowed to execute unauthorized code, and more than 97 are for Android. Four reports were for iOS ratings, while three were for Android ratings. The point is that neither Android nor iOS are inherently secure and are not immune to 0-day vulnerabilities.
Protection against spyware
The hardest and most impractical thing to do is to put your phone away. If you are really worried about espionage, do not allow the authorities to access what they want. If you do not have a smartphone, Pegasus has nothing to attack.
A slightly more practical approach might be to leave your phone at home when going out or going to sensitive meetings. It would help if you also made sure that others around you do not have smartphones. You can also disable things like your smartphone camera, as Edward Snowden did well in 2016.
If all of this sounds like a lot, you can take practical steps. However, you should know that if a government agency targets you with software like Pegasus, which is a dangerous spy, and you insist on holding your smartphone, then there is not much you can do to stop it.
The most important thing you can do is keep your phone up to date.
For Apple users, this means always installing iOS updates as soon as they become available. For Android users, this means first selecting a brand that has a good track record of releasing updates and then always installing new updates if available. If in doubt, choose Google, as they tend to get the fastest updates.
The most important thing you can do is keep your phone up to date. For Apple users, this means always installing iOS updates as soon as they become available. For Android users, this means first selecting a brand that has a good track record of releasing updates and then always installing new updates if available.
If in doubt, choose Google, as they tend to get the fastest updates. Secondly, never, and I mean never, never click on a link sent to you by someone unless you are 100% sure, without a doubt, this is the original and safe link. If there is even a slight doubt, do not click on it.
Third, if you are an iPhone user, do not think that you do not have immunity. Pegasus targets iOS and Android.
As mentioned above, in 2019, there was a time when Pegasus was actively exploiting Facetime vulnerabilities that allowed it to install itself on iOS devices without detection.
Finally, be vigilant but calm and stubborn. This is not the end of the world (yet), but ignoring it will not help. You may not think you have something to hide, but what about your family members or friends?
Journalists, business executives, religious leaders, academics, and union officials are not so rare in a group that they have no friends or family. As the motto of World War II put it: “Sink the weak edges of ships.