Malwares are any software intentionally designed to harm a computer, server, user, or computer network (as opposed to a software bug, which is software that causes unintentional damage, such as to It is the cause of a defect).
Many types of malware include computer viruses, worms, Trojan horses, ransomware, spyware, adware, rogue software, erasers, and scareware.
Malwares, an abbreviation of malicious software, refers to any malicious software designed and developed by a saboteur or a hacker. There are different types of malwares, and they can be dangerous for the networks of organizations, personal computers, and even servers.
It is better to prevent malware from entering the system or network using different solutions, but what should be done in case of infection? What harm will this contamination cause? With the advancement of science and the increase in the power of malware, has the antivirus capability also increased? Are networked systems standing up to these threats with bare hands? Stay with us until the end of the article to answer these questions.
List of article titles
- What is malwares?
- Types of malwares and how each one works
- What is Malwares Prevention and Advanced Malware Protection (AMP)?
- How to clean the system from malwares?
- How to identify malwares?
- What are the best ways to hide malware?
- What is the purpose of malwares analysis?
Conclusion
What is malwares, and why is it created?
As mentioned at the beginning of the text, malware is a type of software designed and built with malicious goals to disrupt the system’s functioning, steal information, extort and blackmail the victim, etc. Malwares is created from the combination of the two words malicious and software, which in the computer world with the name malwares, which means malicious software, creates excellent problems for organizations and individuals.
The extent that today, a large number of significant security and technology companies have been established and developed to deal with this type of cyber attack. Malware may differ in design and programming from another.
The reason for this is the vandal’s purpose in making it. A hacker can break into a vast organizational network to design malware to enter the network by disrupting the system’s function. Or even by encrypting the sensitive information of a personal computer, extorting the victim, and returning the data in exchange for payment.
In every society, there is a possibility of a saboteur and one or several destructive agents. Computer networks, the largest of which is the Internet, are no exception to this rule. It may not be possible to name a fixed reason for the emergence of malware. Still, to steal information and earn money from this method, hackers have designed and developed many malware, such as viruses, worms, ransomware, Trojans, etc., which threaten the computer community. Types of malware and how each one works
Depending on a hacker’s goal, his tools may vary, and the malwares he designs and programs may play different roles. For example, a hacker intends to spy and steal information. As a result, by creating spy malwares from the target computer, he sends the information to the intended destination without disrupting the system’s performance. Or another vandal, by designing a specific malware, wants to infect a more comprehensive network of computers and finally earn money by selling an antivirus made by him.
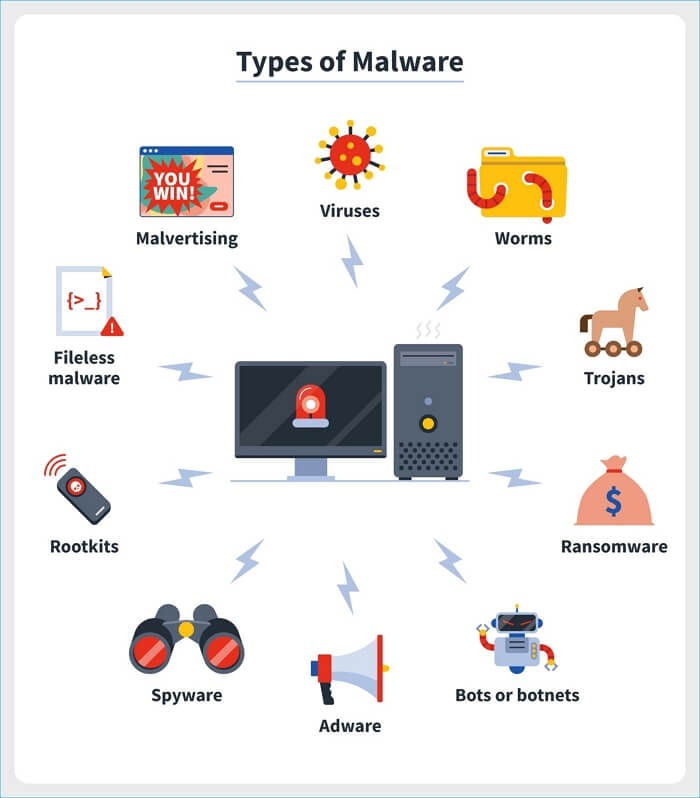
Therefore, different types of malware can be found based on the other elements a hacker has in mind. In the following, we will review 12 of the top malwares introduced.
- Virus
- Worms
- Trojan virus
- Spyware
- Adware
- Ransomware
- Fileless malware
- Botnet malware
- Rootkit malware
- Wiper malware
- Key logger malware
- Digital currency malware
Each malwares targets the computer system in a specific way that may be easy or difficult to eliminate.
Types of malware and how to deal with them

Malicious software gives complete control of the system to the attacker who created the malwares.
Types of malwares
- Virus
A virus is a program that creates copies of itself and inserts these copies into other computer programs, data files, or the challenging boot sector. Viruses then cause harmful activity on the infected host, such as stealing hard disk space or CPU time.
- Worm
A worm is a type of malware that leaves a copy of itself in the memory of any computer in its path.
- Trojan – Trojan
Trojans appear to be simple and safe software, but they are a type of malware that contains malicious code, and their execution leads to the loss or theft of information or possible system damage.
- Trojan virus – types of malware and how to deal with them
- Trojan virus – types of malware and how to deal with them
Adware – advertising software - Rootkit
Rootkits are software a hacker uses to gain administrator-level access to a computer/network installed through a stolen password or exploit a system vulnerability without the victim’s knowledge.
Ways to deal with malwares
To fight against malware and malware, the following actions can be taken:
Make sure the operating system and applications have up-to-date patches.
Never open strange emails, especially those with attachments or attachments that invite you to do something like click a link.
Be careful of the programs you download from the Internet. Do not immediately click OK on any window that opens for you and read its text before clicking on any button.
Install antivirus software.
Make sure you scan and update your antivirus programs regularly.
Install a firewall on your system.
Always enable and use security features provided by browsers and applications.
Anti-malware software
The following anti-malwares software helps to remove malicious software from the system:
- Microsoft Security Essentials
- Microsoft Windows Defender
- AVG Internet Security
- Spybot – Search & Destroy
- Avast! Home Edition for personal use
- Panda Internet Security
- MacScan for Mac OS and Mac OS X
- final word
In this session, we discussed the types of malware and how to deal with them in security testing; Viruses, worms, trojans, adware, etc, are types of malware. In addition to familiarizing ourselves with malware, we learned how to deal with malware.
Government has a new malware warning for users.
CERT-In has reported a new malware that’s affecting Android devices. The government has reported that a new Android malware named Daam is spreading and can steal sensitive data, bypassing antivirus programs and deploying ransomware on the targeted devices.
What is Daam Android malware?
According to the official post, Daam malware is communicating with various Android APK files to infect the device. It is distributed through third-party websites or applications downloaded from untrusted/unknown sources.
How does it affect Android devices?
As per the report, once Daam infects an Android device, the malware tries to bypass the security check of the device.
After a successful attempt, it attempts to steal sensitive data and permissions such as reading history and bookmarks, killing background processing, reading call logs, etc. It can also hack call recordings and contacts, gain access to the camera, modify device passwords, capture screenshots, steal SMS, download/upload files, etc., and transmit to the C2 server from the victim’s device.
It uses the AES encryption algorithm to encrypt files in the victim’s device. Then it deletes other files from local storage and leaves the encrypted files with a .enc extension and a ransom note — readme now.txt.
How to protect your device from this virus
The government body has listed a couple of guidelines for users that may help them prevent something like this from happening.
- Limit your app downloads to official app stores like your device’s manufacturer or operating system app store to reduce the risk of downloading harmful apps.
- Before downloading/installing apps on Android devices, review the app details, number of downloads, user reviews, comments, and additional information section.
- Verify app permissions and grant only those relevant to the app’s purpose.
- Avoid checking the “Untrusted Sources” checkbox to install side-loaded apps.
- Install Android updates and patches as soon as they become available from the device vendors.
- Exercise caution while browsing untrusted websites or clicking on links in unsolicited emails and SMS messages.
- Install and regularly update anti-virus and anti-spyware software on your device.
- Watch out for suspicious numbers that don’t look like real mobile phone numbers, as scammers often mask their identity using email-to-text services.
- Conduct thorough research before clicking on links provided in messages, using websites that allow you to search based on a phone number for relevant information.
- Only click on URLs that indicate the website domain, and if unsure, search for the organization’s website directly using search engines to ensure legitimacy.
- Consider using safe browsing tools, antivirus software with filtering tools, and content-based filtering services to enhance your online safety.
- Be cautious of shortened URLs, such as those using services like bit.ly and TinyURL. Hover over the shortened URL or use a URL checker to see the full website domain before visiting.
- Look for valid encryption certificates indicated by a green lock in the browser’s address bar before providing sensitive information.
- Report any unusual account activity immediately to the respective bank with relevant details for further action.