Data masking is the process of hiding original data. Its main purpose is to hide sensitive data, such as personal data stored in the original database.
The critical point, however, is that data remains usable in data masking. Data masking is the process of hiding original data. Its main purpose is to hide sensitive data, such as personal data stored in the original database. The important point, however, is that data remains usable in data masking.
What is data masking?
Data masking means covering or obscuring data. This method is a trick to create fake copies of the organization’s original data that, although counterfeit, still look real.
Among its goals, we can mention protecting sensitive data and creating valuable data when we do not need the original data (for example, when the data is necessary for training, software testing, program demo sales, etc.).
The Data Masking process changes the amount and value of the data while preserving the Format so that this created version of the data cannot be detected using decryption or reverse engineering. There are several ways to change the data, which we will explain below.
Why and when to use Data Masking?
One of the most important reasons organizations turn to Data Masking is to solve many security problems, such as data loss, data theft (Data Exfiltration), and …. Other reasons for using this security method include reducing the risks of using the cloud, rendering data unusable for hackers (while many intrinsic properties of the data have been retained), and allowing data to be shared with authenticated users.
Identified (for example, for testers, developers, etc.) without disclosing the original data, the data is erased (in fact, even when it deletes the data, a trace of it remains, which is a reason for the possibility of data recovery. Data structuring means that masked data replaces accurate data.
Sometimes, an organization needs to allow external resources and third-party IT organizations to use its databases. In this case, you need to ensure the security of the data so that, for these people and even hackers, the data looks completely real and not suspicious.
Sometimes, an organization needs to reduce its operators’ errors. Organizations often rely on their employees to make the right decisions, yet many shortcomings result from human error. If data is masked in a certain way, it can reduce catastrophic mistakes.
Data masking can benefit organizations that work with sensitive data, such as user identification information (PII), personal medical information (PHI), personal account and bank card information (PCI-DSS), intellectual property information (ITAR), etc.
Types of Data Masking
Data masking is used in several different ways to maintain data security, including Static, Deterministic, On-the-Fly, and Dynamic Data Masking. We will explain each one in the following.
Static Data Masking
This way, you can have a copy of the deleted database. During this process, virtually all sensitive data is modified to create a copy of the database we can share with Security.
In this method, we usually first take a copy of the database as a backup, load it in a different environment, delete all the extra information, and then mask the remaining data. The masked data can now be moved to the target point.
Deterministic Data Masking
In this method, we have two sets of data of the same type and Format, one of which is always replaced by another. For example, anywhere in the database, the name “John Smith” is always replaced by “Jim Jameson.”
On-the-Fly Data Masking
This method masks data when data is transferred from production systems to test or Development systems and has not yet been saved on disk.
Organizations that deploy software quickly can not make a backup copy of the source database and apply data masking to it. They need to stream data from production to multiple test environments constantly.
In the On-the-Fly method, each part of the needed masked data is sent. Each part of this masked data is then stored in a test or development environment for use by a non-productive system.
Dynamic Data Masking
This method is almost identical to the on-the-fly method, except that the data is not stored in any secondary point, such as the test or development environment. In other words, the data is sent directly from the production system as a stream for system consumption in the test or development environment.
Data Masking Techniques
Organizations can mask their sensitive data using various techniques, and here are some of the most commonly used techniques.
Data Encryption
When cryptographic algorithms mask data, the user is virtually unable to use it without a key. This technique is the most secure form of data masking, but it is difficult to implement because we need data encryption technology and a secure key-sharing mechanism.
Data Scrambling
This technique is very simple and only randomly replaces all the characters in the phrases. For example, a number like 76498 changes to 84967. Although this technique is very simple, it is not possible to use it on all data, and of course, its security is not very high.
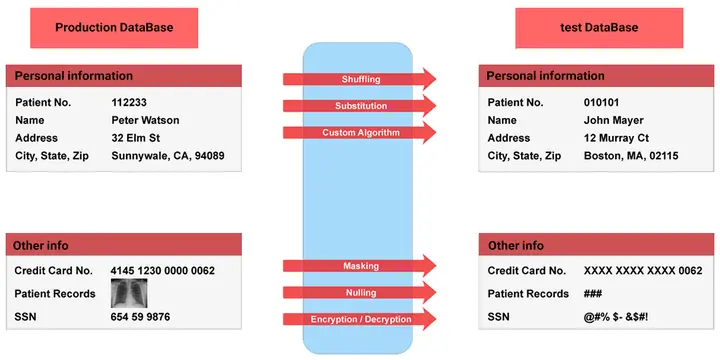
Nulling Out
In this method, when the user makes unidentified data requests, the value Null (data that has no value or is lost) is displayed to them. The disadvantage of this method is that less data can be used for testing and development.
Value Variance
In this case, the original data value is replaced using a function (for example, the difference between the maximum and minimum values in a series).
For example, if a customer has purchased multiple products, we can replace the purchase price with the average cost of the most expensive and cheapest products they bought.
While this technique does not disclose the original data, it provides us with very useful information that we can use for various purposes.
Data Substitution
This method replaces the original data value with false but true values. For example, we randomly replace customer names with several names in a phonebook.
Data Shuffling
This method is very similar to Data Substitution, except that data from the same database replaces the data in a database. The order of the data in each column changes. In the end, the output from this database looks entirely accurate, but the records are not.
The best data masking tools
- Among the best Data Masking tools, we can mention the following:
- DATPROF – Test Data Simplified
- Microsoft SQL Server Data Masking
- Oracle Data Masking and Subsetting
- IBM InfoSphere Optim Data Privacy
FAQ
What is data masking?
Data masking is a security process that replaces or alters sensitive information with fictional or obfuscated values so the data can be used safely in non‑production environments without exposing real details.
Why is data masking used?
It protects personal, financial, or confidential data from unauthorized access, helps comply with privacy regulations, and allows realistic data use for development, testing, or analytics without risking exposures.
What are common data masking techniques?
Techniques include substitution (replace with fake values), shuffling (reorder data within a dataset), deterministic masking (consistent substitutions), dynamic masking (real‑time hiding), and tokenization (replace values with tokens).