If you are a fan of using virtual space or are more curious than usual on the Internet, you must have come across the proxy name. What is a proxy, and what is its use? This is the first question that comes to mind. In the following, we intend to answer these questions.
What is a proxy?
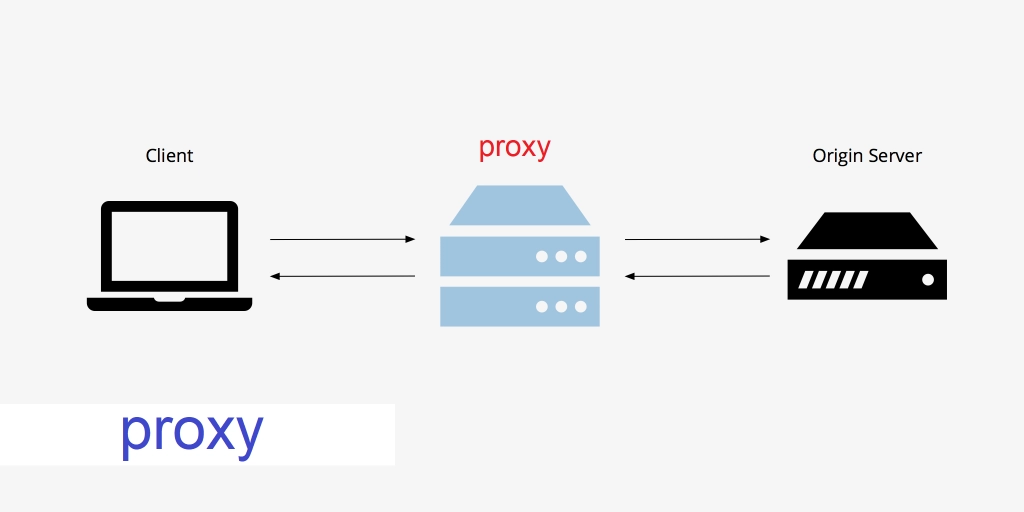
Proxy in English means attorney or representative. But in general, it is a bridge between the Internet, the Web, and the user. By connecting to the proxy, it acts as your representative on the web page, and you connect to different web networks through the proxy. A broker allows the host to control and monitor outgoing traffic or incoming content.
What is a proxy server?
A proxy server is a bridge or gateway between you and the web page. It can protect the information of users who visit the web page or users who visit multiple web pages from attackers. Therefore, a proxy server is one of the best facilities for preventing attackers from entering a network. Each proxy server has its own IP and establishes a connection between the user and the Web with that IP.
What is the use of a proxy?
Users usually use a proxy to enter filtered applications or websites, which is possible due to brokers’ ability to change the IP address. Changing the IP is one of the uses of brokers, but the primary use of brokers is to identify the user’s IP when entering the Web or application, and to control and monitor their IP. Such a feature prevents the entry and exit of dangerous data into the Web.
What are the types of proxies?
There are many types of proxies, and according to different things, such as the method of use, application, etc., they are placed in various categories. Follow the article to learn more about proxy types.
Types of proxies according to the method of use
According to the method of use, proxies are divided into two general categories: hardware and software. We will explain them in the following.
Hardware or physical proxy
This type of proxy is connected with the help of a physical server or router, which is mainly used in large businesses and companies, and has the role of a security layer.
Software proxy
Software proxies, which you are probably familiar with, are more readily available to users. They are open in applications that allow access to specific IPs. Software proxies are sometimes open to the public for free and sometimes require a subscription fee. But big companies and sensitive businesses usually don’t use free proxy types! As explained earlier, the host can access the proxy’s input and output data, which does not provide sufficient security.
Types of proxy in terms of application
According to their applications, there are different types of proxies, generally divided into twelve groups: transparent proxy, anonymous proxy, anonymous solid proxy, etc. We have explained each of them separately below.
Transparent Proxy
This type of proxy does not create a security shield for you! Also, a transparent proxy uses your real IP and does not change it. A transparent proxy is mainly used in centers where security is unimportant, and other proxy applications are intended only for schools, offices, and some small companies.
Anonymous Proxy
The most important use of an anonymous proxy is to hide your original IP from the websites you use! Websites get fake IPs from these proxies. Of course, when you use a broker, it becomes clear to websites that you are using a broker, and some sites do not allow access to users connected to the broker!
High Anonymity Proxy
These types of proxies are more powerful examples of anonymous proxies. The main difference of this proxy is that, in addition to changing your IP, web pages will not notice that you are using a broker and will recognize the fake IP as your real IP. But this is due to frequent updates and changes that the provider’s server applies to the broker so as not to leave a trace! Of course, you should note that nothing is definitive in this area, so your IP will usually not be detected when using a reliable anonymous proxy.
forward proxy
This type of proxy sends received information to groups within the network. It sends the user’s request to the host and makes the network work easier. Therefore, the forward proxy provides good security for networks with a single entry.
Distorting Proxy
This proxy type enters the web pages by distorting the user’s IP and providing a fake IP. Users who intend to hide some of their information from the Web use a distorting proxy. However, the critical point is that some websites have brokers that can detect them.
Data Center Proxy
This proxy is provided to the user through a data center and by a company; they are not dependent on Internet providers. Among the advantages of a data center proxy are the high speed of data collection and low price. You should note that, as mentioned earlier, you should not expect high security and IP anonymity from cheap servers.
Residential Proxy
As the name of this proxy suggests, they use the IP of physical servers to provide better security, but you have to pay more for it. Also, residential brokers are more suitable for cookie sites, blocking suspicious ads and advertisements.
Public Proxy
These types of proxies serve many people and are free. The public representative can also change the IP, but don’t expect high speed and security!
Shared Proxy
These proxies serve several users, which makes them cheap. However, as is known, a cheap server with several users will not be of high quality!
SSL Proxy
SSL proxy stands for Secure Sockets Layer. It is used when the user and the server use encrypted data. This proxy is also helpful for organizations that need high security against threats. The SSL protocol detects and stops threats and helps websites with SEO.
Rotating Proxy
This proxy type assigns a unique IP address to the user every time they connect. It does not reveal user information when multiple users use the same website, but some public or shared types are less secure.
Reverse Proxy
Unlike the forward proxy, this proxy is placed in front of the server and sends requests to it. Back brokers are helpful for popular and highly visited sites and keep their bandwidth low. However, they also have disadvantages. When hackers hack servers that use a back broker, their entire system is at significant risk and needs to be secured by other methods.
What are the types of proxy protocols?
There are different types of proxy protocols, as follows:
- SSL proxy
- HTTP Proxy
- FTP Proxy
- SMTP Proxy
- Socks proxy
How do proxies work?
When you use a web page, you request the website, and after entering, your request is accepted. But when using a proxy, which we said first, it means a lawyer or an agent, because each broker has its own IP. You send your request to the broker, and it requests the web page and receives a response, and then the answer is delivered to you. This process is done in most brokers with your proxy IP.
What are the benefits of proxies?
Proxies have many advantages, and you are probably familiar with one of them: IP change. But stay with us to learn about other proxy benefits.
high security
An example of this application is a firewall that filters dangerous data and prevents it from entering. Because of this advantage, proxies are widely used in organizations and large companies, and these companies often use stronger and certainly more expensive brokers. Also, with the help of brokers, you can put specific commands and rules on the server or prevent your digital address from being published.
Using a browser
One of the uses of a proxy in the browser is that with its help, you can prevent the entry of unwanted advertisements. The representative here works like an optimizer; you only enter the websites you need through it.
Log in to certain websites
Today, many websites make their pages available for a specific IP address of a particular country or group. Still, you can access certain pages with the help of a proxy and the ability to change the IP.
Limitation
When large companies intend to prevent their employees from entering specific sites or only allow them to access certain pages, the ability to personalize proxies quickly becomes crucial.
Increase access speed
Sometimes, we encounter low speed and limited access when entering some applications or websites. You must use a proxy to increase speed and access. By changing the IP and bandwidth, the broker facilitates access to the application or website!
Performance record
One of the capabilities of proxies is the accurate recording of user information and activity. Companies can store user requests, data, and communication with the help of brokers. This feature is used to check the performance of company employees and identify and prevent attackers from entering.
What are the disadvantages of a proxy?
In addition to all the advantages proxies have, they also have disadvantages. We will examine these disadvantages in the following section.
Reduced security!
One of them is less secure! Perhaps you will be surprised to see the contradictory statement about safety in the advantages section and the disadvantages of proxies! However, as powerful and more expensive brokers ensure high security, public and accessible representatives can compromise user security. A proxy also changes IP but lacks encryption. Brokers often use the SSL protocol, which is not secure enough. Also, proxies can remember passwords, and to ensure security in this case, you should get a representative from a trusted provider.
Difficulty entering local networks!
It is possible to access some websites by changing the IP through a proxy, but it should be noted that you may face problems when entering local networks! To use the local network, you need to configure or provide a proxy configuration according to the network.
What points should we pay attention to when choosing a proxy?
So far, you have learned about proxies, how they work, and the advantages and disadvantages of brokers. Below are some tips for choosing a broker that you should pay attention to!
Pay attention to the conditions and type of proxy!
We discussed different types of proxies, each with different levels of protection and particular uses. Therefore, you should pay attention to these things when choosing a broker! For example, a transparent proxy displays your original IP, and if you need to change your IP, it is better to use other types, such as an anonymous proxy.
No matter how much money you pay, you eat!
This adage also applies to proxies. Public and free brokers often have lower security and speed, and high-end brokers have higher support, speed, and security. So choose a broker that fits your conditions! Big companies cannot work with a free broker and need a strong and even physical broker!
Be familiar with the rules of the server provider!
Any proxy to change your IP will have access to your original IP, and each proxy provider has its own rules. If privacy and security are essential to you, you should pay attention to the level of encryption and its standards!
Conclusion
In this article, we read that a proxy is like a bridge between the user and the provider and can allow the user to access some sites and applications by changing the user’s IP address. Also, the proxy can create a limit for the company’s employees and monitor their activities. Also, in the article, we learned about the types of brokers and their advantages and disadvantages. There are some tips for choosing a broker that you must pay attention to. We hope the article was helpful to you. Please help us provide better services with your comments.
FAQ
What is a network proxy?
A network proxy is an intermediary server that forwards requests between a user’s device and the internet.
Why are proxies used?
They are used to improve privacy, cache content, filter traffic, and control access.
Are all proxies secure?
Not all proxies provide strong security; some offer basic filtering while others include encryption and advanced privacy features.