One Of The Important Tasks Of Security Professionals Is To Assess The Security Of The Organization.
This assessment includes technical aspects such as the configuration status of servers, firewalls, software, physical security controls, and informing employees about social engineering attacks.
The security assessment is one of the essential tasks of cyber security experts that should be done regularly.
Therefore, knowing how to perform these assessments is essential, as cybersecurity is not limited to firewall configuration and licensing.
Understanding how to assess the security of different parts of an organization and its associated risks will help you better protect your organizational infrastructure against cybercriminals.
What is an information audit?
Information Audit means analyzing and evaluating security mechanisms, databases, and resources that hold sensitive information. It is done to detect and improve communication accuracy, security, and up-to-dateness and resolve security issues.
In general, the information table is done for the following reasons:
- It is Observance of the organization’s information and security rules and policies.
- It is Awareness to ensure better security of information resources.
- Information needs of the organization.
- Identify costs related to information resources.
- Identify opportunities to use information resources to achieve strategic competitive advantage.
- It is the Development of security and intelligence policies.
- We are integrating IT investment with strategic business measures.
- Identify information flows and processes.
- Monitor and evaluate compliance and compliance with standards.
- Identify the organization’s information resources.
What is a security assessment?
Security assessments help you identify threats and prevent cyber attacks. Security assessment refers to a set of periodic measures that examine the security status of the enterprise network. Security assessments include identifying IT systems and business processes vulnerabilities and recommendations for reducing security risks.
Types of assessments
Security assessments include risk assessments, threats, configurations, vulnerabilities, and intrusion testing. Each of these assessments shows different problems with organizational infrastructure.
Risk Assessment:
- Risk assessment is the most common type of assessment in cyber security, which helps to ensure the continuity of business activities by identifying issues that may disrupt business activities. Some sources also describe risk assessment as risk analysis because it identifies risks around in-house assets and finds solutions to minimize them. In general, risk assessment is based on the following steps:
Identify assets:
- The first step in risk assessment is to identify the organization’s assets. Assets are anything valuable to the organization. For example, if a company has an e-commerce site that generates hundreds of thousands of dollars a day, it is an important asset.
Identify threats:
- Once you have identified the assets, you need to identify each purchase’s threats. In general, assets face various threats. For example, a website may encounter a denial of service (DoS) attack, or a hard drive on a web server may fail for various reasons, such as malware attacks. All you have to do at this point is list the threats.
Analyze impact:
- This step is done to determine each threat’s impact on the asset. For example, the effect of a Distributed Denial of Service (DDoS) attack on a corporate e-commerce site is to lose revenue when the recovery process is complete, and everything is back to normal. That’s why it’s essential to look at the impact of the threat carefully.
Prioritize threats:
- Once you have identified asset threats, prioritize each threat based on its impact on business activities and the likelihood of a hazard occurring. At this point, you should have a complete picture of the dangers.
Mitigate the threat:
- Once you have prioritized the threats, you need to determine what strategy you are looking to use to reduce them. For example, you can place the web server behind a firewall to prevent the successful execution of attacks around the web server or use the RAID solution to deal with sudden disk and drive crashes and data loss.
Threat Assessment:
- Threat assessment is part of the risk assessment process that identifies the various threats to an asset. As mentioned, you face multiple threats to investment, so part of the risk assessment is dedicated to prioritizing threats.
Configuration Assessment:
- Cybersecurity experts evaluate the security configuration of systems or networks by assessing designs. The above approach involves preparing a checklist of best practices for implementing them. What important assets does an organization have that we need to think about adequately evaluating and configuring? These assets include the following:
Systems:
- When evaluating, ensure the latest patches are installed on the systems. Make sure no unnecessary software or services are running on the plans. All designs must be protected with strong passwords.
- All systems must have antivirus software whose database contains the latest virus definitions and signatures. This database should be updated automatically.
File server:
- When evaluating the file server security configuration, ensure that the file server authenticates the files before accessing the files on the server, that the permissions are correctly assigned to the folders, check that people can access the information, and make sure the minimum Points are observed.
Web server:
- Websites that interact with sensitive visitor information should use SSL / TLS protocols to encrypt the data, authentication should be performed correctly, and there should be no unnecessary files on the web server. The web server should have a reporting feature so that you can closely monitor the process of accessing the websites.
SMTP server:
- In addition to patching and securing systems, ensure that a firewall protects the SMTP server and that there is no direct access to the server. In addition, the SMTP server must be protected by security tools such as antivirus software to detect any emails that contain infected attachments or spam sent to the server. Large organizations operating in the financial and insurance fields are faced with a significant amount of worthless spam. Opening only one of these spammers paves the way for hackers to infiltrate the systems. Paying attention to this point plays a vital role in reducing phishing attacks.
Routers:
- Experts set passwords for accessing Console, Auxiliary, and Telnet on routers so that they can control who wants to access the configuration of routers. For security reasons, it is best to use Secure Shell (SSH) protocol instead of Telnet for remote router management. Ensure the router has an access control list (ACL) that controls what traffic is allowed through the router. For example, it is possible to configure the router to allow traffic from specific networks. In addition, you must put an Implicit Deny All rule at the bottom of an access control list. The law states that must deny any traffic to the router other than specified networks.
Firewalls:
- Firewalls must be configured to block any traffic other than traffic that is expressly permitted through the firewall. This configuration is an implicit rejection and declares that only defined traffic on the firewall is allowed to pass. Since firewalls are connected to the Internet, you need to ensure that all remote management features are disabled and that a robust authentication mechanism is used on the device.
Switches:
- Ensure the passwords are configured on the switches’ console, auxiliary, and Telnet ports so that you can control who has administrative access to the device. Also, make sure that new portals are disabled so that cybercriminals do not succeed in using these portals for hacking. Most large organizations use VLAN technology to secure, better manage users, and closely monitor bandwidth. For security reasons, it is best to place the users of each unit on a separate network and use the Segments mechanism to break a single network into smaller networks.
Employees:
- When conducting manual assessments, test staff knowledge of security issues and arrange several social engineering attack scenarios. For example, you might consider whether an employee gives their password to an anonymous person. You can also place USB drives on employees’ desks to see how many of them connect an unknown USB drive to their systems. Employees with strict security training know that an anonymous USB drive may contain a virus and should not connect such purposes to their systems.
Physical security:
- Another critical issue around evaluation is physical security. Are all doors and windows locked; Have the systems’ CMOS settings been changed to prevent booting via optical discs or USB drives? Are software or hardware mechanisms used to prevent USB drives from connecting to systems? Are systems with confidential information equipped with remote control or monitoring features or remote communication software such as Team Viewer?
Vulnerability Assessment:
- Vulnerability assessment refers to identifying areas where cyber-attacks are more likely to occur. Most vulnerability assessments are performed using standard tools such as Nessus, OpenVAS, or LANguard GFI.
- Figure 1 shows the user interface of the LANguard GFI tool, which is a network vulnerability scanner. This tool helps network experts identify the parts of a system most vulnerable to attacks.
Vulnerability assessment tools are used to analyze the configurations of a system and identify areas that need further investigation.
Among the main functions of these tools are the following:
- Assess the status of patches installed on systems and report whether there are patches not installed on systems.
- Identify user accounts created on a system without a password.
- Inform about accounts that have not been used for a long time.
- I am informing you about the existence of different types of management accounts.
- Identify vulnerabilities or vulnerabilities that need to be addressed.
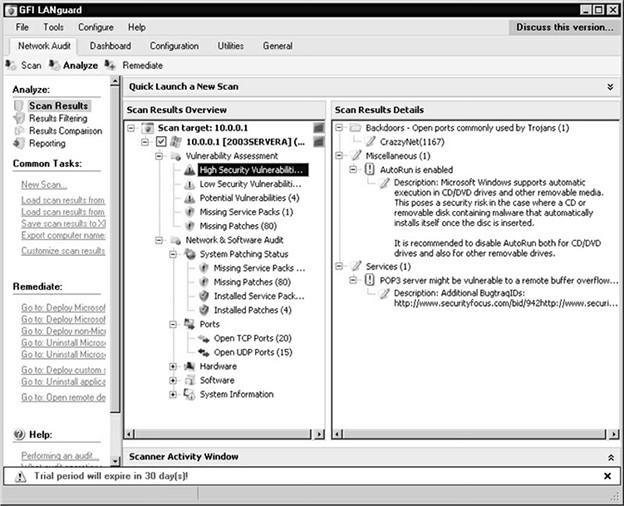
figure 1
The critical point to keep in mind when working with vulnerability assessment tools is that they only look at system configuration and offer recommendations for troubleshooting as much as possible but do little to reduce or repel cyberattacks. , Because their main task is to examine the structures of the systems. The following should be considered when assessing vulnerabilities.
Unused accounts:
- Are there any user accounts that have not been used for a long time? Generally, in all companies, employees leave the workplace while their accounts are still active. Therefore, it is essential to identify and deactivate new accounts. Any unused account may be subject to cyber-attacks because no employee can check their status.
Administrative accounts :
- must carefully monitor Management accounts. The smaller the number of management accounts, the better; the number of people who can change the environment is more limited.
Unpatched operating system:
- Unpatched operating systems pose a significant security risk to the defense doctrine, so watch out for systems that are not patched. If you have a vulnerable email server or database server, an attacker could launch a buffer overflow attack and gain full administrative access to the system. In addition, it is always possible that uninstalled vulnerabilities are installed on users’ systems.
Vulnerable software:
- One of the functionalities of vulnerability assessment software is its ability to identify vulnerabilities running on the system. For example, the evaluation software will notify you if a system is vulnerable to a Common Gateway Interface CGI attack.
Identifying vulnerabilities:
- The purpose of scanning is to identify vulnerabilities in the system. For example, if a system is not up to date with patches, it is known as a vulnerability in the network.
Identifying the lack of security controls:
- When performing a vulnerability assessment, look for security controls that should be used and are not currently in use. For example, when evaluating the security of a database server, make sure that a firewall does not protect it. In this case, you should inform the database administrator that the systems must communicate with the database server through the firewall to control everything.
Identifying common misconfigurations:
- When performing a vulnerability scan, check the system configuration to find any incorrect format that could cause security issues. For example, you may notice that the default management account name on a server has not changed.
last word
As you can see, one of the most critical tasks of security experts is to perform security assessments and audits. It is generally advisable to conduct inspections and audits at short intervals to ensure no unknown vulnerability on a system, especially web servers.