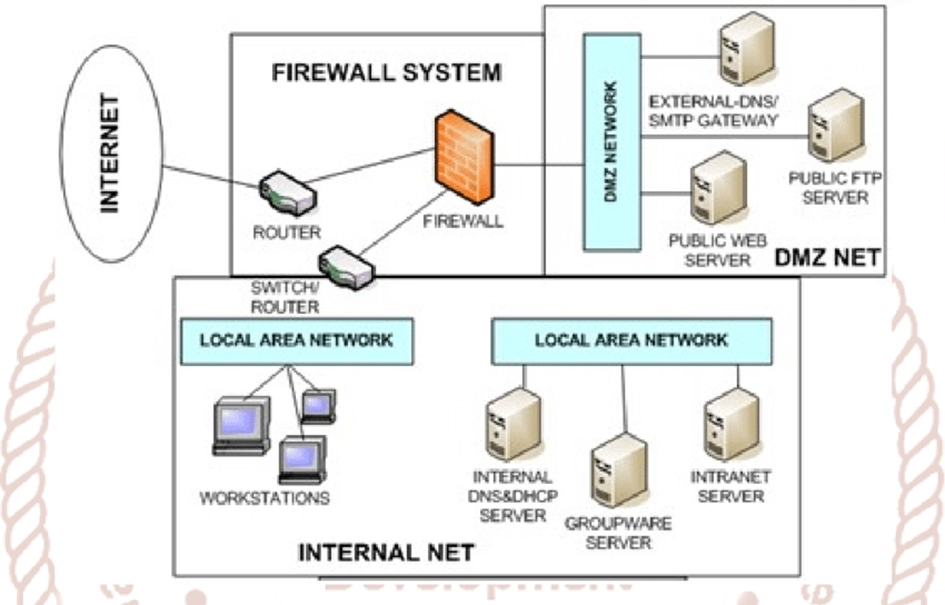
DMZ, which stands for Demilitarized Zone, indicates civilian networks in the network world. These networks, which are classified, play a big role in increasing the security of organizations. The DMZ network will maintain the security of the organization’s servers against untrusted services by creating a logical or physical layer. Of course, if you don’t know what a DMZ network is and what its uses or benefits are, stay with us until the end of the article.
In general, it can be said that DMZ is one of the main concepts in the network. For this reason, people in this field should be completely familiar with DMZ to create flawless networks. Also, this network has unique features that you should know.
How does the DMZ network work?
If we want to know, in general, what the DMZ network function is and its role in the network, we should pay attention to an important concept. Dmz networks are a zone or intermediary between private networks and the Internet world. For this reason, before the entry and exit of any data to the network, they check their security and original identity to prevent possible damages.
But it is interesting to know that DMZ is placed between two firewalls or the same security wall in some network designs. In such a situation, the malicious agent must reach the service or DMZ network after passing through the first firewall. This network also sends security alerts to network security experts to prevent attacks.
DMZ architecture review
To understand the function and concept of DMZ more easily, you should familiarize yourself with the architecture of this network. In general, there are two methods for implementing DMZ in networks, determined by the number of firewalls. Network experts can set up DMZ using one or two firewalls, But most new DMZ networks have two firewalls.
To know what DMZ architecture is and how it works, you don’t have to do much work; Because this architecture is extremely simple. In DMZ architecture with two firewalls, there are only three interfaces, the
function of each of which is as follows:
· First interface: connecting the internal network to the external network using the Internet service
· Second interface: internal network
Third interface: main network and DMZ network
One of the most important points in DMZ network architecture is port control over network traffic. For this reason, their configuration should be done in the best possible way. Also, the DMZ network has several automatic control systems that are useful for increasing network security.
What are the applications of the DMZ network?
Dmz Network has diverse and valuable applications due to its security capabilities. For this reason, various services are provided through the DMZ network, which is quite valuable. They also find unique features when they use DMZ network services. Of course, most of these features are related to security and only provide minor improvements in other parts of the network. In the rest of this section of the article, we will introduce more DMZ applications.
1. Providing web server services
You might also think that DMZ network applications are only related to organizations. But if you know what DMZ is and how it is implemented, you will see that this network is also used in public servers. For example, web services that provide various services have databases that contain sensitive data.
Sometimes these databases store personal or bank information and make it available to users. It is also obvious that such sensitive data is highly vulnerable to cyber-attacks. The DMZ network can increase security considerably by using its two internal firewalls.
2. Implementation of VoIP service
The VoIP (Voice over IP) service, which has recently become very popular, is one of the applications of the DMZ network. Dmz network can provide users with these services more safely due to security features. It is interesting to know that VoIP services are highly vulnerable to attack. For this reason, users’ calls may be intercepted. But when such services are combined with DMZ security, concerns about eavesdropping or other potential risks are reduced.3. Security protocols such as HTTP
If you want to know what DMZ is used for and its effect in the network world, look at the beginning of the site names at the beginning of your browser’s address bar. Dmz network can provide services and security protocols such as HTTP.
Of course, other protocols are readily available in a DMZ network and can surprisingly impact network security. For example, network experts can access FTP, Telnet, and SMTP protocols. Each of these protocols brings benefits individually.
4. Email services
Organizations always trust the emails that enter the servers, but organizations’ security suffers because of this misplaced trust. You should know that most cyber attacks are carried out with the help of emails infected with malware or viruses. When such malicious emails enter the organization, they can cause irreparable damage.
Sometimes, the emails that enter or leave the server through the Internet contain confidential information. For this reason, DMZ should be used to protect this data. Also, a proxy server must be installed in DMZ to comply with standard rules such as HIPAA. This proxy server will also be useful for controlling users connected to the Internet.
5. Authentication registration panels
DMZ networks with two firewalls are a good option for designing authentication panels or systems. In this so-called Back To Back architecture, two firewalls provide users with greater security. Of course, it has been seen that some network designers use the Three-Legged Model or single firewall architecture to design authentication systems. Of course, a DMZ network with two firewalls is a better option to control user authentication.
6. VPN services
Software and sites that provide VPN services usually have DMZ in their network. Of course, this is only done by platforms that value their users’ security; VPN services usually expose users’ personal information to hackers. DMZ also has many uses for VPN endpoints. With this trick, a service that is completely guaranteed in terms of security will be provided.
7. Application gateways
As smartphones became ubiquitous, application gateways, or their connection to servers, became more important. In these systems, the software is connected to the main server with a gateway and provides various information or services to the user. If you have understood what DMZ is and how it works by reading the article, using this network in application gateways is completely clear. When the DMZ is placed in the network, the security is increased, and the performance of the system users can be checked better.
What are the advantages of the DMZ network?
The DMZ network applications that were introduced in the previous section of the article all have many advantages. But you should know that there are some advantages inherent in DMZ that you should know. Network experts always try to use DMZ in their network design to access these benefits.
To achieve such valuable networking benefits, you must thoroughly understand important concepts such as DMZ.
1. Prevent malicious attacks to identify the network
One of the features of the DMZ network is buffering. For this reason, this network can identify malicious attacks and stop them. Also, when DMZ systems are damaged, the private network is still safe; Because the private network will be separated from the DMZ. Of course, the existence of this very secure network makes identifying the network a difficult task. Thanks to such features, the security of the internal or private network is significantly increased.
2. IP protection against spoofing
If you know a little about the methods of breaking into servers and networks, you know that one of the methods is IP address spoofing. Hackers try to bypass existing network access restrictions by spoofing the IP address. But my network prevents this by creating a security layer. This network waits for IP addresses that have been tampered with. If the network is fully working and the main IP addresses have access to the private network without any problems.
3. Controlling the valuable data of organizations
Organizations that store important data on their network and databases are at risk when communicating with external networks such as the Internet. Also, some users who have access to the network abuse this situation and publish information outside the network. For this reason, network professionals protect private networks of organizations using DMZ to have better control over user performance.
4. Forced to use a proxy to access the Internet
Users working with DMZ networks cannot connect to public networks like the Internet. Rather, to do this, they need a proxy connection to connect to external resources. Users need a proxy connection to access the system’s private network and internal resources. This proxy also acts as a relay and creates a secure connection.
5. Centralization of the website filtering process
In this section on what DMZ is, we will talk about one of the other widely used benefits in our country. Unfortunately, when filtering operations are performed on sites, even the useful parts of a site are disabled. The DMZ network can prevent this from happening with its unique control capabilities. Doing this allows only inappropriate content to be filtered, and useful parts remain available.
6. Simplifying the monitoring of user activity on the Internet
The user control has always been a big problem in organizations or large networks. But the DMZ network intends to simplify this work with its special features. As mentioned in the previous sections of the article, DMZ networks can control user activity. For this reason, DMZ should be implemented in organizations’ networks to achieve this worthwhile goal. Features such as Internet connection with proxy or security protocols will be valuable.
7. Less bandwidth required
In general, the DMZ network does not require much bandwidth and does not have much impact on network traffic. This important feature’s first big advantage to organizations or users is cost reduction. For example, it is no longer necessary to strengthen the infrastructure to upgrade the network. Also, the network speed will be higher than before despite the need for less bandwidth.
Examples of DMZ implementation in the real world
Now that you know what DMZ is and its beneficial uses and benefits, it is better to learn more about real examples of this network. With such examples, you can better understand the functioning of DMZ networks and understand how these networks perform in the real world. In this part of the article, we will introduce two real but valuable examples of DMZ networks.
Preventing penetration into the servers of operational technologies
All the applications introduced above are considered part of the IT world. But you should know that the DMZ network is not only limited to information technology. It also has many applications in operational technologies (OT-Operational Technology).
For example, in many power plants or large facilities, equipment such as turbines, control units, etc., are connected under a network. When these networks do not have enough security, hackers can completely take a power plant out of operation by penetrating the network. But with the presence of DMZ, security has increased, and such malicious attacks have become impossible.
Microsoft Azure cloud service
The cloud service of Microsoft Azura, which has a very high reputation, has taken help from DMZ in its network. In this cloud service, a security method in which DMZ plays a prominent role. This way, the DMZ network is placed between the organization’s internal and virtual networks. With this system, the software will also run inside the virtual and internal networks.
How to install DMZ on servers
If you want to know how to install DMZ and how this net is implemented in servers, stay with us in this part of the article. First, you should know that the implementation method completely depends on the type of DMZ network. For example, my implementation with one or two firewalls has minor differences. That’s why you should choose your DMZ architecture before starting the installation on the server. Of course, in the next sections of the article, we will introduce the details of the implementation of civilian networks.
Choose the right server.
In the first step, you must be careful that DMZ must be implemented on a different part of the net. That is, you should consider one server for the DMZ network and place other services on another server. Now you should prepare to install the civilian network on the LAN.
Create enough interfaces
As mentioned in the previous sections of the article, the Back To Back architecture of the DMZ network requires three interfaces. Since you know what are the necessary interfaces for dmz and what are its uses, you will no longer face a difficult challenge at this stage.
Use a firewall
Undoubtedly, firewall configuration is the most important thing to do when installing DMZ on a server. First of all, make sure that all important data and internal databases must be behind the firewall. We also recommend that you consider many firewall restrictions.
How to strengthen a DMZ network?
There are many ways network professionals can help you strengthen a DMZ network. For example, it is possible to use firewall security features or prevent IP spoofing. Also, service specialists should be run as Chroot and unnecessary instances should be removed from the network. It goes without saying that removing inactive users from the network increases security significantly.
In this article, we tried to tell what DMZ network is and how it works. If you are also interested in such topics and eager to learn more concepts, you will have access to a complete set of training in the field of network science.