According to the classical definition, any attempt to gain access to private and confidential information or to disrupt computer networks is called a cyber attack.
In simpler terms, any attack from one computer or network of computers to one or a network of other computers is a cyber attack.
Bob Thomas is said to have carried out the first cyberattack in 1971. An attack that is not very much on the scale of cyber attacks these days. He wrote a program that duplicated itself, and on the victim computer, the phrase “I’m THE CREEPER: CATCH ME IF YOU CAN” meant “I’m a crawler: if you can catch me.”
These few lines of code became known as Creeper.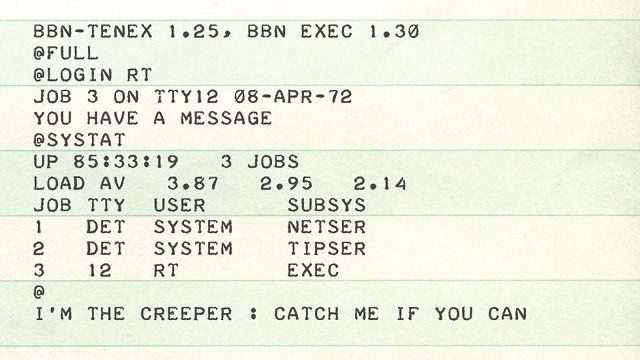
After the widespread release of this code on the ARPANET network, which can be called the current parent of the Internet, he created another program that could find and remove Creeper. It is said that this program was also one of the first anti-virus programs.
Given today’s cyber attacks, Creeper was just an annoying program that displayed a message, but these days we are faced with attacks that could lead to loss of life if not prepared to deal with them. Much broader, more complex, and more dangerous.
There are many different ways to carry out cyberattacks, but most cyberattacks can be classified into eight types:
Malware
The term Malware abbreviated MALicious softWARE means malware, which in Persian is called malware. Malware is a piece of code, like any other software developed by one or more programmers. The purpose of this malicious code is to disrupt, spy on, steal information, remotely control the victim’s computer, and in a word, damage a computer or network of computers.
The Mian Group reported on the use of malware to attack ethnic and religious minorities. “Iranian government hackers used malware to attack more than 100 people, including Turkish rights activists and Gonabadi dervishes,” the report said. ”
Phishing
Phishing Password Harvesting fISHING means trying to obtain a website password by creating a fake website or page, but it looks the same as the original site. The phrase Password Harvesting Fishing has also been translated into Persian as “Hunting a user password through a bait”. In Phishing, the letter Ph has been replaced by F to induce the concept of “cheating”. Just like a fisherman who deceives a fish with prey.
Iranian government hackers have a long and written history of using this method. Of course, they also use other methods, but phishing is one of the most widely used methods by government hackers in the Islamic Republic of Iran.
Ransomware
Ransomware is similar to malware in many ways, except that it was created for extortion. In this type of attack, the attacker usually encrypts the victim’s computer information in an unusable way and demands money from the victim to decrypt it. Simply put, they take computer information hostage and demand money for their release.
It was one of the most famous and destructive ransomware of modern Wannacry. In 2017, the malware-infected about 200,000 computers worldwide, including Iran, and demanded $ 300 worth of bitcoin (digital currency) from the victim to unlock the computers.
Fortunately, this very dangerous malware, which had infected many hospitals and medical centers and endangered the lives of many patients due to the non-functioning of medical equipment, was stopped by a 22-year-old hacker named Marcus Hutchins.
Refusal of service (Denial of service)
An Iranian proverb says “watermelons cannot be harvested with one hand” may be the best description for such an attack. This parable refers to the limitation of transport power. The same is true of computer data. Each site or online service can only respond to a limited number of requests.
When you enter www.bbcpersian.com in your browser, this computer network can only respond to a certain amount of requests to visit this site, although some techniques and methods can be used to manage requests.
Content is out. When this site or service is under a lot of pressure, like a person who works hard, he will lose consciousness and will no longer be able to respond to requests.
The purpose of such an attack is to make a website or service connected to a computer network inaccessible, mainly to disrupt the service.
Man in the middle (Man in the middle)
The middle man’s attack is actually a method of eavesdropping. Imagine that you are in contact with your friend through an intermediary who has succeeded in gaining your trust. This middle person manages to convince both of you that you have a private and direct relationship, but he listens to practically all of your conversations and may even change them in some cases. Such an action is called a middle-aged attack.
In August 2011, Google announced that it had succeeded in identifying and blocking an attack by Iranian government hackers using this method to attack political dissidents and human rights activists.
MySQL injection (SQL injection)
This is a direct attack on the database. Structured Query Language or SQL is a language for extracting data from databases. In this way, the attacker tries to infiltrate the database by finding security breaches. The purpose of stealing information includes a password or destroying information stored in a database.
Tapping the Zero (Zero-day exploits)
A zero-Day Attack is the exploitation of security holes in computer programs that have not yet been discovered by the manufacturer or, if discovered, have not yet been repaired. One of the most notorious of these attacks was the Stuxnet virus, which targeted Iran’s nuclear enrichment facility.
The makers of Stuxnet had found four security breaches in Windows that no one knew about, so they made plans to use these four breaches to disrupt or destroy Iran’s uranium enrichment process. Https://bbc.com/ ws / av-embeds / cps / Persian / science-54597932 / p067x5qy / en Video description,
Zero-day; The story of Stuxnet’s attack on Iran’s enrichment facilities
Cryptojacking
One way to generate money and digital currency are to use a computer. In this process, the user uses his computer resources such as power, processor, and memory to execute a series of instructions as a result of which he can generate digital currency.
To generate a lot of digital currency, you have to consume a lot of these resources, which is sometimes not economical.
For this reason, the attacker uses the Cryptojacking method without your knowledge and starts using your computer resources to generate the desired digital currency for himself. In fact, the attacker steals your resources.