MikroTik Firewall Introduction
Getting to know the Firewall in Mikrotik
Mikrotik firewall; MikroTik firewall is one of the most used parts of this router. Although this Firewall is not perfect, you can use it extensively to protect your router.
Like most routers, MikroTik is equipped with a firewall.
Since MikroTik does not have a stand-alone network firewall, like the major network equipment vendors, makes the Firewall inside the router a bit better equipped.
Although this Firewall cannot replace a UTM or hardware firewall, it can be used in projects where the cost is necessary.
If you have a large number of firewall roles or use a layer seven firewall extensively, be very careful in choosing the right router board so that the quality of your router’s service is not compromised.
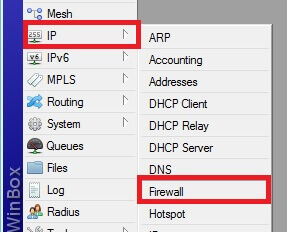
Select IP and then Firewall from the left menu to access it.
In the window that opens, go to the filter role tab:
Chain in the Mikrotik firewall
By default, the MikroTik Firewall has three chains.
- Input Chain: This packet is placed in the input chain when a packet’s destination is the router itself. When using MikroTik as a DNS server, DNS packets are in the inbound chain.
- Output chain: packets whose source address is the router itself. Like the NTP packet, the router sends to the Internet to set its clock.
- Forward chain: Packets that are intended to pass through the router. Like when the router only routes the packets and the source, and the destination addresses of the packets are not any of the router’s board addresses.
Adding a new roll to MikroTik is easy.
Click on the add sign and go to the General tab.
Then select the chain you want. Fill in the fields depending on the scenario.
Note that leaving any field blank means that the field is unimportant.
Then go to the Action tab and select the type of firewall action with the package that fits this role:
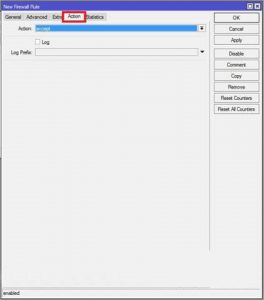
Three important actions of Mikrotik are as follows:
- Accept: This function allows the packet to pass.
- Drop: This operation discards the packet and does not send the result to the sender.
- Reject: This operation discards the packet and reports the result to the sender.
For better firewall performance, put these three roles in a high-priority firewall. Otherwise, some rolls may not work properly.
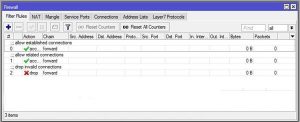
To apply these rules, copy the following commands into the Mikrotik terminal:
ip firewall filter
a) add chain=forward connection-state=established comment=”allow established connections
”b) add chain=forward connection-state=related comment=”allow related connections
c) add chain=forward connection-state=invalid action=drop comment=”drop invalid connections
Conclusion
In this article, we got acquainted with the Mikrotik firewall, its actions, and the firewall chain in Mikrotik. Good luck!











