Thinking About What Devices Are Connected To Your Home Network? You May Be Surprised At The Devices That Are Connected To Your Home Network Without Your Knowledge, But How Do We Identify These Devices?
This article will learn how to use the Nmap command in Linux to identify all devices connected to the network.
Some people think that the home network is a straightforward entity with no hidden secrets, and they do not need to increase their knowledge about these networks.
This view may have been accurate in the past. Still, with the proliferation of IoT devices, mobile devices such as smartphones and tablets, the smart home revolution alongside conventional devices such as broadband routers, laptops, and desktops, your eyes should be wide open.
Users with Windows 10 installed on their systems can easily detect this, but how do we see the above devices in Linux? The answer lies in a word called Nmap.
The first step is to install Nmap.
This article will use the Nmap name to identify devices connected to the network. Depending on the software package you have installed on your system, you may have to install Nmap.
If Nmap is not installed on the system, the following command allows you to install Nmap on an Ubuntu distribution.
sudo apt-get install Nmap
To install Nmap on a Fedora distribution, use the following command:
sudo dnf install Nmap
The above command installs the Nmap on Manjaro.
sudo Pacman -Syu map
You can install Nmap on other Linux distributions using the package management tool.
Find your IP address.
The first step is to find the IP address of your Linux computer. Here you will see a range of IP addresses that the network uses to manage devices. Here are the minimum and maximum IP addresses that your computer uses.
We need to specify IP addresses or a range of IP addresses for nmap here, so we need to find this value first. Linux has a handy command called IP, which has an addr. To use the above control, type IP, create a space with the spacebar key, type addr, and press Enter.
IP addr
You will see your IP address at the bottom of the above command. The above address is marked with an inlet tag.
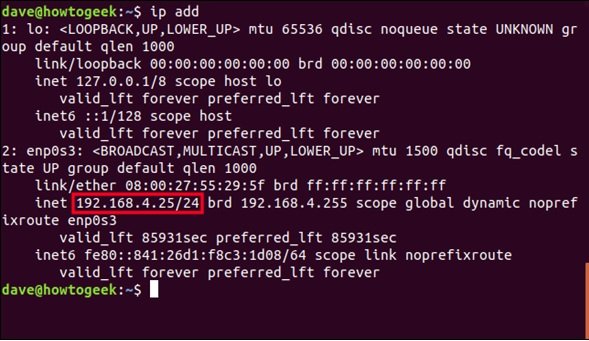
The IP address in the image above is 192.168.4.25. / 24 means three consecutive sets of eight 1s in the subnet mask. 3×8 = 24
In the binary system, the subnet mask is equal to the following value:
11111111.11111111.11111111. 00000000
In the decimal system, this value is equal to 255.255.255.0.
The subnet mask and IP address are used to indicate which part of the IP address is used to identify the network and which part is used to identify devices. This subnet mask informs the hardware that the first three numbers identify the IP address of the web, and the fourth part is the IP address used to identify unique devices.
Since the most significant value you can store is an 8-bit binary value of 255, the IP address for this network is in the range 192.168.4.0 to 192.168.4.255. All of these are listed in / 24. Fortunately, nmap works with this token, so we need to use nmap.
Start using nmap
Nmap is a network mapping tool. Nmap works by sending different network messages to IP addresses within the specified range. Let’s do a simple nmap scan. We intend to use the -sn option (scan without port). This option tells nmap that it does not currently need to check the status of ports on devices.
As a result, it will perform light and fast scans. Note that the larger the number of devices within a network, the more time-consuming it will be. The IP address that we intend to use is the address that we obtained from the execution of the previous command.
Here the parameter 192.168.4.0/24 for nmap is translated to the equivalent of the starting IP address equal to 192.168.4.0 and includes all IP addresses up to 192.168.4.255. Note that we use sudo as follows.
sudo nmap -sn 192.168.4.0/24
After a short wait, the output of the above command is written in the terminal window. You can run this scan without using sudo, but using sudo ensures that as much data as possible is extracted. For example, without sudo, this scan does not return manufacturer information.
The advantage of using the -sn option is the quick and easy scanning, which provides a clear list of current addresses. In other words, we have a list of devices connected to the network with their IP address, and, if possible, nmap also provides information about the device manufacturer. You can see the list provided with the manufacturers’ specifications in the image below.
We now have a list of connected devices, so we know how many connected devices are. There are 15 devices turned on and connected to the grid in the picture above. We also know the names of some device manufacturers. The specifications of some devices, such as Raspberry Pi, are likely to be recognizable, but for some devices, you need to do more.
Perform a deeper scan
If we remove the -sn option from the nmap command, nmap also checks device ports. Every application or service within a device has a port number. Network traffic is delivered to an IP address and a port, not just an IP address. Some port numbers are preset or reserved.
They are always used to transfer network traffic to do a specific job. For example, port 22 is reserved for SSH connections, and port 80 is reserved for HTTP web traffic. We will use nmap to scan each device’s port to see which open ones. For this purpose, we execute the following command.
nmap 192.168.4.0/24
This time we will get more details about each device. The output of the following command is as shown below.
Since the output of this command contains a lot of information, you can move the result into a text file. The following command does this.
nmap 192.168.4.0/24 > nmap-list.txt
The nmap command has other features, and I suggest you take some time and discover all of them.