In computing, a firewall is a Network Security System that monitors and controls incoming and outgoing Network traffic based on predetermined Security rules. A firewall typically establishes a barrier between a trusted and untrusted Network, such as the Internet.
History
The term firewall originally referred to a wall to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to Network technology, which emerged when the Internet was fairly new in terms of global use and connectivity.
The predecessors to firewalls for Network Security were routers used in the late 1980s. Because they are already segregated networks, routers could apply filters to packets that cross them.
What Is a Firewall: Types, How Does It Work, Advantages & Its Importance
What Is a Firewall?
Firewalls prevent unauthorized access to networks through software or firmware. They examine and block incoming and outgoing traffic using rules.
Fencing your property protects your house and keeps trespassers at bay; firewalls are used to secure a computer Network. Firewalls are Network Security systems that prevent unauthorized access to the web. It can be a hardware or software unit that filters the incoming and outgoing traffic within a private Network according to rules to spot and prevent cyberattacks.
Firewalls are vital components of network security in enterprise and personal settings. Most operating systems have a basic built-in firewall, but using a third-party firewall application provides better protection.
Now that we understand what a firewall is, we will examine its history from this point forward.
History of Firewall
Network firewalls have evolved over the years to address several threats in the Security landscape. Firewalls will remain crucial to organizations and society. So, let’s look at a brief history of firewalls.
- 1989 – Birth of packet filtering firewalls
- 1992 – First commercial firewall, DEC SEAL
- 1994 – The first stateful firewalls appear
- 2004 – IDC coins the term UTM (unified threat management)
- 2009 – Gartner introduced Next Generation Firewall (NGFW)
Why Are Firewalls Important?
Firewalls are designed with modern Security techniques used in a wide range of applications. In the early days of the Internet, networks needed to be built with new Security techniques, especially in the client-server model, a central architecture of modern computing. That’s where firewalls have started to create Security for networks with varying complexities.
Key Uses of Firewalls
- Firewalls can be used in corporate and Consumer settings.
- These firewalls can incorporate a security information and event management strategy (SIEM) into cybersecurity devices for modern organizations and are installed at the network perimeter to guard against external and insider threats.
- Firewalls can perform logging and audit functions by identifying patterns and improving rules by updating them to defend against immediate threats.
- Firewalls can be used for a home network, Digital Subscriber Line (DSL), or cable modem with static IP addresses. They can easily filter traffic and signal the user about intrusions.
- They are also used for antivirus applications.
- When vendors discover new threats or patches, the firewalls update the Rule sets to resolve the vendor issues.
- We can set restrictions for in-home devices using hardware/firmware firewalls.
Functions of Firewall
- A firewall’s most essential function is to create a border between an external network and the guarded network. The firewall inspects all packets (pieces of data for internet transfer) entering and leaving the conservatiNetworkork. Once the inspection is completed, a firewall can differentiate between benign and malicious packets with the help of a set of pre-configured rules.
- The firewall abides by such packets, whether in a Rule set or not, so they should not enter the guard network.
- This packet form information includes the information source, its destination, and the content. These might differ at every level of the network, as do the Rule sets. Firewalls read these packets and reformat them according to rules to tell the protocol where to send them.
How Does a Firewall Work?
As mentioned previously, firewalls filter network traffic within a private network. They analyze which traffic should be allowed or restricted based on rules. Think of the firewall as a gatekeeper at your computer’s entry point, allowing only trusted sources, or IP addresses, to enter your network.
A firewall welcomes only incoming traffic that has been configured to be accepted. It distinguishes between good and malicious traffic and allows or blocks specific data packets on pre-established Security rules.
These rules are based on several aspects of the packet data, such as their source, destination, content, etc. They block traffic coming from suspicious sources to prevent cyberattacks.
For example, the image below shows how a firewall allows good traffic to pass to the user’s private network.
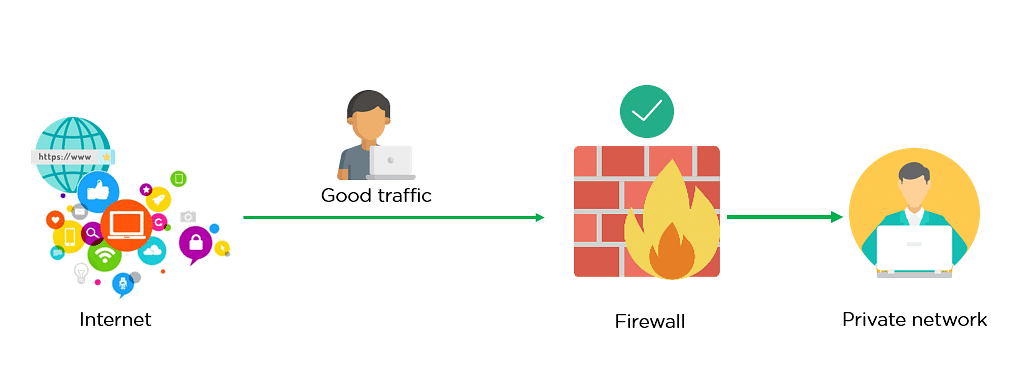
However, in the example below, the firewall blocks malicious traffic from entering the private network, protecting the user network from being susceptible to a cyberattack.
This way, a firewall performs quick assessments to detect malware and other suspicious activities.
Different types of firewalls can read data packets at different Network levels. Now, you will move on to the next section of this tutorial and understand the various types of firewalls.
A firewall can be software or hardware. Software firewalls are programs installed on each computer that regulate network traffic through applications and port numbers. Additionally, a firewall delivered by a cloud solution is called a cloud firewall.
There are multiple types of firewalls based on their traffic filtering methods, structure, and functionality. A few of the types of firewalls are:
- Packet Filtering
A packet-filtering firewall controls data flow to and from a Network. It allows or blocks data transfer based on the packet’s source address, destination address, application protocols used to transfer the data, and so on.
- Proxy Service Firewall
This firewall protects the network by filtering messages at the application layer. A proxy firewall is a gateway from one network to another for a specific application.
- Stateful Inspection
A firewall permits or blocks network traffic based on state, port, and protocol. It decides on filtering based on administrator-defined rules and context.
- Next-Generation Firewall
According to Gartner, Inc., the next-generation firewall is a deep-packet inspection firewall that adds application-level inspection, intrusion prevention, and information from outside the firewall to go beyond port/protocol inspection and blocking.
- Unified Threat Management (UTM) Firewall
A UTM device generally integrates the capabilities of a stateful inspection firewall, intrusion prevention, and antivirus in a loosely linked manner. It may include additional services and, in many cases, cloud management. UTMs are designed to be simple and easy to use.
- Threat-Focused NGFW
These firewalls provide advanced threat detection and mitigation. By combining network and endpoint events, they may detect evasive or suspicious behavior.
Advantages of Using Firewalls
Now that you have understood the types of firewalls, let us look at the advantages of using them.
- Firewalls are essential in companies’ security management. Below are some of the crucial advantages of using firewalls.
- It provides enhanced Security and privacy for vulnerable services. It prevents unauthorized users from accessing a private Network connected to the Internet.
- Firewalls provide faster response times and can handle more traffic loads.
- A firewall allows you to easily handle and update the Security protocols from a single authorized device.
- It safeguards your network from phishing attacks.
How to Use Firewall Protection?
Ensure your firewall is set up and maintained correctly to keep your network and devices safe. Here are some tips to help you improve your firewall Security:
- Constantly update your firewalls as soon as possible: Firmware patches update your firewall against any newly discovered vulnerabilities.
- Use antivirus protection: In addition to firewalls, you must use antivirus software to protect your system from viruses and other infections.
- Limit accessible ports and hosts: Limit inbound and outbound connections to a strict allowlist of trusted IP addresses.
- Have an active Network: To avoid downtime, have functional Network redundancies. Data backups for Network hosts and other critical systems can help you avoid data loss and lost productivity in the case of a disaster.
Application Layer and Proxy Firewalls
Proxy firewalls can protect the application layer by filtering and examining a packet’s payload to distinguish valid requests from malicious code disguised as reasonable requests for data. Proxy firewalls prevent attacks against web servers from becoming more common at the application layer. Besides, proxy firewalls give Security engineers more control over Network traffic with a granular approach.
On the other hand, application-layer filtering by proxy firewalls enables us to block malware and recognize misuse of various protocols, such as the Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), specific applications, and Domain Name System (DNS).
The Importance of NAT and VPN
NAT and VPN are both essential Network translation functions in firewalls.
- Nat (Network Address Translation)
- It hides or translates internal client or server IP addresses that are usually in a “private address range.” RFC 1918 defines it as a public IP address.
- NAT preserves the limited number of IPv4 addresses and defends against Network reconnaissance as the IP address from the Internet is hidden.
- VPN (Virtual Private Network)
- A VPN extends a private Network across a public Network inside a tunnel that can often be encrypted. However, the contents inside the packets are protected, especially when traversing the Internet.
- A VPN lets users send and receive data across shared or public networks.
Next-Generation Firewalls (NGFW)
These are used to inspect packets at the application level of the TCP/IP stack, enabling them to detect applications such as Skype or Facebook and apply application-specific Security policies. Next-generation firewalls include sandboxing technologies and threat prevention technologies such as intrusion prevention systems (IPS) or antivirus software to detect and prevent malware and threats in files.
Vulnerabilities
- Insider Attacks
Insider attacks involve transmitting sensitive data in plain text, resource access outside of business hours, liable resource access failure by the user, third-party users’ Network resource access, etc.
- Distributed Denial of Service (DDoS) Attacks
A distributed denial of service (DDoS) attack is a malicious attempt to disrupt the regular traffic of a targeted Network by overwhelming the target or its surrounding infrastructure with a flood of traffic. The DDoS attack mitigates the difference between an attack and regular traffic. Nevertheless, the traffic in this attack type can come from seemingly legitimate sources that require cross-checking and auditing from several Security components.
- Malware
Malware threats are usually tricky due to their varied, complex, and constantly evolving nature. With the rise of IoT, networks are becoming more complex and dynamic, so sometimes it becomes difficult for firewalls to defend against malware.
- Patching/Configuration
Patching/Configuration is a firewall with a poor configuration or a missed update from the vendor that may damage Network Security. Thus, IT admins need to be very proactive in maintaining Security components.
The Future of Network Security
In the last few years, virtualization and trends in converged infrastructure created more east-west traffic, and the most significant volume of traffic in a data center is moving from server to server. With this change, some enterprise organizations have migrated from the traditional three-layer data center architectures to leaf-spine architectures. This change in architecture made some Security experts warn that firewalls have an essential role in keeping the network secure in a risk-free environment. Thus, the importance and future of firewalls have no end. However, there may be many advanced alternatives to firewalls in the future.
Difference Between a Firewall and Antivirus
Firewall
- A firewall is an essential software or firmware in Network Security that prevents unauthorized access to a Network.
- It is used to inspect incoming and outgoing traffic with the help of a set of rules to identify and block threats by implementing it in software or hardware form.
- Firewalls can be used in both personal and enterprise settings, and many devices, including Mac, Windows, and Linux computers, come with one built in.
Antivirus
- Antivirus is also an essential component of Network Security. It is an application or software used to protect against malicious software on the Internet.
- An antivirus works based on three primary actions: Detection, Identification, and Removal of threats.
- Antivirus can deal with external and internal threats by implementing only software.
Limitations of a Firewall
- Firewalls cannot stop users from accessing data or information from malicious websites, making them vulnerable to internal threats or attacks.
- It does not prevent password misuse or attackers with modems from dialing in to or out of the internetwork.
- Already infected systems are not secured by Firewalls.
FAQ
What is a firewall and how does it work?
A firewall monitors incoming and outgoing network traffic and allows or blocks data based on security rules, protecting your network from unauthorized access.
What types of firewalls exist?
Hardware Firewall: A physical device placed between networks to manage all traffic. Software Firewall: A program installed on a device to protect that individual system.
What are the main benefits of using a firewall?
Firewalls enhance network security, block unauthorized access, monitor traffic, and enforce security policies, ensuring data protection and network reliability.