Software-Based Networks Are Not A New Technology And Are More Than Ten Years Old, But In Recent Years Have Been Considered By Many Companies, Especially Iranian Companies.
Most organizations seek to make the most of the significant benefits of this technology, which are cost reduction, increased productivity, and tighter network monitoring.
Given that in recent times, the cost of purchasing network hardware equipment and the salaries of specialized personnel have increased significantly, companies are trying to use software-based networks to reduce costs.
However, before you think about designing or using these networks, you need to know enough about these networks.
What is a network environment?
One of the most important things to consider when designing a computer network is how to secure private corporate networks with unreliable networks such as the Internet.
As long as the private network is not connected to external networks, it will face the lowest rate of cyber-attacks; Because everything is under control, it is possible to identify problems quickly or if an employee connects contaminated flash memory to a system due to negligence and disregard for security policies, causing network contamination.
Yes, this issue can identify quickly. However, when this secure network is connected to a network like the Internet, it faces various challenges. To evaluate the performance of software-based networks properly, we must first look at how computer networks work and what hidden components and components they are made of because software-based networks provide all of these capabilities in software.
Network Perimeter is the boundary between a private corporate LAN and public networks like the Internet. In general, the network environment is the same as in Figure 1.
The environment includes firewalls, intrusion detection and prevention systems (IDPSes), program-aware software, sandboxes to prevent malware from entering the network, and other security requirements. Almost all large enterprise networks are implemented based on this architecture.
figure 1
As Figure 1 shows, three areas in the network environment serve as the boundary between the private enterprise network and the Internet:
- Internal Zone: It’s An area defined for organizing users and servers. This area is also known as the safe or trusted area because it has the highest degree of security. No external access to the internal area is allowed; all access should be through the Civilian Area (DMZ) if necessary.
- Civilian Zone (DMZ): An area that users can access via the Internet-based on specified restrictions. Simply put, any connection of external clients and networks to the private enterprise network is made through equipment in this area. For example, emails received from external servers enter the internal server in SZ.
- External Zone: The point of contact between the internal and external networks through communication links. For example, links received from Internet Service Providers (ISPs) are routed to this point and typically to Denmark. In organizational design, depending on the size or smallness of the organization, a room with special equipment is considered to which the communication links of Internet service providers are entered, and the required bandwidth is provided to different parts of the organization. The above approach has many advantages. The first is that it simplifies the process of troubleshooting network problems, and the second is that if a malware attack occurs, it is possible to cut off internal and external networks in the simplest way to prevent information theft or hackers from infiltrating networks further.
It is usually not easy to implement such technologies, as you may have to implement multiple DMZs for different applications on a large scale.
Also, in this architecture, firewalls are distributed in clusters, and each firewall is located in a different place (usually two firewalls in each location).
In the Zero-Trust architecture proposed by Forrester Research, when designing secure networks, we need to consider what level of security we need to protect critical network data, assets, applications, and services (DAAS) and How to design firewall topology and defense mechanisms.
In this architecture, we need to identify the trusted area for users and servers, the untrusted area for external connections such as the Internet, and public areas that include devices and services accessed through external networks.
Typically, network experts deploy additional, mostly security, software within the network environment, including intrusion detection and prevention systems, sandboxes that run suspicious software downloaded from the Internet, web and email filters, and so on.
These security tools can implement in two forms of hardware or software in the network environment to detect common attacks on the network environment . a vital point to note is that attacks on different network layers may focus on the network itself or network components.
Pages Data, Control, and Management
One thing to know about network devices is that they perform three different operations:
- Processing and sending data to the Data Plane.
- Making decisions regarding sending data packets; That is, where the information is to be sent (Control Plane).
- Activation of management mechanism for reading information from devices (Management Plan).
How these three pages work is shown in Figure 2.
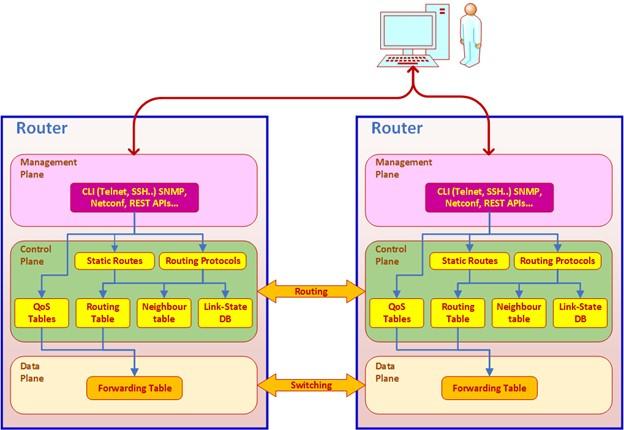
figure 2
Data Plane
The data page is responsible for sending information. It receives instructions and knowledge needed to send packets, such as routing tables and packages sent from port to port, from the control panel. An important point to note about the submitted tables is their self-learning feature, which can record important information sent by the control panel and use it in subsequent posts to reduce network slag. For example, it is possible to run multiple routing protocols on the control panel but enter them into a single routing table based on the consensus attribute and access the data page. In addition, the data-sheet is responsible for processing and delivering packets, so it is implemented on network interfaces and device processors.
Control Plane
A control panel is a place that specifies how data is sent on the data plate. The control panel contains routing protocols that exchange information between routers, hosts multicast protocols, service quality protocols (QoS), and any other protocols that network devices use to exchange information and decide whether to send data. These protocols are executed on the control page, and a table is sent to the data page. The control panel is one of the critical components of software-based networks that requires a powerful CPU to perform calculations. This page is also facing various attacks. Some try to consume device resources (such as CPU and memory), while others try to poison protocols running on the device to send fake routes or direct traffic to the hackers’ targets. Be.
Management Plane
Hackers mainly carry out attacks at the management level to infiltrate network equipment, change settings, and circumvent organizational policies to disrupt or enter the network. The admin page is responsible for interacting with network devices. This interaction may be through protocols such as SNMP, Netflow, REST application programming interfaces, or any other method defined for networked devices. Of course, it is possible to manually manage via command line, proprietary client software, or web-based interface. The software fully implements the admin page.
SDN and NFV
SDN and NFV are technologies that emerged in the early 2010s to virtualize network operations. While SDN is a technology developed to help design enterprise networks and software-centric data centers easier, NFV, on the other hand, is a Network Service Provider (NSP) based Network Service Provider.
Software-centric networks (SDNs)
SDN is a software-centric network and network management approach that centrally manages our devices. The technology uses an application programming interface to plan the network through centralized control intelligently. The above procedure allows easy monitoring and simple troubleshooting of network equipment so that it tries to control the network intelligently by removing the control panel from network devices. Major hardware such as network devices and related technologies still exist here, but we can centrally program and manage them. As a result, we can collect and troubleshoot your entire network continuously and efficiently with more flexibility and speed.
Software-centric networking is important because it gives network operators a new way to design, build, and deploy enterprise-wide area networks (WANs).
- Ability to plan traffic.
- Increase capacity following organizational policies.
- Close monitoring of the network.
- Ability to implement network automation.
- Restore the network in the shortest time due to breakdown or other problems.
By separating the data page from the control panel, SDN creates an efficient software-based programmable network infrastructure that can be manually, automatically managed, and tailored to the organization’s business needs. While in traditional networks, networked devices, such as switches, exchange information with each other and use common topologies to send packets, in software-centric networks, switches are simple devices that send instructions according to the education they receive from the network controller.
In a traditional network, the following components are present:
- Control Panel: On this page, Its routing protocols exchange routing information to examine restrictions such as access control lists (ACLs) and QoS requirements and populate routing tables.
- Data page: Use routing tables to send data. When a packet enters the router, it is sent according to the table information.
Figure 3
Figure 3 shows an example of an SDN network. In this network, we have a central controller, the network’s core. This controller acts as a control panel for the entire network. When a new session opens and packets are sent over the web, each switch receives the first packet, sends a request to the controller, and asks how to send the box. After receiving the answer, the buttons store the information in their table. From now on, each package will be shipped based on the information in the table. It is done through the Southbound interface using protocols such as OpenFlow or Netconf. Also, communications from the controller to the switches are established via TCP and secure transfer protocols (TLS).
In the northern interface, the controller sends and receives information to SDN programs through standard programming interfaces such as RESTfull.
SDN applications can be applications that implement network functions such as routers, firewalls, load balancers, or any other network functionality. An example of an SDN application is the Software-Wide Area Network (SD-WAN), which provides a connection between remote sites via private lines and the Internet.
The SDN domain includes all devices running under the same SDN controller. There is a network regulator (Orchestrator) to control multiple SDN domains. For example, when corporate LANs are connected via a private SD-WAN service, there are three controllers for two LANs and one for SD-WAN. In all of these processes, the regulator is responsible for controlling connections and communications. Network experts need to address significant security issues when designing an SDN network. These include the following:
- Attack connections between controller and SDN switch via a standard TCP connection with a standard port number.
- Attack network controllers and regulators.
- Attack data page switches.
Network Performance Virtualization (NFV)
NFV first introduced the concept of computational virtualization to the world of networks. The above image implies that instead of using proprietary hardware for each network function, we use hardware that interacts with standard virtual machines. In this case, network operations are executed as software on virtual machines. To achieve this goal, we need platforms that host these programs. Figure 4 shows these platforms.
Figure 4
Figure 4 shows how to deploy network applications. In the case of Linux containers, virtual machines are implemented as Linux containers, and programs are installed on them.
A virtual machine simulator is a computer system that provides the performance of a physical computer.
A hypervisor is a software that runs virtual machines. There are generally two types of hypervisors, Type 1, which runs directly on the system hardware, and Type 2, which runs on the host operating system.
Hypervisor type 1 is installed directly on the hardware. Common hypervisors in this group include VMWare ESX / ESXi, Microsoft Hyper-V, and Citrix XenServer. The first hypervisor was developed by IBM in the 1960s, followed by the iVMWare ESX (later ESXi) in 1999, the XEN from Citrix in 2003, and a year later, the Hyper-V from Microsoft. In the Linux world, this process began with traditional Unix platforms such as Sun-Solaris, followed by KVM and Dockers.
Linux containers quickly captured the market for NFV technology thanks to the many applications they provided, as they were able to give routers, switches, firewalls, security devices, and other applications needed in a data center network.
Hypervisor type 2 is installed on the host operating system. Famous hypervisors in this group include VMWare, Microsoft Virtual PC, and Oracle Virtual Box.
Figure 5
Figure 5 shows the NFV model architecture. The NFV architecture consists of the following components:
- Computing Hardware: Refers to computing resources and storage.
- Authorized Resources: Resources allocated to virtual machines.
- VNFs: The Virtual machines and applications installed on them, such as routers, firewalls, Core Cellular Components, and other network functions.
- Element Managers (EMs): Manage network performance.
- Management and Regulators NFV (MANO): Together with Operation Support Systems (OSS) and Business Support Systems (BSS), control the amount of resource consumption.
One of the most critical attack vectors around NFV technology is attacking the entire software stack, including operating systems, hypervisors, virtual machines, and applications.
last word
As you can see, the implementation of software-based networks is based on understanding standard network equipment’s performance. By abstracting the hardware components, software-centric networks try to provide a centralized management mechanism to network administrators that simplify monitoring traffic and user performance and the network expansion process as quickly as possible.