Network scanning is the first phase of penetration testing. The information obtained in this phase is very important and useful in penetration testing. In this phase, information such as an address, type of operating system, installed services, and applications is obtained. In this article, we tried to test the Mikrotik router as a target and then check the necessary measures to prevent these attacks, which you can benefit from if you are familiar with Mikrotik.
- Types of scanning
- Definition of flag
- Types of TCP flags
- Status of ports
- Common scans on the NMAP network
- Find the target operating system
- Working with Nmap and analyzing its output
- Mikrotik scan with Nmap
- Vulnerability scan
- Working with Nessus
- analyze
- Use of proxies
Types of scanning
Port scanning: identifying open and available TCP/IP ports. Every port has an active service, which can get valuable information if a hacker scans the ports. For example, the opening of port 21 means that FTP is active. You can see the list of its ports and services in this link.
Network scan: This scan is done to identify live targets (available systems) in the network, and the main requirement for this is usually pinging. The operation of pinging a system is two-way, which is done using the ICMP protocol, this protocol sends a message to the target, and if the message reaches the target, it sends an answer to the sender.
Vulnerability scanning: Vulnerability scanning identifies vulnerable points and computer systems’ security holes. It first identifies the operating system and its version (including service packs) and then finds the vulnerable points in the operating system. Network scanning and vulnerability can usually be detected, and the reason is that the scanner must interact with the target system.
In Mikrotik, you can close the network scanning process and vulnerability by its firewall, which we will discuss later.
Flag definition in the network
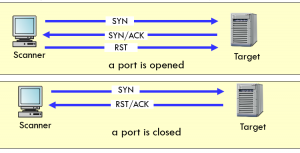
The flag indicates the establishment of communication and the type of communication set in the TCP/IP header, as shown in the image below. The target system sends a response using other flags depending on the type of message received.
Types of TCP flags
SYN: stands for synchronizing, which is used to communicate between systems. For example, handshaking can be mentioned.
FIN: stands for finish and is used to end a connection.
URG stands for urgent and indicates that the data inside this packet must be processed quickly.
RST stands for reset, which is used to restart the connection.
PSH: stands for push and is used to send buffered data.
ACK: Abbreviation of acknowledging is used to acknowledge and receive a message.
Using the komodia packet crafter software, you can create Network customized packages with the desired flag.
The status of ports in the network
Port statuses are usually divided into six general categories:
- Open
- Close package
- Filtered
- Unfiltered
- Open/Filtered
- Close/Filtered
Open ports: It is a port that is actively ready to respond.
Closed ports: A port that is not serviced and is not filtered by the firewall.
Filtered ports: Ports protected by a firewall or some protection devices.
Unfiltered ports: Ports that our scanner (for example, Nmap) can access but cannot detect whether they are open or closed for whatever reason.
Open/filtered ports: An open/filtered port is a port that our scanner (e.g., Nmap) doubts is either filtered or open but cannot accurately determine which state it is.
Closed/Filtered Ports: A port that our scanner (e.g., Nmap) is suspicious of and is sure is either filtered or closed but cannot accurately determine which state it is in.
Types of network scanning with NMAP tool
TCP connect: This scan is the most reliable scan type, meaning the port is open if our connection is established.
Xmas scan: In this type of scanning, URG, FIN, and PSH flags are set so that if the target does not respond, the port is open, and if it responds with rest, the port is closed. This scan does not work on Windows targets.
Syn stealth scan: In this type of scanning, we send messages with the syn flag. If the port is open, the target responds with syn/ack, and if the port is closed, it responds with rest—this scan bypass firewalls and authentication mechanisms, which pretend to be normal network traffic.
Null scan: In this scan, the sent packet does not have any flags, and if no response is sent, the port is closed, and if rust/ack is sent, it means the port is closed. This scan does not work for Windows.
Ack scan: In this scan, the packet is sent with the ack flag. If it is answered with the first answer, the port is not filtered, and if no answer is received, the port is filtered by the firewall. This scan does not work for Windows.
Windows scan: It is the same as ack scan but also works for Windows.
IDLE Scan: In this, you do your work through an interface system, which in terms of security and hacking, this victim system on whose behalf the scan is recorded is called a Zombie.
Each IP packet on the Internet has its Fragment Identification Number or IP ID, which will be the unique identifier of that system or packet. Considering that most of today’s operating systems use the mechanism of increasing the value of the IP ID in sending their information packets, by listening to the PIDs of the victim systems, the number of information packets and time and other such information can be obtained. And in Idle Scan, we use this IPID to scan the interface.
The Zombie system sent an SYN packet to the victim system on the desired port. Depending on the port status of the target computer, it may cause the next IP ID to be added, or it may not need to be added and remain unchanged.
Again, we look for the new IP ID of the Zombie system and register it. To check the port’s status, we compare the new IP ID with the old IP ID and find out the status of the desired port because the victim system has directed the request to the Zombie. This process is repeated from the first step for all desired ports.
Suppose two numbers increase the IP ID number. In that case, the desired port is open because the destination server sent a return information packet to the Zombie system and requested to establish a connection. And if a number is added, the port is closed.
RPC Scan: Windows RPC RPC (Remote Procedure Call) is a protocol used by the Windows operating system. RPC provides a communication mechanism and makes it possible for a program running on a computer to be able to execute code on a remote system. The RPC protocol is derived from the OSF (Open Software Foundation) protocol, and Microsoft has added additional features.
In part of the above protocol, there is a vulnerable point related to the messages exchanged on TCP/IP. The problem is caused by the lack of proper investigation (handling) of incomplete messages. An attacker who exploits the vulnerability can execute code with local system permissions on a vulnerable system. In such a case, the attacker can perform any operation on the system. Examples are installing programs, viewing changes, deleting files, and creating new accounts with all the relevant permissions. An attacker makes a special request on the computer Network remotely and through specific ports to use the existing weakness. Sends RPC.
This scan sends a null RPC message to all found tcp and udp ports and detects if it is an rpc port due to the problem of proper handling of incomplete messages.
Find the target operating system
Banner grabbing: is a method to identify the target operating system, which is done in two ways: passive and active.
Active: In this method, the operating system can be guessed by sending packets to the desired target and their answer.
Passive: In this method, we find the target operating system by sniffing and analyzing information.
In active mode, the operating system can be determined using ping, with the explanation that if ttl=64 and less than 100, it is Linux operating system, if it is between 100 and 200, it is Windows operating system, and if 200 and above (usually 255) It was a router.
Working with Nmap and analyzing its output
Nmap is a very popular and very powerful scanner. This software has a command and illustrated version that we can download and install from the stools site, here, we have Kali Linux installed, which we can easily run in the terminal by writing nmap. Here is a guide for the types of scans by this scanner:
According to the above switches, we can scan the network, an example of commands:
Nmap -f -sV 192.168.10.1 Nmap -vv -f -sV -A In the figure on the next page, we put a photo of the entire help of this scanner taken from nmap's website, which helps a lot to find the needed switches.
- root@kali:~# nmap -f -sV -A -sT 200.1.1.7
- Starting Nmap 7.70 ( https://nmap.org ) at 2018-11-27 00:48 EST
- Nmap scan report for 200.1.1.7
- Host is up (0.00077s latency).
- Not shown: 977 closed ports
- PORT STATE SERVICE VERSION
- 21/tcp open ftp vsftpd 2.3.4
- |_ftp-anon: Anonymous FTP login allowed (FTP code 230)
- | ftp-syst:
- | STAT:
- | FTP server status:
- | Connected to 200.1.1.6
- | Logged in as ftp
- | TYPE: ASCII
- | No session bandwidth limit
- | Session timeout in seconds is 300
- | Control connection is plain text
- | Data connections will be plain text
- | vsFTPd 2.3.4 – secure, fast, stable
- |_End of status
- 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
- | ssh-hostkey:
- | 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
- |_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
- 23/tcp open telnet Linux telnetd
- 25/tcp open smtp Postfix smtpd
- |_smtp-commands: metasploitable.local domain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
- | SSL-cert: Subject: commonName=ubuntu804-base.local domain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
- | Not valid before: 2010-03-17T14:07:45
- |_Not valid after: 2010-04-16T14:07:45
- |_ssl-date: 2018-11-27T05:49:06+00:00; -3s from scanner time.
- | sslv2:
- | SSLv2 supported
- | ciphers:
- | SSL2_DES_64_CBC_WITH_MD5
- | SSL2_RC4_128_WITH_MD5
- | SSL2_DES_192_EDE3_CBC_WITH_MD5
- | SSL2_RC2_128_CBC_WITH_MD5
- | SSL2_RC4_128_EXPORT40_WITH_MD5
- |_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
- 53/tcp open domain ISC BIND 9.4.2
- | dns-nsid:
- |_ version: 9.4.2
- 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
- |_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
- |_http-title: Metasploitable2 – Linux
- 111/tcp open rpcbind 2 (RPC #100000)
- | rpcinfo:
- | program version port/proto service
- | 100000 2 111/tcp rpcbind
- | 100000 2 111/udp rpcbind
- | 100003 2,3,4 2049/tcp nfs
- | 100003 2,3,4 2049/udp nfs
- | 100005 1,2,3 45927/udp mountd
- | 100005 1,2,3 47618/tcp mountd
- | 100021 1,3,4 49629/udp nlockmgr
- | 100021 1,3,4 51431/tcp nlockmgr
- | 100024 1 39978/udp status
- |_ 100024 1 49672/tcp status
- 139/tcp open netbios-ssn Samba smbd 3.X – 4.X (workgroup: WORKGROUP)
- 445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
- 512/tcp open exec netkit-rsh rexecd
- 513/tcp open login?
- 514/tcp open tcpwrapped
- 1099/tcp open java-rmi Java RMI Registry
- 1524/tcp open bindshell Metasploitable root shell
- 2049/tcp open nfs 2-4 (RPC #100003)
- 2121/tcp open ftp ProFTPD 1.3.1
- 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
- | mysql-info:
- | Protocol: 10
- | Version: 5.0.51a-3ubuntu5
- | Thread ID: 12
- | Capabilities flags: 43564
- | Some Capabilities: Support41Auth, LongColumnFlag, Speaks41ProtocolNew, SwitchToSSLAfterHandshake, SupportsCompression, SupportsTransactions, ConnectWithDatabase
- | Status: Autocommit
- |_ Salt: 39`Z$CcJ&!o/9nCCfXg}
- 5432/tcp open postgresql PostgreSQL DB 8.3.0 – 8.3.7
- | ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
- | Not valid before: 2010-03-17T14:07:45
- |_Not valid after: 2010-04-16T14:07:45
- |_ssl-date: 2018-11-27T05:49:06+00:00; -3s from scanner time.
- 5900/tcp open vnc VNC (protocol 3.3)
- | vnc-info:
- | Protocol version: 3.3
- | Security types:
- |_ VNC Authentication (2)
- 6000/tcp open X11 (access denied)
- 6667/tcp open irc UnrealIRCd
- 8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
- |_ajp-methods: Failed to get a valid response for the OPTION request
- 8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
- |_http-favicon: Apache Tomcat
- |_http-server-header: Apache-Coyote/1.1
- |_http-title: Apache Tomcat/5.5
- MAC Address: 00:0C:29:D0:68:98 (VMware)
- No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
- TCP/IP fingerprint:
- OS:SCAN(V=7.70%E=4%D=11/27%OT=21%CT=1%CU=38500%PV=N%DS=1%DC=D%G=Y%M=000C29%
- OS:TM=5BFCDADB%P=x86_64-pc-linux-gnu)SEQ(SP=C9%GCD=1%ISR=CE%TI=Z%CI=Z%II=I%
- OS:TS=7)OPS(O1=M5B4ST11NW5%O2=M5B4ST11NW5%O3=M5B4NNT11NW5%O4=M5B4ST11NW5%O5
- OS:=M5B4ST11NW5%O6=M5B4ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=
- OS:16A0)ECN(R=Y%DF=Y%T=40%W=16D0%O=M5B4NNSNW5%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%
- OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M5B4ST1
- OS:1NW5%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=4
- OS:0%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
- OS:Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=16
- OS:4%UN=0%RIPL=G%RID=G%RIPCK=I%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
- Network Distance: 1 hop
- Service Info: Hosts: localdomain, localhost, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
- Host script results:
- |_clock-skew: mean: 1h39m57s, deviation: 2h53m12s, median: -3s
- |_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
- | smb-os-discovery:
- | OS: Unix (Samba 3.0.20-Debian)
- | NetBIOS computer name:
- | Workgroup: WORKGROUP\x00
- |_ System time: 2018-11-27T00:49:04-05:00
- |_smb2-time: Protocol negotiation failed (SMB2)
- TRACEROUTE
- HOP RTT ADDRESS
- 0.77 ms 200.1.1.7
- OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
- Nmap done: 1 IP address (1 host up) scanned in 33.54 seconds
In line 1, our command is written, which includes tcp connect scan, as well as -f to digest packets to bypass the Linux firewall and sV to find the service and version of the service in open ports and the -A switch to find the operating system. And the version and service ports are open and our target IP is 200.1.1.7.
Line 4 shows the liveness of our host.
Line 5 shows 977 close ports.
In the next lines, it says the port number, its status, the active service on that port, and its version, and further, it says useful explanations about that service. For example, ftp port 21 is open and its version is vsftpd2.3.4, there is no bandwidth control and we can use this service at maximum speed, also because anonymous ftp login is active, we can use it anonymously. and there is no need for any authentication. If we do not use ftp for 300 seconds, our session will be closed, and all the Network information exchanged between us and the server is in plain text, that is, without any encryption and hashing operations, which are exchanged with the help of sniff can easily obtain good information if needed, also by using its version and searching on exploit security sites, download it and run it on this port and service if there is one. Other ports and services can be analyzed in the same way.
Line 96 Mac gives us the other side’s system, which, according to VMware, we understand that our target operating system is virtual in VMware.
In lines 98 to 107, we can understand that the operating system has not been detected correctly and it has given the fingerprint of the operating system, which by searching from this fingerprint, it is possible to find the operating system, but earlier in lines 45, for example, we can understand that the system The agent in front of us is Linux on which Ubuntu services are running and its http header is related to Linux operating systems.
In lines 111 to 119, according to the executed script, the results show that the operating system in front of us is based on Debian, is not in any domain, and is in the form of a workgroup. Also, according to the other party’s system time, you can understand our goal in which country.
In the next lines, he took the traceroute command, which routes he passed to reach the destination, and how he got there. According to the address of those routers, the location can be guessed, and other information can be obtained.
The last line also shows the duration of the scan, and the number of hosts scanned.
Mikrotik scan with Nmap
In this part, we scan the Mikrotik rb951ui-2hnd model router and then make settings on the firewall of this router that block the port scanners.
Well, as you can see, he provided us with information about open and closed ports, as well as the services running on them, among the most dangerous information he provided about us are ports 8000 and 8291, which are used to connect to the router. It is Mikrotik and Mikrotik’s Vibox is highly vulnerable, its default port is 8291. Also, the http service that runs on port 80 has been changed to 8000, which is used in Mikrotik for webfig.
After setting these roles, we run the previous port scanner command and as soon as this command is executed, the Mikrotik firewall detects the port scanner and for 14 days this IP does not have the right to access Mikrotik, and its port scanner is no longer on this Mikrotik does not work and cannot give correct information.
Vulnerability scan
This scan can penetrate the target system and abuse them according to the vulnerabilities and their scanning. One of the most powerful of them is Nessus, which we will continue to work with this software.
Working with nessus
After installing and running this program, we click on new scan and make the desired scan type and other settings and save, now we click on launch and wait until our scan is complete, here we used basic scan and the results are in The figure is below.
Well, here we can see that the scan is complete and 88 vulnerabilities have been found
On the right side of the image, we see several vulnerability models:
Critical: In this type of bug, the attacker can penetrate the system 100%
High: In these types of bugs, there is a very high probability that an attacker can penetrate the system
Normal: In this type of bug, the attacker may be able to penetrate the opposite system
low: In this type of bug, the attacker cannot penetrate, but he can use the obtained information
Info: This item only gives us information about the target that can be read.
Nessus result analysis
In the remediation section, this scanner has told us that we have to do some things such as updating the services, which will solve about 23% of all the problems.
The host section displays the number of vulnerabilities obtained from our desired target.
Now we will analyze the bugs. Due to the large number of them, several types are mentioned here.
Bind shell backdoor detection bug
This bug tells us that our shell listens to a port without any authentication, and the hacker can directly execute commands using this port, considering that this bug is critical, so our target is 100% vulnerable. In the solution section, this scanner offers a solution to change the target operating system if needed. The port used as backdoor is 1524 tcp.
rlogin bug
This service is used to communicate from one Linux or Unix system to another. Its security weakness is that it exchanges information without encryption, and anyone can obtain user and password information by performing MITM or sniffing attacks. Connect these systems through this service. In other words, this service is almost like telnet. The best way to solve this problem is to disable this service and use secure shell or ssh, which exchanges information encrypted using public and private keys. The login service uses tcp port 513, and the minimum task for its security is to change its default port. Another information that can be obtained on this page is that this bug can be exploited using Metasploit (rlogin authentication scanner) and its CVE is also written, which can be obtained with more complete information along with its version which is 1.35.
Nfs exported share information disclosure
This bug is related to the sharing of files, which due to not being properly configured, the hacker can mount these files in his system (these files are shared and accessible at the network level), and for this reason, the files can be can see the reading in full and even if the files have write permissions, make changes in them, the solution to this problem is to configure nfs correctly and only people who are authenticated can access these files to be It uses 2049 udp port and as you can see it is rpc which we talked about earlier and can be exploited using Metasploit (NFS Mount Scanner).
Unix Operating System Unsupported Version Detection
This bug was created because the operating system installed on our target is no longer supported, so any vulnerability found in it will not be patched and will remain usable. The solution is to update this operating system.
In other materials used, we can mention nessus syn scanner, service detection, etc., all of which give us very good information that leads to the exploit of our intended target system. We can read the rest of the bugs in the same way and use the desired information, for example, in other bugs, public and private keys are weakly generated, which can be broken, as well as ssl problems and…
Use of proxies
In the real world, we use proxies to hide our real IP and use a fake IP that cannot easily reach the original person, the most powerful of which is Tor, which uses onion skin technology, before the attack. We must hide our real IP.