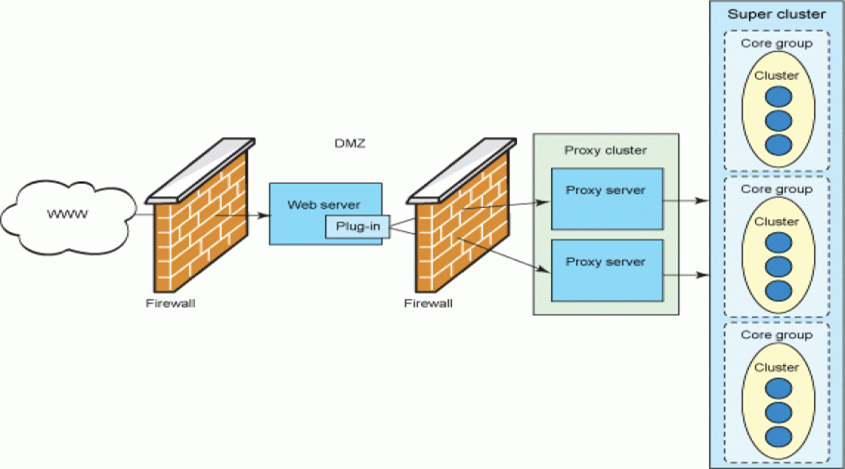
The DMZ on the network allows systems that are accessible to the general public and the Internet to be distinguished from systems that are accessible only to the organization’s users. The DMZ is a communication boundary between two networks that do not trust each other. Since there is no trust in the Internet space, the DMZ structure can be used, which is usually designed by firewalls or proxy servers and placed in different layers of the network. It raises trust in business and external communications.
Introduction
One of the most common uses of a firewall is to grant specific users access to a resource and prevent those outside the group from accessing the resource. Another use of a firewall is to prevent multiple computers from connecting directly to the outside world.
These systems work so that all communications are routed to a firewall through a proxy server, and the same server decides whether a message or a file is safe to pass through the network. This security system is usually a combination of hardware and software. Due to the standards requirements (ISMS & ISO), firewalls have become an integral part of computer networks and a primary concern for network administrators. According to the sensitivity of each organization, the layering and power of firewalls are considered.
What is a Demilitarized Zone?
DMZ stands for Demilitarized Zone and usually refers to a demilitarized zone of the network. It is a communication boundary between two networks that do not trust each other, since there is no trust in the Internet space. The DMZ structure, which is usually designed by firewalls or proxy servers and placed in different layers of the network, can raise trust in business and external communications.
In a simple DMZ structure on a typical network, a server or computer, referred to as the Host, sits in the DMZ environment and receives all the requests from internal users to communicate outside the network.
After receiving these request packages (for example, a website request), the server redirects them to the public network or the Internet. It then sends the response to these requests in the same session created by the internal user. Notably, in this type of simple design, no traffic can enter from the external network to the internal network.
Users on the Internet or an external network can only access the Host used for the DMZ and will not have access to the internal network. Another thing that can be done on this Host is that web pages accessed by the organization on the Internet can be placed there. However, it should be noted that DMZ will not have access to the internal network in this case. Suppose that, in this case, a hacker intends to attack the organization’s website; even if he succeeds in hacking these pages, he will not have access to specific information about the organization’s internal network and private information.
If we want to define DMZ in terms of security, we can also introduce it as an advanced setting in network firewalls. In DMZ settings, most computers on a LAN are located behind a firewall connected to the Internet or a public network.
On the other hand, one or more servers are located after the firewall, i.e., they are not in the internal network. These servers, which are located after the firewall, receive requests from internal users as announced from the internal network. Then they present to the Internet network to which they are connected. This is precisely the intended security concept. In most government agencies and even corporations, there are services that organizations plan to provide offline, such as a corporate website or portal, an email service, a hosting web service, or even a DNS service.
Suppose you put these services inside the internal network and allow users who want to use them to access the internal network from the Internet. This is a security vulnerability, so the general use of DMZ design is always recommended for such services.
In such cases, you place the services and servers you want in the DMZ environment and create a limited connection to the internal network for them, a connection to a very low level and with a lower percentage of risk than regular network communications.
DMZ is designed to protect against attacks that are performed from outside the organization to services, and usually, in this type of design, the risks of the organization’s internal network, such as Spoofing and Sniffing. They are not seen. In addition, we can put services in the DMZ. We put services that need public access in this area of the network.
The most important and famous services that are located in the DMZ section of the network are as follows:
1- Web servers or Web Servers
2- VoIP servers
3- Email servers
4- FTP servers
The critical point is that enterprise web servers are usually not static pages that are just a few, but dynamic pages with a database in the background; these web servers should be able to do this. Use the database, as a rule, and if you put it in the DMZ environment, it would be wrong; in this case, the database is placed either in the internal network and behind the firewall or in a separate network behind a firewall. Put in the same DMZ design. If a hacker infiltrates the website, they can only access the web pages. He cannot attack the data and information in the database behind another firewall.
Email services also have sensitive information and databases that must be protected. We put them behind a separate firewall. Usually, email servers support a Webmail service that can be accessed via the web. You can set your email server behind a DMZ firewall and publish an email webpage for public access through a feature called Publishing.
Email servers must manage both incoming and outgoing email traffic properly. The design of DMZs varies according to the services available on the network, and the DMZ is not a static structure. Due to security and monitoring issues in a business environment, most organizations and companies set up a Proxy Server in their DMZ area. Setting up this server in this environment has several advantages as follows:
- Forcing internal users to use Proxy Servers to access the Internet
- Reduce the need for additional bandwidth on the Internet due to the use of cache in the proxy server
- Centralize the process of filtering websites and web content
- Simplify the recording process and monitor users’ use of the Internet
Suppose the user needs to access the internal network from the outside. Will the DMZ structure allow him to do so? In answer to this question, we must say that a Reverse Proxy enables external users to access the network’s internal resources. Just as a Proxy Server serves internal users, a Reverse Proxy does the opposite—it gives external users internal access.
There are many ways to design a DMZ, and anyone can develop an organization-specific design for their organization according to the existing conditions. In DMZ designs, you can use a single firewall with three network cards or several separate firewalls. How you design a DMZ depends entirely on your organizational needs. Here are two common ways to design a DMZ:
DMZ using a firewall
In this case, you have a hardware or software firewall with at least three network cards, and your DMZ design fits into these three network cards. Your external connection connects to the Internet and the ISP network through the first network card.
Your internal network connects to the existing second network card, and eventually, your DMZ network connects to the third network card on the firewall. Here, our firewall has created a Single Point Of Failure, which means that if this firewall disappears or malfunctions, all the connected networks will have problems.
Also, if there is a lot of traffic between networks, this firewall alone may not be able to provide service, and your network may slow down. Each of these network cards is called a Zone. Purple is commonly used to document this structure for the internal network, green for the DMZ network, and red for the Internet.
DMZ is using two firewalls
Using two firewalls in the DMZ design gives you one of the most secure designs. The first firewall, also called the front-end firewall, is configured to receive and send traffic from the Internet, which first connects to a zone known as the DMZ. The second firewall, called a back-end firewall, is configured to manage incoming and outgoing traffic to the internal network.
Conclusion
Restricting access to internal and organizational networks involves integrated threat management, delegating special authority to a specific group of users to use a resource, and preventing those outside the group from accessing the resource. The Importance of using a firewall to avoid direct connection of the computer to the system and internal organizations.
DMZ can be an essential component of environmental security design to protect the private network. Most government agencies and even corporations intend to provide services outside the network. Using the Da MZ design for such public services is always recommended. There are many ways to design Da MZ, and everyone can have a special design for their organization according to the existing conditions of this method.
FAQ
What is a DMZ in networking?
A DMZ (Demilitarized Zone) is a physical or logical subnetwork that separates a local private network from untrusted external networks, usually the internet. It adds an extra layer of security by isolating public-facing services.
Why is a DMZ used in network security?
A DMZ helps protect internal systems by placing web servers, mail servers, or FTP servers in a separate zone. If these servers are compromised, attackers don’t gain direct access to the internal network.
Is setting up a DMZ at home recommended?
For home users, enabling DMZ on a router can expose a device to the internet without firewall protection, which is risky. It's generally not recommended unless you know the security implications and configure it properly.