In The World Of Computer Networks, A Demilitarized Zone (DMZ) is a logical or physical subnet that provides an organization’s external services in interaction with an unreliable network, such as the Internet.
More precisely, DMZ is a protected network between an unreliable network, such as the Internet, and a secure internal network. The purpose of a DMZ is to add an extra layer of security to the organization’s local area network so that hackers can be directed to a specific point specified by the organization instead of going to different parts of the network.
Most organizations use different technologies, such as firewalls, closed filters, proxy servers, and Inspect Stateful interactions with the DMZ to protect infrastructure more accurately.
Based on this definition, a DMZ is a small and isolated network between the Internet and a private network.
What is a DMZ Network?
Before we explore what DMZ does and what it should implement, it is essential to understand its meaning. DMZ stands for Demilitarized Zone.
While the DMZ does not belong to any enclosed networks, it is unsuitable for military or sensitive operations, as it is always likely to be compromised.
DMZ is a gateway to the public Internet, so it is not as secure as the internal network, but not as insecure as the public Internet.
Hosts within the DMZ are only allowed to have communication channels limited to certain hosts on the internal network because DMZ content is less secure than the internal network.
Similarly, communication between hosts in the DMZ and communication with the external network is restricted to provide more security in the area and allow specific services.
Familiarity with the architecture of the civilian area
To get a more accurate understanding of DMZ, we must first examine the DMZ architecture in the network. There are several ways to design a network with a DMZ pattern.
The two main methods are to use one or two firewalls, although most modern DMZs are designed with two firewalls. The above approach can be extended to implement more complex architectures.
The external network is connected to the firewall at the first network interface by connecting to the public Internet through the Internet Service Provider (ISP).
The internal network is implemented by connecting to the second network interface and the DMZ network, which connects to the third network interface. Figure 1 shows the architecture of a DMZ-based network.
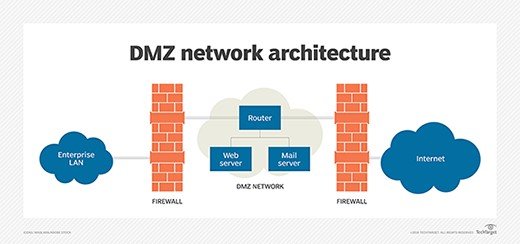
figure 1
Different firewall policies are set up to monitor the traffic exchanged between the Internet and the civilian network, the local and civilian networks, and the local network and the Internet.
They are the Internet, and thus, certain hosts’ connections to the local network are restricted to prevent unwanted connections to the Internet or the local area network. Organizations are implementing a DMZ network between two firewalls to enhance security.
The first firewall, the Perimeter Firewall, is implemented and configured to allow only external traffic to the DMZ destination. The second firewall, an internal firewall, only allows traffic from the DMZ to the internal network.
The above approach provides more security because an attacker must pass through two devices to access the local LAN.
For example, a network intrusion detection system within the DMZ should be configured to block all traffic except HTTPS requests to port 443.
How does a civilian network work?
Civilian networks are implemented to act as a barrier between the public Internet and the private network. Implementing a civilian network between two firewalls means all network input packets are evaluated using a firewall or security policy before reaching the organization’s host servers in the DMZ.
If a hacker can get through the first firewall, he must gain unauthorized access to the services to carry out malicious operations; however, systems based on such networks are prepared to deal with such threats.
However, suppose a hacker can cross the external firewall barrier and control DMZ-hosted systems. In that case, they will still have to go through the internal firewall defense mechanisms to access critical organizational resources.
Why should we use the civilian zone mechanism?
The main advantage of using a DMZ is that it allows cyberspace users to access certain services while creating a secure barrier between users and the private internal network. However, the potential benefits of the civilian area include the following:
Access control for the organization
Organizations can allow users outside the private network to access their various services, whether commercial or non-commercial. This rule governs access to email services such as Gmail.
The DMZ network provides various defense mechanisms to prevent unauthorized users from accessing the private network. In most cases, the civilian area is a proxy server that concentrates internal traffic flow and facilitates traffic monitoring and recording.
Prevent network detection attacks.
Because DMZs act as buffers, they prevent reconnaissance and reconnaissance attacks from succeeding. Even if a system in the DMZ is compromised, the private network is protected by an internal firewall that separates it from the DMZ. In addition, DMZs make it more difficult for hackers to execute network attacks successfully.
When DMZ servers are visible to users, an invisible layer of protection protects them. In such cases, if hackers can seriously challenge servers inside the civilian area, they still do not have access to the private network because a layer of protection protects the civilian area.
Protection against IP address forgery
Sometimes, hackers try to circumvent access controls by forging IP addresses to gain access. In such cases, the civilian area could delay the hackers’ work or, in more advanced cases, allow network services to provide services based on valid IP addresses.
The civilian zone provides a precise mechanism for traffic management by establishing a level of network classification that allows services to be publicly available to users. In contrast, the private network remains entirely secure.
Why is a civilian network used?
Civilian networks are one of the most important mechanisms available to security and network teams. Hackers use civilian networks to separate and keep target systems and internal networks out of reach.
The DMZ mechanism is an outdated way to host corporate resources. It allows organizations to provide users with access while also quickly generating revenue.
Over the past few years, organizations have moved extensively to virtual machines and containers to separate different parts of the network and specific applications from other parts of the organization.
In addition, super-centric technologies have significantly reduced organizations’ reliance on internal web servers.
Take a look at some of the famous and well-known DMZs
Some cloud service providers, such as Microsoft Azure, use a hybrid security architecture in which a DMZ is placed between the organization’s internal and virtual networks.
Such a mechanism is used when external traffic needs to be reviewed or when different traffic control is required between the virtual network and the internal data center.
On the other hand, DMZ works well on home networks where computers and other devices are connected to the Internet via a router and configured on a local area network.
Some home routers support a DMZ, which differs significantly from the DMZ subnet used by organizations because, in an organization, the number of devices connected to the network is typically greater than in a home.
The DMZ hosting capability allows a device on the home network to act as a DMZ outside the firewall, while other parts of the home network remain within the firewall.
Sometimes, a game console is chosen to host the DMZ so the firewall does not interfere with online packet streaming. In addition, a game console is a good option for hosting the DMZ, as it has less sensitive information than a computer.
In addition, the DMZ provides a powerful way to reduce security risks associated with Operational Technology, particularly in cloud applications.
Industrial equipment, such as turbine engines or SCADA systems, has been fully integrated with information technology to make operating environments more innovative and efficient. However, threats have also increased accordingly.
Most Internet-connected operational technology equipment is not designed to manage attacks like conventional network equipment.
Thus, compromising operational technology can allow hackers to more easily enter sensitive parts of a production unit, cause equipment failure, or seriously damage critical infrastructure.
This year (2021), ransomware attacks disrupted parts of US oil pipelines, resulting in the shutdown of refinery equipment and feed injections.
Following the cyber-attack, the shortage of gasoline at gas stations, and rising prices, several drivers in the southeastern United States have begun buying and storing gasoline.
In this regard, the American Automobile Association announced that, due to the gasoline shortage, the average price of gasoline on Tuesday, May 11, 2021, reached $2.98 per gallon, the highest price since November 2014.
Fuel shortages have led to A state of emergency in North Carolina, Virginia, and Florida.
The company’s website was intermittently made inaccessible to prevent hackers from carrying out another attack.
In response, Colonial said the website issue had nothing to do with the cyberattack, but blocked its computer network from communicating with users outside the United States because it feared further attacks.
DMZ is not used between IT and operational technology to enable OSS devices to handle ransomware.
The purpose of using a DMZ is to segment networks and isolate them to reduce damage from hacking attacks. As in the example above, companies do not have to pay millions.
How to install DMZ on servers?
Before you decide to configure a DMZ, determine which services should run on each server. Typically, a DMZ server runs physically and logically on a different part of the network.
This means that a separate server must be used to host services intended for public use, such as the domain name system, web, and email.
Functionally, it is better to implement the civilian area on a different subnet from the local network. To build a civilian area network, you must have a firewall with three network interfaces: one for untrusted networks, one for the civilian area, and one for the internal network.
All servers connected to the external network must be located in the civilian area network, and all servers with sensitive data must be located behind the firewall.
When configuring a firewall, you must place strict restrictions on traffic entering the internal network. Next, NAT must be configured to allow computers on the local network to access the Internet.
In addition, clients must be allowed to connect to DMZ servers.
Figure 2 shows how to set up a civilian area network. To improve security, it is better to use two firewalls. In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker accesses the internal network, he must overcome two security mechanisms.
The three grids represent the DMZ grid architecture with two firewalls. Next, NAT must be configured to allow computers on the local network to access the Internet.
In addition, clients must be allowed to connect to DMZ servers.
Figure 2 shows how to set up a civilian area network. To improve security, two firewalls are better.
In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker accesses the internal network, he must overcome two security mechanisms.
The three grids represent the DMZ grid architecture with two firewalls.
Next, NAT must be configured to allow computers on the local network to access the Internet. In addition, clients must be allowed to connect to DMZ servers. Figure 2 shows how to set up a civilian area network.
To improve security, it is better to use two firewalls. In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker accesses the internal network, he must overcome two security mechanisms. The three grids represent the DMZ grid architecture with two firewalls.
In addition, clients must be allowed to connect to DMZ servers. Figure 2 shows how to set up a civilian area network.
To improve security, it is better to use two firewalls. In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker accesses the internal network, he must overcome two security mechanisms. The three grids represent the DMZ grid architecture with two firewalls.
In addition, clients must be allowed to connect to DMZ servers.
Figure 2 shows how to set up a civilian area network. To improve security, two firewalls are better.
In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker accesses the internal network, he must overcome two security mechanisms.
The three grids represent the DMZ grid architecture with two firewalls. In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker can access the internal network, he must cross the barrier of two security mechanisms.
The grid shows the three architectures of the DMZ grid with two firewalls.
In the above architecture, one firewall allows only DMZ traffic to pass through, while the second firewall allows DMZ traffic to pass through the internal network.
In this case, an additional layer of security is created because if a hacker accesses the internal network, he must overcome two security mechanisms. The grid shows the three architectures of the DMZ grid with two firewalls.
figure 2
Figure 3
For systems within a DMZ network to be more secure and not easily fall victim to hacking attacks, it is best to disable all unnecessary services and domains, run services as chrooted as possible, delete or deactivate user accounts, configure and review reports regularly, and use firewall security policies and anti-IP address counterfeiting capabilities.
FAQ
What is a DMZ network used for?
A DMZ (Demilitarized Zone) network isolates publicly accessible servers (e.g. web, email, FTP) from internal business or private networks — limiting exposure if a public server is compromised.
How do you implement a DMZ network?
Place public servers in a separate subnet or VLAN, configure firewall rules to allow only necessary traffic between the DMZ and internet (and minimal/restricted traffic to internal networks), and ensure strong access controls and monitoring are in place.
Why does a DMZ improve security?
Because even if a public-facing server is breached, the attacker’s access remains confined to the isolated zone — internal systems remain protected behind firewalls.