If your website or app suddenly goes offline due to a massive influx of traffic, it has likely been targeted by a DDoS or Denial-of-Service Attack. These types of cyber attacks are increasing rapidly, and if they occur, they can cause significant damage to a business. What we want to address in this article is getting familiar with DDoS attacks and how to prevent them from occurring. So stay tuned until the end of this article.
What are DDoS attacks?
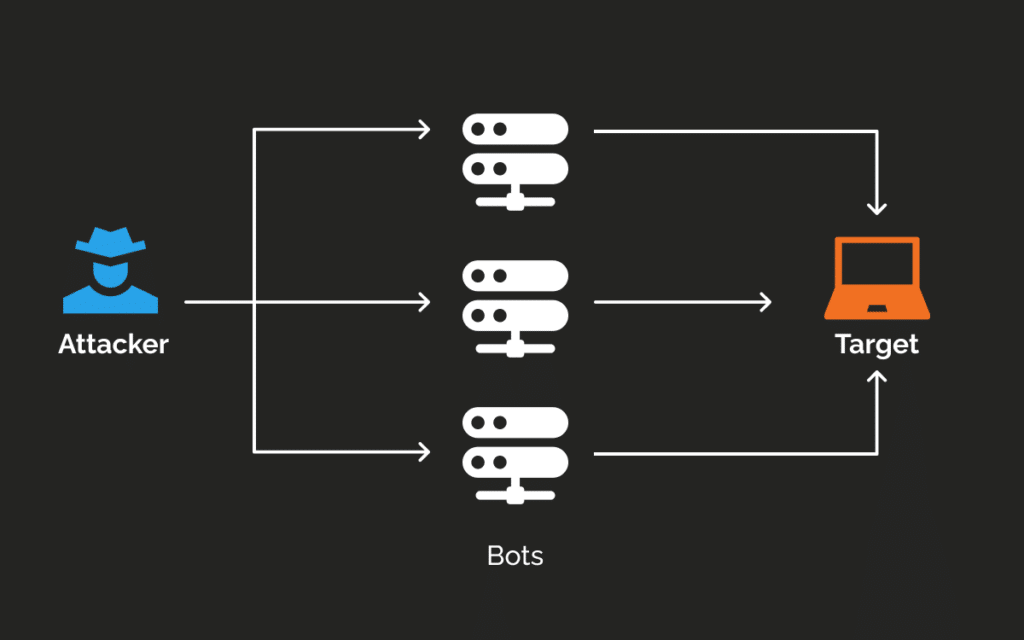
A DDoS attack occurs when a hacker sends a huge flood of traffic to a network or server to disrupt and disable a system. These attacks usually disable or take a website offline temporarily and may last for a few days or more.
Technically, the term “Denial-of-Service” is used for these attacks because the website or server is unable to provide services to legitimate traffic at the time of the attack. The term “Distributed Denial-of-Service” is also used for these attacks because illicit traffic is generated by hundreds, thousands, and sometimes millions of computer systems. Of course, if the traffic is sent from only one source, it is known as a DoS attack.
DDoS attacks use a botnet (a set of computer systems or Internet-connected devices remotely controlled), also called zombies, to send malware to the target computer system.
Types of DDoS attacks
DDoS zombies usually target different layers of the OSI (Open System Interconnection), which, according to Cloudflare statistics, fall into three general categories:
1- Application layer attack
An application layer attack is the simplest and most common form of DDoS attack, mimicking the requests of regular servers. In other words, computer systems or devices in the Botnet come together just like a normal user to access a website or server. However, as the scale of the attack increases, so does the number of seemingly normal requests that the server must process. They are not processed and eventually fail.
2- Protocol attack
In the protocol attack, attackers misuse the server’s data processing resources to try to overload the system, which eventually causes it to crash. Sometimes, botnets send packet data to the server for collection. The server then waits for confirmation from the source’s IP address, which never receives it, but the server continues to receive data.
In a protocol attack, attackers misuse the server’s data processing resources to try to overload the system, which eventually causes it to crash. Sometimes, botnets send packet data to the server for collection. The server then waits for confirmation from the source’s IP address, which never receives it, but the server continues to receive data.
3- Volumetric attacks
Volume attacks are somewhat similar to application attacks, except they are more complex. In this type of DDoS attack, all of a server’s bandwidth is consumed by booted botnets. For example, botnets can sometimes trick the server into sending huge amounts of data; in other words, a server has to re-process the receiving, collecting, and sending operations.
Other methods of DDOS attacks include the following, some of the most important of which are as follows:
- ICMP flood
- SYN flood
- Teardrop attacks
- Low-rate Denial-of-Service attacks
- Peer-to-peer attacks
- Asymmetry of resource utilization in starvation attacks
- Permanent denial-of-service attacks
- Application-level floods
- Nuke
- R-U-Dead-Yet
- Distributed attack
- Reflected / Spoofed attack
- Unintentional denial of service
- Denial-of-Service Level II
ICMP Flood
In this method, the website’s service is disrupted by creating various requests and increasing the ping on the server. Sending a huge volume of ICMP requests in a network will cause all the hosts on that network to respond, thus disrupting all the sites on that network, resulting in a large volume of responses to the access point within the network. It is routed and causes the switch to fail.
teardrop attacks
In this type of attack, by sending a Mangled IP with Overlap, they create a high load volume for the system network card, which generally causes service disruption. This vulnerability is due to a bug in the network and TCP / IP layers. It should be noted that Windows 3.1, 95, and NT operating systems, as well as Linux 2.1.63 and 2.0.32, are quite vulnerable to such attacks. Of course, in 2009, an example of this attack was carried out on Windows Vista, with the difference that this attack was carried out on a higher layer, namely the SMB2 layer. Therefore, updating to new operating systems can prevent this problem and security weakness.
Nuke
One of the oldest attack methods is DDOS, which tries to disrupt and disable the server by sending incorrect ping requests. This attack usually occurs with software such as WinNuke. It uses the weakness of NetBIOS in Windows 95 to attack. This software displays a blue screen in this Windows operating system version by sending a string of information to port 139.
R-U-Dead-Yet
These types of attacks involve sessions that are not being used and are waiting for requests from web applications. Slowloris is the program that keeps most web server sessions open for communication. RUDY also causes the web server to crash by sending requests with bulky headers to these pending sessions.
SYN flood
In SYN attacks, the goal is the handshake process in the TCP protocol. In this type of attack, the part-time attacker abandoned the three-step process of establishing a TCP connection. It causes the target server to wait for the rest of the steps that need to be performed. When the number of requests increases, the server can no longer communicate with new requests and is out of reach!
Who uses DDoS attacks?
Although DDoS attacks are very high in destructive power, almost anyone can perform these attacks in their basic and simple form. Ordinary people can pay for a DDoS attack on the black market or online, or rent a botnet to run their malicious targets.
In general, the following people run DDoS attacks for several specific reasons:
- Business Owners: To beat competitors
- Gamers: To destroy competitors
- Activists: To prevent people from accessing specific content
- Trolls: To take revenge on a person
Who is at risk for DDoS attacks?
Ordinary people should not worry too much about this because DDoS attacks often target large companies. These companies could lose millions of dollars in damage. Of course, smaller businesses also face many difficulties in the event of these attacks. In general, all online organizations should be fully ready to deal with DDoS attacks at any time.
How to prevent DDoS
You can not prevent sending unauthorized traffic to your website servers, but you can prepare yourself in advance to deal with it. To do this, you must do the following:
1- Traffic monitoring
You need to have a good understanding of how low, medium, and high your website traffic is. In fact, you can set a limit to your traffic rate so that it does not exceed the allowable limit. The server will receive the sent requests as soon as it can process them. In addition, regular traffic monitoring helps you quickly identify website traffic issues.
You also need to be ready during certain seasons or advertising campaigns when a lot of traffic is flowing to the website. Sometimes, legitimate traffic that flows from the social network’s viral links to the website can also cause problems similar to DDoS attacks. In other words, even if the traffic comes from a reliable source, it can cause server crashes that ultimately incur irreparable costs.
2- Increase bandwidth
You need to determine the capacity of your website server based on the average and maximum traffic. Of course, you should always consider the bandwidth for the server more than you need. This will give you more time during a DDoS attack before your website, server, or application crashes completely.
3- Use of content distribution network (CDN):
The main purpose of DDoS attacks is to completely overload your web server. So, one of the best ways to deal with this is to distribute website data across multiple servers worldwide.
This is a content distribution network or CDN. The CDN delivers your website data to users from the nearest server. Using multiple servers also makes it easy for the rest of them to continue to work in the event of an overload on one server.
In addition, cloud services such as Cloudflare allow you to protect your website against DDoS attacks by activating an option. The option usually has several basic to advanced levels, so you can select the desired option according to the volume of requests sent.
Important points in case of DDoS attacks
Today, DDoS attacks are very powerful, and it is not possible to confront and eliminate them alone. So, the best way to protect yourself against these attacks is to follow security tips and prevent them. However, if your website crashes due to DDoS attacks, you can restore it to normal by following these steps.
1- Performing defensive measures quickly:
As mentioned earlier, if you know your website’s normal traffic, you can easily detect DDoS attacks. In this case, you will see many web traffic or server requests sent from suspicious sources. With the difference, you have enough time to deal with it before the server is completely down.
Of course, remember that you should specify the server traffic limit and clear the server log history at the first opportunity to free up space.
2- Contact hosting:
Inform your hosting support promptly in the event of a DDoS attack. They can eliminate all incoming requests to the server by creating a Blackhole path until the attack stops. It is to their advantage that otherwise. If your host is for sharing, other customers’ hosting may crash.
Finally, they use a scrubber to separate legitimate traffic from the black hole and to separate legitimate requests from malicious ones.
3- Contacting a network specialist:
If your website has been attacked on a large scale, you should contact a DDoS specialist. They direct your traffic to their massive servers, where they remove malicious and suspicious requests. Of course, hiring a DDoS specialist puts a lot of costs on you.
FAQ
What is a DDoS attack?
A DDoS (Distributed Denial‑of‑Service) attack occurs when multiple compromised devices flood a target resource (like a server, website or network) with malicious traffic from many sources, overwhelming its capacity and causing service disruption.
Why are DDoS attacks dangerous and what damage can they cause?
They can consume bandwidth, CPU and memory resources of a target, leading to slow performance or complete inaccessibility. Consequences include financial losses, damage to brand reputation, and increased recovery costs.
How can organizations prevent or mitigate DDoS attacks?
Effective prevention strategies include using traffic‑filtering services (like CDNs or DDoS mitigation platforms), implementing rate‑limiting and web application firewalls (WAFs), regularly updating and securing devices (including IoT), and preparing an incident response plan to quickly detect and react to unusual traffic patterns.