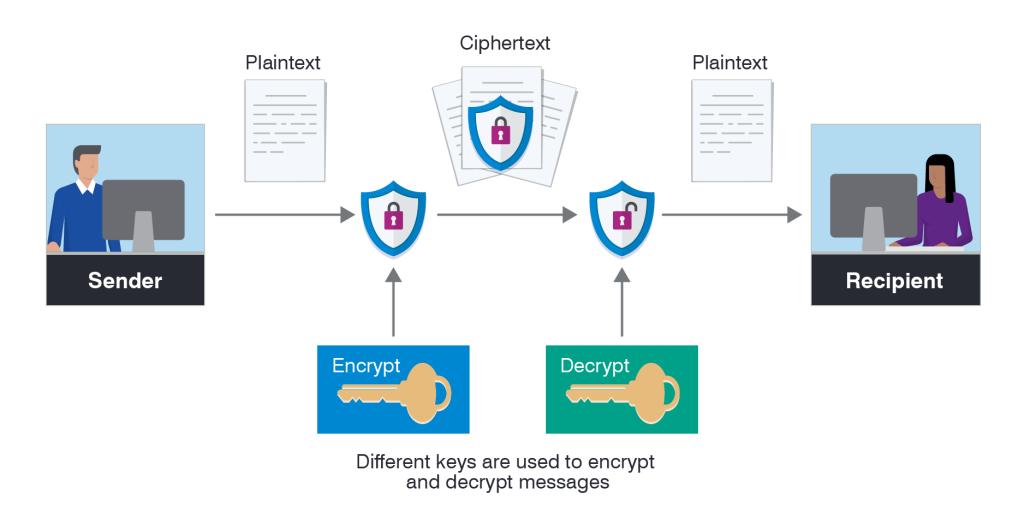
Data Encryption: For Security Plus Testing, Remember That Data From Any Portable Drive Or Mobile Equipment Must Be Encrypted To Maintain Confidentiality. Accordingly, it is important to be familiar with data encryption techniques.
Data encryption
The critical thing is that whenever you store data in memory or a device, you need to check if it’s possible to encrypt that data. Encryption can be implemented in a variety of ways in one system. The following list specifies some popular areas for encrypting information:
Full disk encryption: Today, most operating systems support full disk encryption (FDE). For example, Windows 7 and higher versions have a BitLocker mechanism that allows you to encrypt the entire drive’s contents, including the operating system. To boot the system, a person must know the key to decrypt the boot files.
Database: Encrypting sensitive data is very important when storing information in a database. For example, suppose your Company has an app that keeps a customer’s credit card number or even a customer’s password on the site. In that case, you need to encrypt that data in the database, as hackers can access the database and discover this information if it is not encrypted.
Single files: If you don’t encrypt the content of the entire drive, you can look to encrypt the content of sensitive documents of choice. For example, you can use a file encryption system (EFS) in Windows to encrypt individual files.
Portable Media: If you store data on a portable drive such as a flash drive, encrypt all company data on this drive. Losing or forgetting flash memory in any place is not far from expectation, and if the information is not encrypted, anyone can read the content!
Mobile devices: Most mobile devices allow you to encrypt their contents so that no one can recover your data if it is lost or stolen.
Hardware-based encryption
Software or hardware can perform data encryption (computer chips installed on the system). The advantage of hardware-based encryption is that it serves faster and more efficiently than software solutions. In addition, due to the complexity of computing, organizations use hardware solutions to perform this process faster.
Trusted Platform Module: TPM is a chip placed on the system’s motherboard (it is also possible to install the module separately under certain conditions) and stores the encryption keys used to encrypt data. Apps that use passwords to encrypt data are vulnerable to dictionary attacks. TPM has a dictionary attack prevention module. In Windows, BitLocker supports TPM in saving keys. Keep in mind that the BIOS must support TPM and be active on it.
HSM: Hardware Security Module (HSM) is a card added to a system containing a cryptographic processor to perform asymmetric encryption functions at the hardware level. It also includes chips that store encryption keys for use by the system.
USB and hard drive encryption mechanism: As mentioned, you need to ensure that every portable hard drive and memory, such as USB drives, is encrypted so that unauthorized people cannot access the data.
Note: You need complete information about the TPM chip for the Security Plus test. Also, if you are using TPM to encrypt the drive’s contents, you need a copy of the keys to decrypt the disk’s contents in case the TPM chip or motherboard fails.
Other data security considerations
In the data protection category, there are other considerations that you should pay attention to. Among them are the following:
Cloud storage: If you store information in the cloud, ensure you know your organization’s security policy. Some organizations cannot store data in the cloud due to the sensitive nature of the data.
SAN: Most organizations have a storage space network to keep all their data. Make sure you have time to verify that SAN is configured safely.
Handling Big Data: Make sure that the big data stored in the company’s data is safe, and use secure channels when customers access the network. Big Data is a large dataset used by organizations to analyze and make business decisions.
Data is transferred, and data is at rest: Secure your data in storage space by assigning permissions or encryption, and ensuring data is in transition with encryption. You have also maintained the principle of accuracy and integrity of information as much as possible by limiting the actions that people can take with data in the software.
Other data security considerations
There are several other considerations to consider when running data security, including:
Cloud storage: If you store information in the cloud, ensure you know your organization’s security policy. Some organizations cannot store in the cloud due to the sensitive nature of the data.
SAN: Most organizations have a storage space network to keep all their data. Make sure to take the time to verify that SAN is configured safely.
Handling Big Data: Make sure that Big Data, used to store company data, is safe and uses secure channels when customers can access the network. Big Data is a large dataset used by organizations to analyze and make business decisions.
Data is transmitted, data at rest: In-use data, ensure you secure data in storage space with permissions or encryption, and secure the data being shared with encryption. Also, information is secure by limiting people’s actions with that software.
Implement data-related policies
In the initial numbers of security training, we examined one of the most critical security aspects that every organization should pay attention to, i.e., having a strict security policy and all its dos and don’ts. It is essential to update security policies and prepare a data-related policy that includes:
Erase: Ensure this policy rules that devices be safely erased and that data is permanently erased when no longer used.
Discard: In the policy, be sure to specify how to set aside devices that store data. For example, when switching a hard drive to a system, a reliable method is to physically destroy the hard disk so that no one in the industry can access the information.
Maintain confidence: Ensure your organization has a protection policy determining how long data and records are kept.
Storage: Make sure this policy specifies where data is stored. For example, you may want to state whether flash memory is a valid storage option for company files or whether the Company can use cloud storage.
Data security and privacy practices
There are several ways to protect or delete data. All organizations should implement a data degradation and media cleanup policy to help IT professionals figure out how to remove data from devices such as old hard drives and mobile devices. Below are some options for deleting data to protect the organization’s privacy:
Burning: A simple way to destroy sensitive documents is to burn copies.
Shredding: You can use the document-crushing technique to delete sensitive information. For this purpose, you need a crusher. A document cut by a typical bar shredder allows hackers to combine sections and view data, but a cross-shredding one permanently deletes the information. To eliminate old hard drives, you can buy a particular shredder.
Wiping: You can use specific programs to clean the drive securely, which means overwriting the drive several times to ensure that the data cannot be retrieved.
Note: To test Security Plus, you must be aware of the various available techniques to ensure data confidentiality if you use the device. In highly secure environments, old drives are physically lost, so no one can retrieve the data.
Security of BYOD-related programs and challenges
The hot topic added to the Security Plus certification test is the topic of security practices related to applications and devices (BYOD). In this section, you’ll learn about standard best practices that help you implement a safe environment for apps and let users bring their other equipment to work in compliance with security.
Best ways to secure apps
First, let’s examine some standard best practices for building a safe infrastructure. Although some of these topics have been studied in previous sections, it is essential to investigate them.
Key Management: Make sure sensitive apps use best practices when making encryption keys and keeping keys safe.
Credential Management: Ensure that any security credentials in the app are used securely and stored in an encrypted format in the database.
Authentication: Make sure your app authenticates all users and, based on that authentication, controls what the user can access.
Geotagging: Check if your application uses geotagging features and whether geo-stipulates are stored in files like photos or videos. Geolocation disclosure is one of the significant concerns associated with privacy, as physical location can be determined from this geotag data.
Encryption: Ensure the application encrypts sensitive information in storage space, including network communications and sensitive data.
Allowed Program List: Some sensitive software has an allowlist feature that can be configured in the app. For example, an email program can have an allowlist of contacts and a list of references that are allowed to send emails within the software.
BYOD Security Concerns
One of the significant security concerns these days is that employees bring their devices, such as mobile phones, tablets, and laptops, into the office and use them to perform company tasks. The following shows some concerns about allowing an employee to use a personal device, and these should be taken into account when designing the BYOD policy:
Data ownership: You want to make sure that you formulate and announce information policies if you allow employees to use their devices for work. In addition, you should notify employees that if they leave the Company, tCompanyuld erase all company information from the device.
Device ownership and liability: It is essential to determine who is responsible for supporting the device in case of a problem with the device. Most companies ensure employees know they are accountable for keeping their devices.
Manage patches: Specify who keeps the device up to date with patches. Some organizations delegate this responsibility to the employee tasked with installing the patch on their device whenever it is released.
Antivirus management decides who manages antivirus features. If it is an employee, make sure the employee has antivirus software on the device and keeps the virus database definitions up to date.
Digital evidence: Your BYOD policy should clarify that the Company can complete a criminal identification analysis. Employers and employees may disagree if a security incident occurs with a personal device, so you should not allow them to use personal belongings for work.
Privacy: Another sensitive topic in this area is device owner privacy. You should ask the employee if they will store company data on the device; you can check their device if necessary. Again, the employee may not agree to this, so they should not have access to company data on personal devices.
Onboarding/Offboarding: If you allow personal devices that need access to your systems and network, you must have procedures to add those personal devices to the Identity and Access Management System (IAM) used to identify people. Adding a new device to the network is known as Onboarding, while removing a device from the system is known as offboarding.
Follow corporate policies: Another critical point is ensuring that the employee follows the Company’s Policies regarding personal devices. These may include antivirus management policies, patches, and acceptable use.
User accountability: Ensure the employee agrees to the terms of use of the personal device for work. If they do not agree, you should prohibit the use of the device. Remember that your goal is to protect the interests of the Company
ACompanyture/Infrastructure Considerations: If personal devices are connected to the enterprise network, you must make changes and monitor everything carefully. For example, you may need to install specific certificates on devices or expand the IP range on the DHCP server.
Legal concerns: There are numerous legal concerns about using a personal device commercially. Legal matters include who owns the data, how digital criminology research affects the device, and the privacy of employees who possess the device. Observing these points immunizes the enterprise network.
Acceptable Usage Policy: Ensure the employee agrees to a good use policy when using their device. Typically, employees want to use their devices to bypass the acceptable usage policy.
Device camera: You may need to turn off the camera, so you don’t have to worry about recording footage or photographing the location.
FAQ
Why is encryption important?
It scrambles data so only authorized users with the correct key can read it.
Which encryption types are commonly used?
Symmetric encryption (same key to encrypt/decrypt) and asymmetric encryption (public/private key pair).
Where should encrypted data be used?
For communications, file storage, backups, and any sensitive personal or business data.