Fail2Ban is undoubtedly the best software to secure your Linux server and protect it from automated attacks. When enabled, it provides many configurable rules to ban source addresses that may try to access your device. Fail2Ban works hand in hand with a firewall, so we recommend installing and enabling them as separate layers of security.
In previous posts, we discussed preventing CentOS servers from being hacked with Fail2Ban.
In this article, we explain Fail2Ban and its uses. We will also show you how to install and run Fail2Ban on Ubuntu.
How to install Fail2Ban
1. We recommend updating the system repository and software before installing the new package. Run the following command:
apt-get update && apt-get upgrade
2. Install the Fail2Ban package by running the following command:
apt-get install fail2ban
3. If you want to add email support for the Fail2Ban service, enter the following command and press Enter:
apt-get install sendmail
4. Confirm the installation status of Fail2Ban using the following command:
sudo systemctl status fail2ban
How to set up Fail2Ban
After installing it, consider configuring it. This section will examine how to do this using the jail. Local file.
Fail2Ban has a configuration file called jail. Conf that contains jails – filters with actions. However, users should not modify this file directly as it contains the basic rules for the software.
Instead, please make a copy of the original file and name it jail. Local. Using it, you can customize and set filters and actions like ignore, bedtime, find time, maxretry, and backend. ignore
This feature requires you to specify trusted IP addresses, DNS hosts, or CIDR masks that Fail2Ban should ignore. This parameter allows all traffic to come from specified sources. You can add multiple addresses and separate them with spaces.
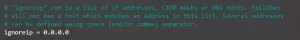
bantime
This parameter determines the length of time a client is banned after a failed authentication. The ban period is measured in seconds, and the default number is 600 or 10 minutes.
find time
This setting determines the time of failed login attempts. If a host fails authentication multiple times (based on the maxretry setting) during the set period, its IP address will be banned.
maxretry
maxretry works in conjunction with find time – it sets the maximum number of failed login attempts in the defined time window. The default value is 5.
backend
This feature allows you to specify the backend configuration for file modification. The default value is auto, but it must be configured if you use CentOS or Fedora.
pynotify – monitors file system changes in real-time and requires a file change monitor to be installed.
gamin – Like pynotify but requires Gamin tool.
polling – uses a polling algorithm that does not require external libraries.
systemd – uses the systemd python library to access the systemd journal.
auto – uses the previous values in this order – pyinotify, gamin and polling.
You can also set additional settings in the jail.local file, including SSH and iptables settings. The available options are:
banaction – Defines which default action to use if the maxretry threshold is reached. If you are using a firewall, set the value to firewallcmd-ipset. However, if you have set UFW as your firewall, change it to ufw.
banaction_allports – Allows you to tag and block IP addresses on any port. If you are using a firewall, set the value to firewallcmd-ipset.
port – The value must match the configured service. If using the default port, change the value to the service name. If you are using a non-traditional port, enter the port number here.
filter – filename located in /etc/fail2ban/filter.d contains failregex information used to parse log files.
Conclusion
Fail2Ban is logging analysis software that helps protect Linux-based web servers from cyber attacks.
In this article, we have shown how to install Fail2Ban on the popular Ubuntu operating system. We also explained how to edit jail.local, the software configuration file. We hope this article helped you set up Fail2Ban on your Linux server. If you have any questions or suggestions, post them in the comments section below.