Organizations Are Very Concerned About Intrusions Into Corporate Networks, And Unfortunately, This Concern Has Now Extended To Home Networks.
Organizations and users employ various mechanisms to secure wireless networks and prevent unauthorized access. However, multiple factors make wireless networks vulnerable to hacking, including weak passwords and misconfigured settings.
Of course, we should not forget the existence of hacking tools that are continually updated to circumvent security controls.
Some users and organizations believe that VPNs can provide robust security for networks. However, some basic steps to secure networks should not be overlooked. Solutions that increase the Security of Wi-Fi networks make it harder for hackers to access them.
Changing the router and network passwords is not a complicated task. You can do so by following simple instructions at different time intervals. Still, before doing so, we must improve our network security information.
Several basic security protocols exist for securing wireless networks, the first of which is WEP.
This protocol has been used by users and security companies for more than two decades as a security mechanism, although it is no longer usable. After WEP, the WPA algorithm was introduced.
The above algorithm performed better than WEP but was eventually replaced by WPA2, the most secure protocol for encrypting Wi-Fi networks.
Note that WPA3 is an alternative to WPA2. However, most routers in use do not support this security feature, and there is still time for a complete replacement of WPA2.
Now that you have a brief overview of cryptographic algorithms, it’s time to discuss ways to secure Wi-Fi networks.
Note that WPA3 is an alternative to WPA2. However, most routers in use do not support this security feature, and there is still time for a complete replacement of WPA2.
Now that you have a brief overview of cryptographic algorithms, it’s time to move on to methods for securing Wi-Fi networks. First, note that WPA3 is an alternative to WPA2. However, most routers in use do not support this security feature, and there is still time for a complete replacement of WPA2.
Now that you have a brief overview of cryptographic algorithms, it’s time to discuss ways to secure Wi-Fi networks.
To Improve The Security Of Wi-Fi Network
1. Go to the modem or router settings page
- In the first step, go to the router settings page. To do this, you must enter the router’s IP address, which is typically http://192.168.1.1. Next, enter the address above in the browser address bar, then enter your username and password in the fields that appear to access the router administration page.
- After opening the settings page, depending on your router, click Wireless Settings and change the password in the Password field.
- On the Wi-Fi settings page, the Security option lets you select the Security algorithm. We recommend choosing the WPA/WPA2 option and the AES algorithm in the Encryption field.
2. Find anonymous connections
If you are in a residential or building complex with several companies around you, you need to identify the devices connected to the router. There are two ways to do this.
First, go to the router settings page or use a device connected to the Wi-Fi network. In the first case, you will see a list of devices connected to the router on the main router settings page after entering the router’s settings. The figure below shows this.
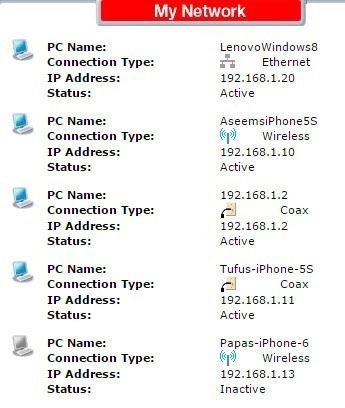
The second method uses the Fing Network Scanner and Net Analyzer Lite software. Fing is available for Android and provides detailed information about devices connected to Wi-Fi networks.
3. Disable the WPS router
We recommend disabling the router’s Wi-Fi feature to maintain network security. WPS vulnerabilities cause most attacks on Wi-Fi networks.
4. Go to filtering McAddresses
It is a good idea to specify the device locations to be connected to the router so that the router can filter out other devices.
5. Use complex passwords
Try to use passwords that are more resistant to pervasive search attacks.
6. Do not worry about hiding the network SSID
Some users think that hiding the network SSID is a way to deter hackers, but doing so will actually encourage them to target the network more.
7. Update the router or modem firmware
The router software, like a computer’s operating system, must be updated. However, unlike computer operating systems, router operating systems do not update automatically; you must manually update the router’s firmware.
8. Change the default IP login to the router admin page
Changing the router’s default address can significantly improve Wi-Fi network Security. To change the modem’s IP address, first, enter the router settings page, go to the Network section, and select the LAN option.
Then enter the desired IP address and click Save to apply the changes. Note that depending on your router, the option to change the IP address may be elsewhere.
9. Activate the router firewall
Some routers are equipped with firewalls that users must activate. For example, D-Link modems offer strong firewall capabilities. Follow the steps below to access the security features of various routers similar to the D-Link router:
First, open the router settings, click the Advanced tab, and select Firewall from the left-hand menu. Then, on the page above, enable the Enable Attack Prevent option to activate the security mechanisms to prevent the attack.
Then, enable the ICMP Echo option. The option above pertains to ping operations. Ping is used to determine network connectivity, but attackers can exploit it to send large volumes of packets. Another important option is Fraggle.
In a Fraggle attack, continuous heavy traffic is sent over a network using UDP, consuming all available bandwidth and router capacity.
Another important field you need to activate is called Echo Charging. Enabling the option above prevents infinite loops.
IP Land prevents successful Layer 4 attacks. In this model, the same sender-and receiver-address attacks are used. A port scan is a technique used by hackers to probe a network for information about all network ports.
TCP Flags prevent attacks that generate heavy, repetitive traffic on networks. Enabling this option will prevent successful TCP DoS attacks or network malfunctions.
10. Use a virtual private network.
A virtual private network is a network in which information is transmitted over a public network, such as the Internet. Still, it remains private through cryptographic algorithms and authentication. It is primarily used to establish connections between different branches of a company or remote activities.
A virtual private network must consider various factors, such as Security, reliability, and work management.
Nevertheless, using a virtual private network offers several benefits for an organization, including expanding the geographical reach of communication, improving Security, reducing operating costs compared to traditional methods such as WAN, and reducing the time remote users spend sending and carrying information.
Improved productivity, simple correlation, and so on. Virtual private networks cost less to implement and operate than leased-line networks. Because of their structure, adding or removing nodes or local area networks in a virtual private network is more cost-effective.
If the private network topology needs to be changed, the network need not be restarted; the network correlation can be updated in software.
FAQ
What steps improve Wi-Fi security?
Use strong passwords, WPA3 encryption, and update router firmware regularly.
How do you prevent unauthorized access?
Disable WPS, change default network names, and restrict device connections.
Why is Wi-Fi network security important?
To protect personal information, prevent intrusions, and ensure safe internet use.