According to the observations and the obtained news, many servers with ESXi virtualizer are now at risk of ESXiArgs ransomware.
This risk exists in all versions 5 and 6. The reason for this security bug is a service called OpenSSL. In the first step, please close the unnecessary ports as soon as possible, limit the main ports to one IP, change all your server’s access information, and back up all the VMs.
The definitive solution to this problem is to install ESXiArgs virtualizer security patches.
To install the ESXI security patch, proceed as follows.
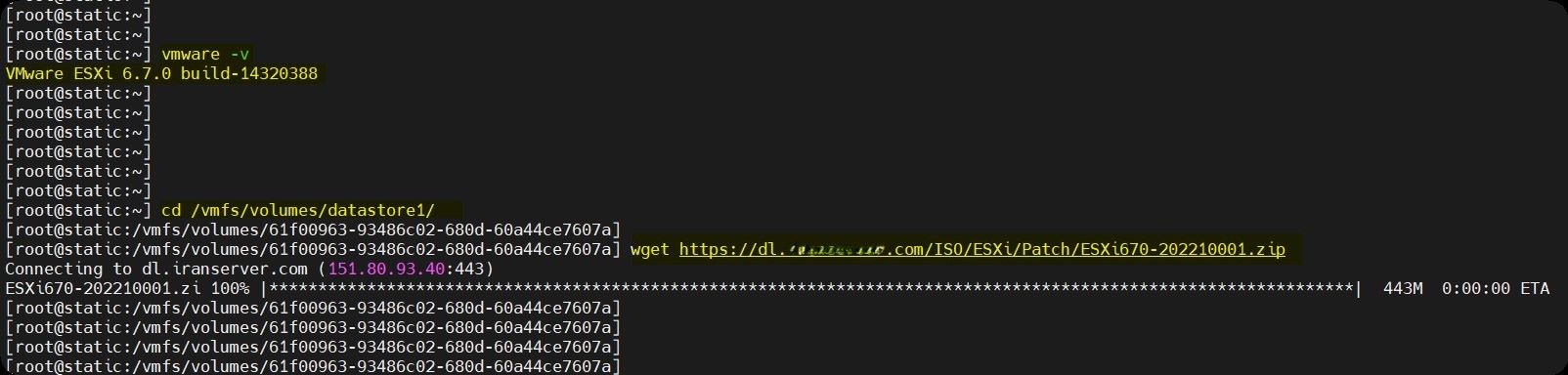
1- Checking the serve@r version to download the required version:
- VMware -v
2 – Temporary SSH activation:
- host > configuration > security profile > services > properties > SSH
- Or, in the new version, enable TSM-SSH in ADS (instead of IP, enter the IP of the server):
- https://YOUR-IP/ui/#/host/manage/services
3- Log in to SSH and enter the following commands:
- Cd/vmfs/volumes/datastore1/
4- According to the installed version, download one of the links:
- wget https://dl.ded9.com/ISO/ESXi/Patch/ESXi670-202210001.zip
- wget https://dl.ded9.com/ISO/ESXi/Patch/ESXi650-202210001.zip
- wget https://dl.ded9.com/ISO/ESXi/Patch/ESXi600-202002001.zip
5- Then install the same downloaded version with the following command:
- esxcli software vib update -d /vmfs/volumes/datastore1/ESXi670-202210001.zip
- esxcli software vib update -d /vmfs/volumes/datastore1/ESXi650-202210001.zip
- esxcli software vib update -d/vmfs/volumes/datastore1/ESXi600-202002001.zip
6- If a successful message is seen in the update, we will reboot the server.
7- After the server is up, you may not have access to SSH. To check the installed version through the web panel, you can check the installed version or activate SSH again according to step 2, and enter the command to check the version entered in step 1. We have to type again to know the correctness of the update.
FAQ
Which ESXi versions are vulnerable to ESXiArgs?
All major ESXi 5.x and 6.x versions are at risk due to the targeted OpenSSL component.
What’s the first step you should take if your ESXi server is at risk?
Immediately close unnecessary ports, restrict access to critical ports by IP, change all server credentials, and back up all virtual machines.
How do you apply the security patch to fix ESXiArgs?
Check your ESXi version with vmware -v. Enable SSH temporarily and log in. Download the correct patch ZIP file for your version. Use esxcli software vib update -d .zip to install it. Reboot the server and recheck the version to confirm the update.