Checking Your Server’s Log Files on Linux and Windows server
Checking Your Server’s Log Files on Linux and Windows server
If you are thinking of using the behind-the-scenes reports of your server to get the necessary information about the server users’ activity and perform troubleshooting with greater accuracy and speed, check the main log files of the Linux and Windows servers can to help you in this way.
Although the programs and sections for checking log files are different in Windows and Linux servers, be sure that each of them provides you with the same level of information:
What is a log file?
A server log file is a simple text report that stores all server-related activities in a certain period. This file is automatically created and maintained by the server itself, and checking the information in this file can help the administrator better understand how users access the website or application. Errors, transactions, and intrusions are among the events that are stored in log files.
The anatomy of the log file is as follows:
Information about the event – user information – date and time of the event
Of course, it also depends on the type of event that covers other data if needed. For example, the servers’ logs include the referred web page, HTTP status code, bytes served, user performance, etc.
Almost everything involved in the website or application server, such as databases, applications, containers, firewalls, services, etc., can generate logs.
When the server performance reports have a lot of variety, then it can be easily said that the server log files are a raw and unfiltered look at the site traffic. Every time a user visits a page of your website, for example, through Google, a new line is added to the log file, which makes checking the log files very useful for administrators because troubleshooting and discovering weaknesses and security risks using these reports can prevent many problems, especially SEO issues.
Checking Windows server log files
Event Viewer is the same tool that is supposed to help you check Windows server log files. The reports of this tool are very useful for checking the performance of programs, the status of updates, and troubleshooting Windows and programs. Also, if you are very satisfied with purchasing a Windows virtual server but you are busy with log-in system reports and user account management, Event Viewer is still by your side. Because the events on your virtual server are checked from both the user and the process side, this information is very useful in troubleshooting services and other security issues.
Event Viewer events are divided into five main types:
Error – when the system cannot work normally, an important problem occurs, shown with the Error tag; For example, the problem of the operating system not responding.
Warning – Non-critical events often indicate potential future problems, such as insufficient disk space.
Information – this type of event is recorded when an application or server is working well, that is, some news about a certain process; For example, correctly loading the network driver.
Success Audit – any event or report related to authorized access attempts is recorded under this title; For example, a successful login attempt.
Failure Audit – These events indicate errors or failures related to access; For example, the inability to access the network driver.
How to use Event Viewer on Windows Server
Open Server Manager and run the Event Viewer program from the tools tab.
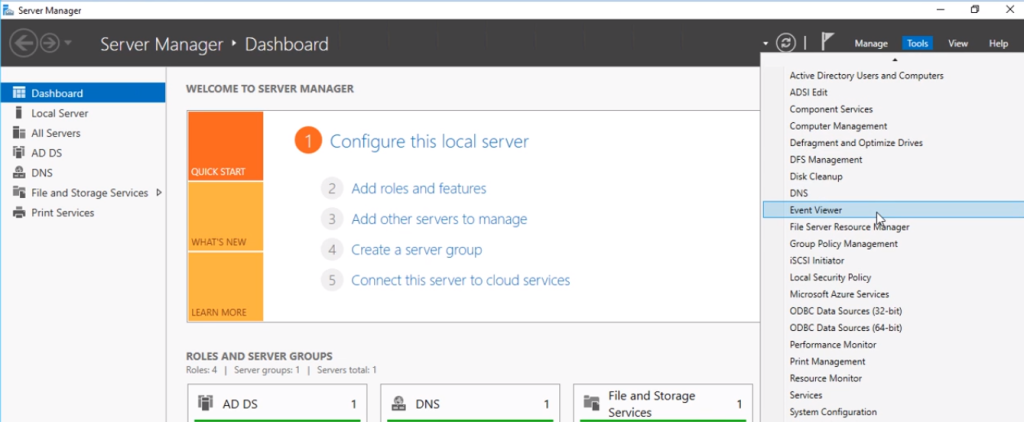
(Or from the Start section, search for Event Viewer and run it).
All Windows server log files are divided into four categories: Custom View, Windows logs, Applications and services logs, and Subscriptions.
To get more information about the desired event, click on it and look at the bottom.
Custom Views
This section is included to display your favorite alerts. For example, if you want to see if a certain part of the system is broken, you can create a Custom View related to this issue so that any warning related to system failure is placed in this section. Considering that the warnings related to the server are mostly too many and checking all of them can be time-consuming, using Custom Views is very useful.
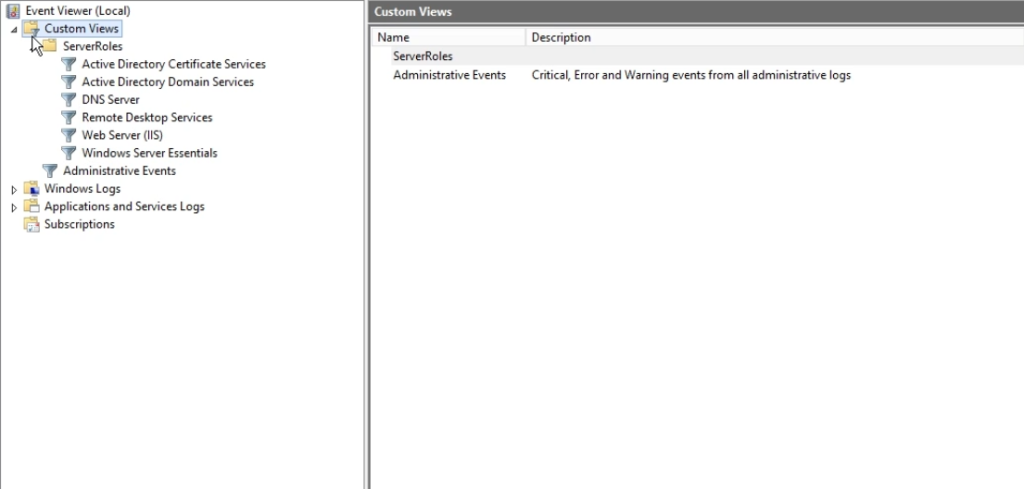
Of course, the Administrator Events option is located in the Custom Views section by default. Various management reports such as application, security, system, and hardware are placed in this section.
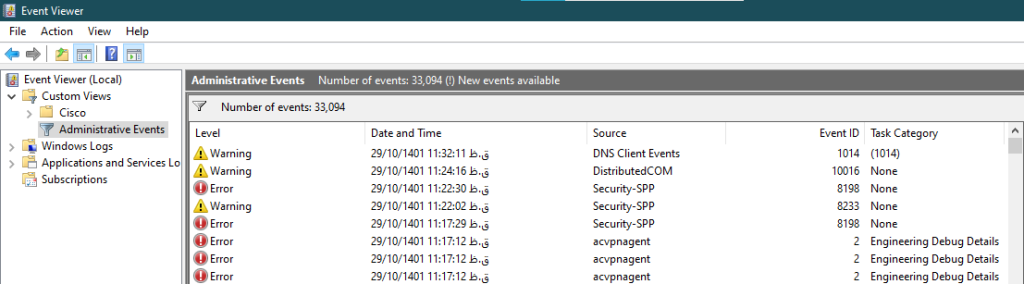
Windows Logs
This is the main part of the Event Viewer, which shows important events in 4 main categories:
Application – These reports are related to drivers and applications hosted on Windows Server. For example, the PowerPoint launch error is placed in the application log.
Security – Security reports contain events related to system security. These events are logged through the Windows event tracking and analysis process. User login and log-out reports are one of the most important ones because, with timely monitoring, any attack and hacking can be prevented.
Setup – These events are related to the installation process of the Windows operating system. Active Directory reports are also stored in this section if the server is a domain controller type.
System – This section includes reports related to the system and its components. Boot driver loading error is one of the most important system-level events.
Forwarded Events – This section contains events sent by other systems on the same network.
Applications and Services
All events related to applications you use on a Windows desktop or server ard in this section. For example, the related log is in this section if there is a problem in running word.
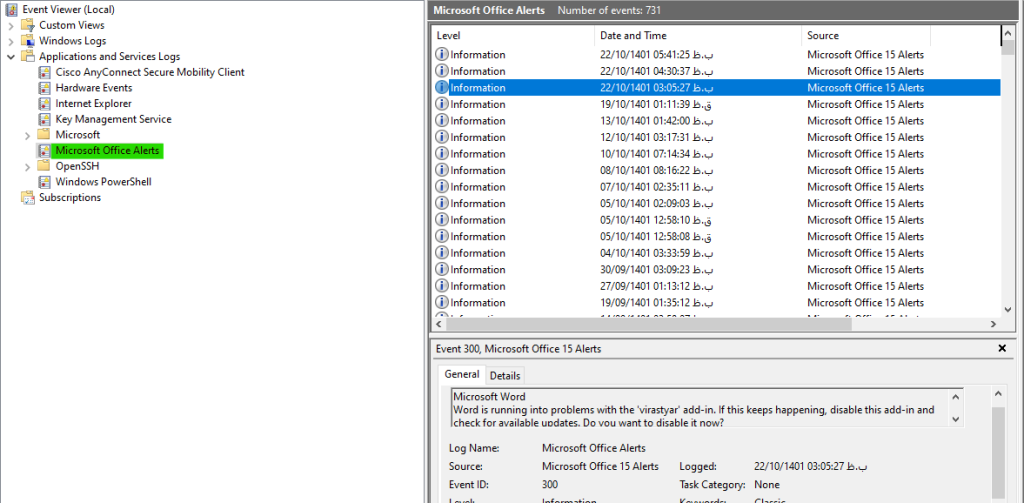
Now you might wonder what the difference is between the previous application log and this one.
The previous log application, located in the Windows Log section, only shows events from running programs. While the Applications and Services section stores events in an ordered and categorized manner. For example, if you open the Windows folder in the Microsoft section, all related events are placed in a folder that you can open and access all of its events.
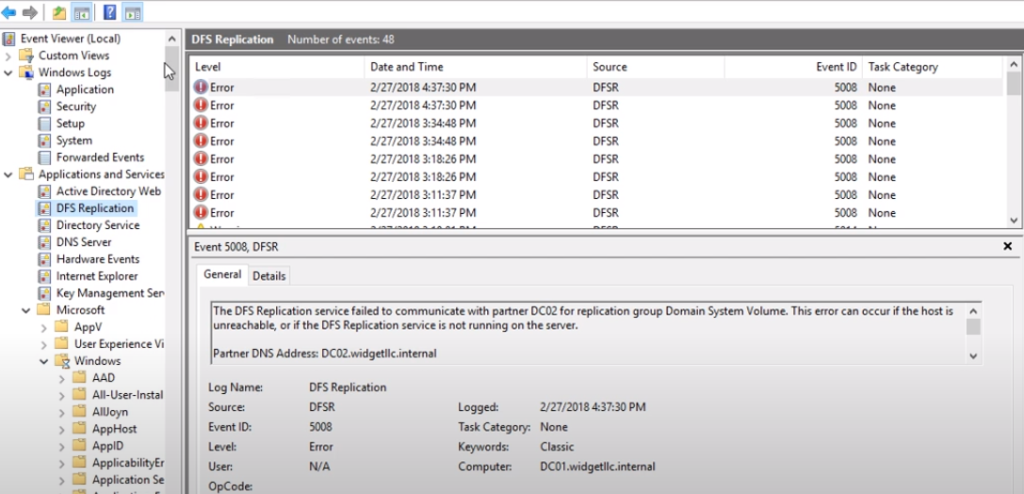
For example, the logs related to the remote desktop are located in the following section:
In general, if you encounter any errors when opening Event Viewer, don’t worry because these errors can happen even when your system is working fine.
If an error has caused the server problem and you have identified that error using the Event Viewer log files, you can find the solution by searching for the event title or ID.
Check Linux server log files.
Like the Windows server, the Linux server has a special section to store the events related to the operating system, programs, and services. These log files are very useful for analyzing problems by administrators. Especially if you plan to start your website or application by purchasing a Linux virtual server, later you will need reports on user logins and exits, access requests, etc., and checking the Linux server log files can make it easier for you. slow down
Linux log files are stored in plain text and can all be found in the var/log directory. So with a simple cd command, you can access the log files, but you must be a root user.
Usually, the log files generated in the Linux environment are divided into four different categories:
- Application Logs
- Event Logs
- Service Logs
- System Logs
The most important Linux log files that must be monitored are!
//var/log/syslog or var/log/messages/
These log files contain messages or information about the system that covers all general activities. Non-kernel boot errors, program-related service errors, and system boot process messages are located in this path.
Debian-based systems – Syslog
Systems based on red hat-messages
var/log/auth.log/ or var/log/secure/
Authentication log files are stored in this path. Successful login failed login and authentication methods are the main contents of these reports. So, this section is located in any security breach, brute-force attacks, suspicious files, and any error related to the user authorization mechanism.
Debian-based systems – auth.log
Systems based on Red Hat-secure
var/log/yum.log/ or var/log/dnf.log/
Log files related to installing, updating, or removing packages are stored in this file by the yum or dnf package manager. So checking these log files is very useful for tracking software package installation status and installation problems. For example, let’s say your server has been down for some reason, and you have doubts about the latest software you installed. This is when you can check this log file to identify the malicious software.
var/log/mysqld.log/ or var/log/mysql.log/
This log file contains all the messages related to the MySQL service’s debugging process, success, or error. So checking these logs is very useful for identifying problems starting, running, or stopping myself, getting more information about client connections to the MySQL data directory, and setting the long_query_time parameter.
var/log/maillog/ or var/log/mail.log/
As the name suggests, all the reports related to the email server are stored in this path. So if you need information about postfix, smtpd, or email-related services, the information in this log file is very useful for you.
Tracking all sent and received emails in a certain period, checking email delivery problems, discovering possible spam attempts, etc., are among the most important things you can do using this log file.
var/log/boot.log/
This file is the repository of all the information related to the boot process and server startup. So, errors related to turning on/off the system, failed boot, and restart are in this section.
var/log/dmesg/
This section places log files related to hardware devices, systems, or Linux server drivers. So, by using it, you can track information about device status, hardware errors, and related general messages. This log file is more useful for dedicated servers.
var/log/kern/
As it is clear from its name, information and reports related to the system kernel are placed in this path. The kernel records these log files, so they are very important. These log files are ideal for troubleshooting hardware, connectivity, and kernel warnings.
var/log/faillog/
All reports of failed login attempts are placed in this path. Therefore, using them can identify security violations such as username/password hacking and attacks such as brute force.
var/log/cron/
All messages related to Crond (cron jobs) are stored in this section. Every time a border is executed, the reports of successful execution or execution error are placed under the format of a new log file in this path.
var/log/httpd/
This file contains all the logs recorded by the Apache server. Apache server login information is stored in two separate files, error_log and access_log.
error_log is the repository of all messages related to httpd errors, the main ones being memory problems and problems related to processing httpd requests.
access_log also stores all access requests received via HTTP and helps you monitor every page opened and every file loaded by Apache.
IP address, client IDs, information about the status of requests, and their results are among the most important contents of this log file.
How to access Linux log files
There are two ways to view Linux server events. The first is to use basic Linux commands, and the second is to run the Linux file system log program.
View Linux server events with commands
Open the terminal and go to the following path: (Of course, you must be a root user to execute these commands)
cd /var/log
Open the list of all log files with the following command:
ls
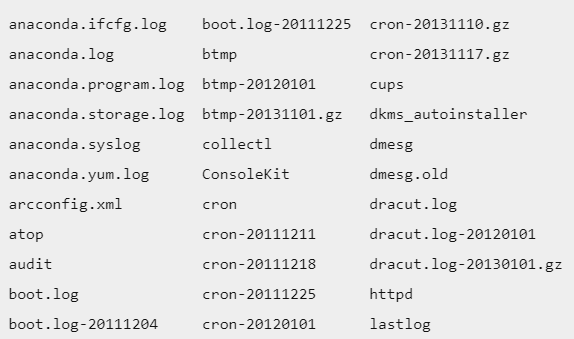
To open a specific log file, you can use one of the following commands:
For example, failing:
less /var/log/faillog
more -f /var/log/faillog
Cat/var/log/failing
tail -f /var/log/faillog
grep -i error /var/log/faillog
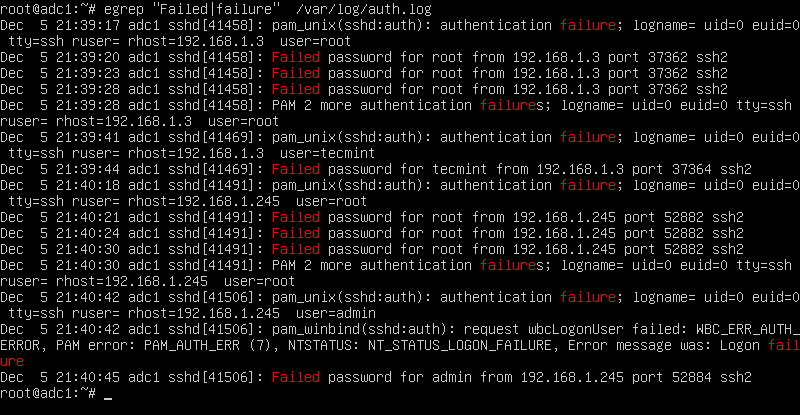
The output of each of these commands will provide you with reports of failed login attempts in a simple format that you can use to view the date and type of user action in detail.
View Linux server events with GUI
System Log Viewer in Linux is the same as Event Viewer in Windows, which is used to view and monitor server or system events.
To open this tool, click on the system menu and choose System Log from the Choose Administration section.
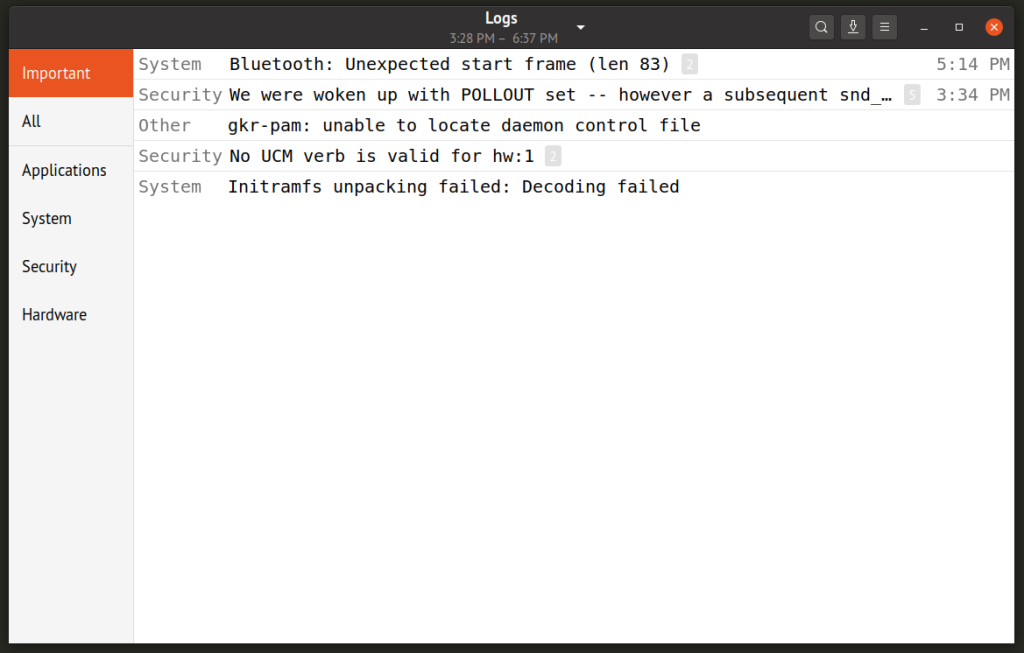
This program presents all the events in a categorized manner so you can refer to the desired section and use their information according to your needs.
Conclusion
Examining Linux and Windows server log files will help you quickly identify errors and take action if necessary. Windows server administrators use the famous Event Viewer tool for this purpose, and Linux administrators can use System Log Viewer commands or a graphical interface, which, of course, most Linux users find using commands easier and more useful.
Thank you for staying with us until the end of the article. We hope that reading this article was useful for you. If you have any questions or requests and need guidance, you can contact us by registering your opinion so that we can answer you as soon as possible.











